Versions Compared
| Version | Old Version 4 | New Version Current |
|---|---|---|
| Changes made by | ||
| Saved on |
Key
- This line was added.
- This line was removed.
- Formatting was changed.
Home / User Provisioning and Identity Lifecycle / Provisioning Policies / Current: Creating a Provisioning Policy for Office 365 Accounts
In EmpowerID, Provisioning policies, also known as "Resource Entitlements" or "RETS," are policies that can be created to automate the provisioning, moving, disabling and de-provisioning of resources to users based on certain qualifying criteria, such as belonging to a specific group, Management Role, Business Role and Location, or Query-Based Collection. Once a policy is created and enabled, EmpowerID continuously evaluates the policy to determine who should and should not have the resource specified by the policy.
| Info | ||
|---|---|---|
| ||
|
This topic demonstrates how to create a RET policy that automates the provisioning and de-provisioning of Office 365 accounts and is divided into the following activities:
- Creating a provisioning policy for an Office 365 user account
Assigning the provisioning policy to a specific target.
In this topic we assign the provisioning policy to the Self-Service User Limited Access Management Role. In this way, anyone who is a member of the Management Role will receive an Office 365 account.Info Management Roles are just one of the possible targets for a provisioning policy. These policies can also be targeted against any number or combination of groups, Business Roles and Locations, Query-Based collections, as well as individual people. Although we target the policy against a Management Role in this topic, you can apply the procedures against any target(s).
- Approving the pending Office 365 account.
- Verifying the policy created a new licensed user in Office 365.
To create a provisioning policy that provisions Office 365 user accounts
- In the Navigation Sidebar of the EmpowerID Web interface, expand Admin, then Policies, and click Provisioning Policies (RETS).
- From the Provisioning Policies management page, click the Actions tab and then click the Create Provisioning Policy tile.
 Image Removed
Image Removed Image Added
Image Added - In the Choose Type section of the Policy Details form that appears, select Office 365 Account from the Object Type To Provision drop-down.
 Image Removed
Image Removed Image Added
Image Added - In the General section of the form, do the following:
- Type a name, display name and description for the policy in the Name, Display Name and Description fields, respectively.
- Select Exchange Mailbox from the Resource Type drop-down.
- Leave the first Depends on Resource Type drop-down empty.
- Select your Office 365 account store from the Resource System drop-down.
- Select your Office 365 account store from the Depends on Resource System drop-down.
- Specify the email suffix to be given to anyone receiving the resource entitlement by typing that value in the Email Suffix field. This suffix must be the suffix for the Office 365 domain you federated with EmpowerID.
Once you have completed the above, the General section of the form should look similar to the image below.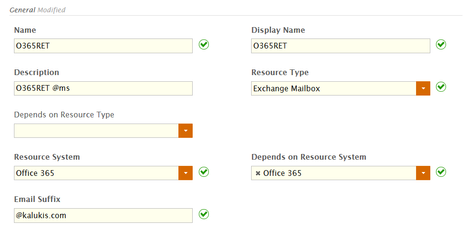 Image Removed
Image Removed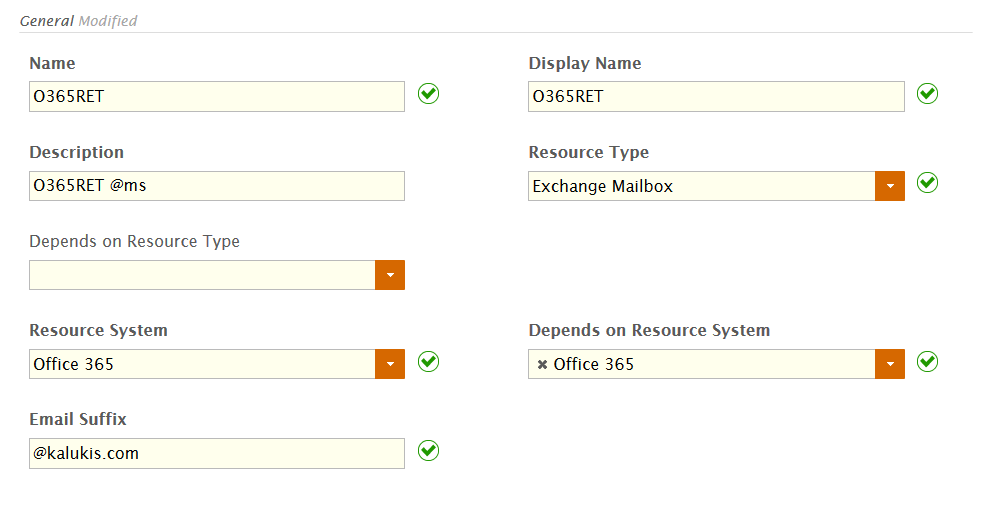 Image Added
Image Added
- In the Throttling Settings section of the form, specify the provisioning and deprovisioning thresholds for the policy. These settings are as follows:
- Approve All Provisions - If this option is selected, the provisioning of each RET specified by the policy will need to be approved by a user delegated access to the Resource Entitlement Inbox.
- Approve All Deprovisions - If this option is selected, the deprovisioning of each RET specified by the policy will need to be approved by a user delegated access to the Resource Entitlement Inbox.
- Require Approval if Provision Batch Larger Than Threshold - This field allows you to set a numeric value that needs to be reached by a single run of the Resource Entitlement Inbox before an approver needs to approve the provisions. If the threshold is reached, EmpowerID will not provision any of the accounts until approval is granted.
- Require Approval if Deprovision Batch Larger Than Threshold - This field allows you to set a numeric value that needs to be reached by a single run of the Resource Entitlement Inbox before an approver needs to approve the deprovisions. If the threshold is reached, EmpowerID will not deprovision any of the accounts until approval is granted.
In our example, we have selected Approve All Provisions and Approve All Deprovisions, meaning that the provisioning and deprovisioning of all Office 365 accounts must be approved before those folders will be processed by RET Inbox.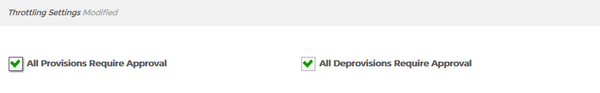 Image Removed
Image Removed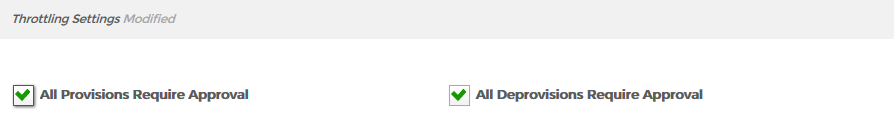 Image Added
Image Added
- In the Advanced section of the form, do the following:
- Select Do Nothing from the On Claim Action drop-down.
This tells EmpowerID to simply mark any previous resources assigned to the user that match this policy as RET-managed resources. For example, if the user already has an Office 365 account and is placed in a Management Role targeted by the RET policy, EmpowerID marks that user's Office 365 account as RET managed. - Select Do Nothing from the On Transform Action drop-down.
This tells EmpowerID to simply mark this resource with the new RET policy number. - Select Deprovision from the On Revoke Action drop-down.
This tells EmpowerID to delete the Office 365 account if the person no longer meets the criteria to receive the resource from the RET, such as would occur if the person was terminated or removed from a qualifying Management Role, group, Business Role and Location or Query-Based Collection. - Leave the Custom Workflow to Run On Claim, Custom Workflow to Run On Transform, and Custom Workflow to Run On Revoke fields empty.
- Leave the Creation Location Path Resolver Assembly and Creation Location Path Resolver Type fields empty.
The Advanced section of the form should now look like the following image: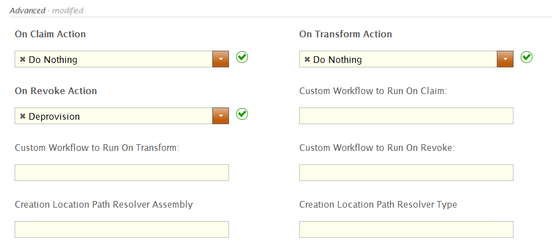 Image Removed
Image Removed Image Added
Image Added
- Select Do Nothing from the On Claim Action drop-down.
- Back in the main form, click Save.
Next, assign the policy you just created to one or more targets as demonstrated below.
To assign the Office 365 RET policy to a target
- Scroll to the Policy Assigned To section of the Policy Details form and click the Add (+) button underneath the specific target type to which you want to assign the RET.
In our example, we are assigning the policy to the Contractor in All Business Locations Business Role and Location so we are clicking the Add (+) button in the Business Role and Locations pane of the section. In this way, each Person who has the Contractor Business Role in any location will receive an Office 365 account.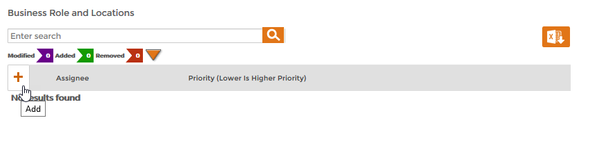 Image Removed
Image Removed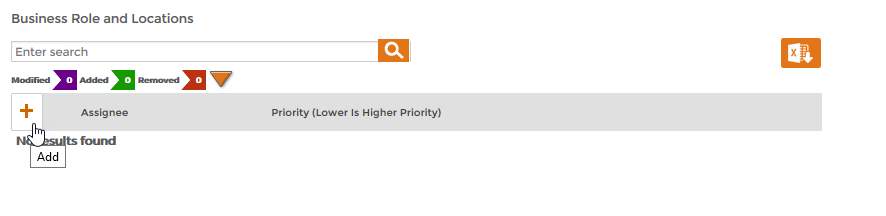 Image Added
Image Added
This opens the Add Entry pane, which is where you select the specific actor you want to assign the policy to. Because we are assigning the policy to a Business Role and Location, the Add Entry pane is contextualized for that actor type.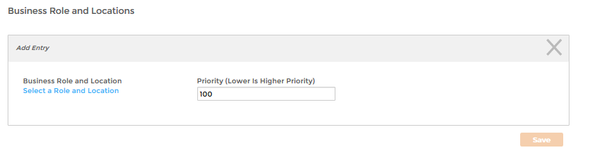 Image Removed
Image Removed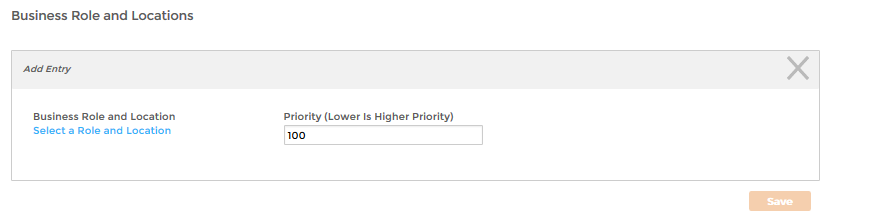 Image Added
Image Added - From the Add Entry pane, click the Select a Role and Location link.
- In the Business Role and Location selector that appears, do the following:
- Search for and select the Business Role to which you want to assign the policy. In our example, we are assigning the policy to the Contractor Business Role, so we have selected Contractor.
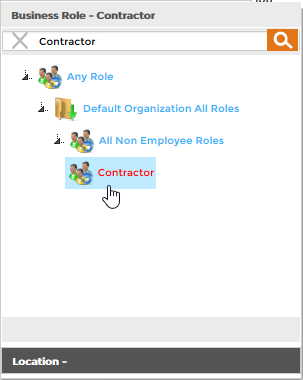
- Click the Location tab and then search for and select the Location. In our example, we want the policy to be applied to all contractors regardless of their location, so we have selected All Business Locations.
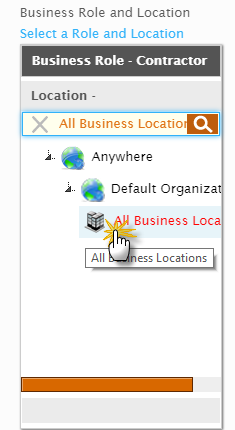 Image Removed
Image Removed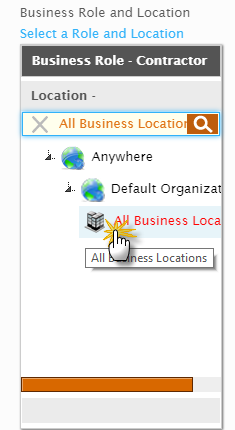 Image Added
Image Added
- Search for and select the Business Role to which you want to assign the policy. In our example, we are assigning the policy to the Contractor Business Role, so we have selected Contractor.
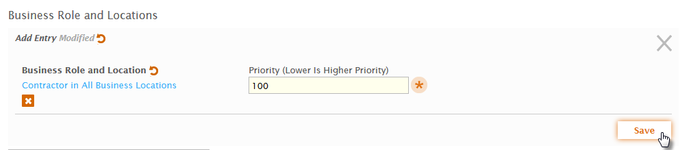
- Click Select to close the Business Role and Location selector.
- Type a number to specify the priority for the RET policy in the Priority field.
This value is used to determine the priority of the RET if the user qualifies for the same RET by virtue of another assignment, such as being a member of a group that has the same policy. - Click Save.
- Back in the main form, click Save.
If you selected Approve All Provisions, you must manually approve each item in the Resource Entitlement Inbox for this policy before EmpowerID will provision the user accounts. This is demonstrated in the next section.
To approve the pending accounts
- From the Navigation Sidebar, expand System Logs and click RET Inbox.
Click the Pending Approval tab to see a list of all RETs requiring approval.
infoIn the following image, the Navigation Sidebar has been collapsed to conserve screen real estate.
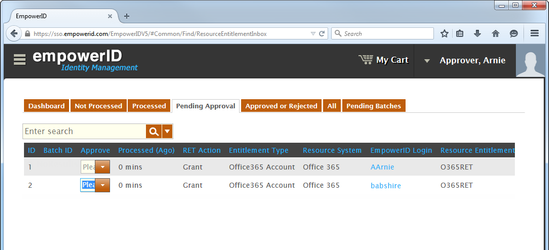
- To approve a RET, click the Approval drop-down and select Approve from the menu.
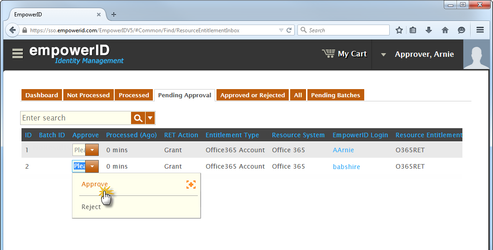
This adds the approval to your shopping cart.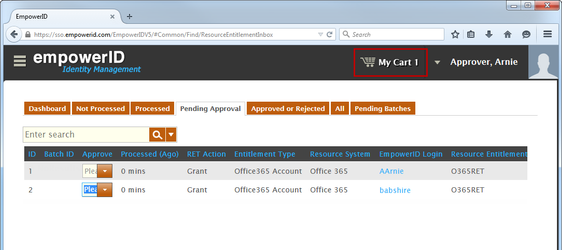 Image Removed
Image Removed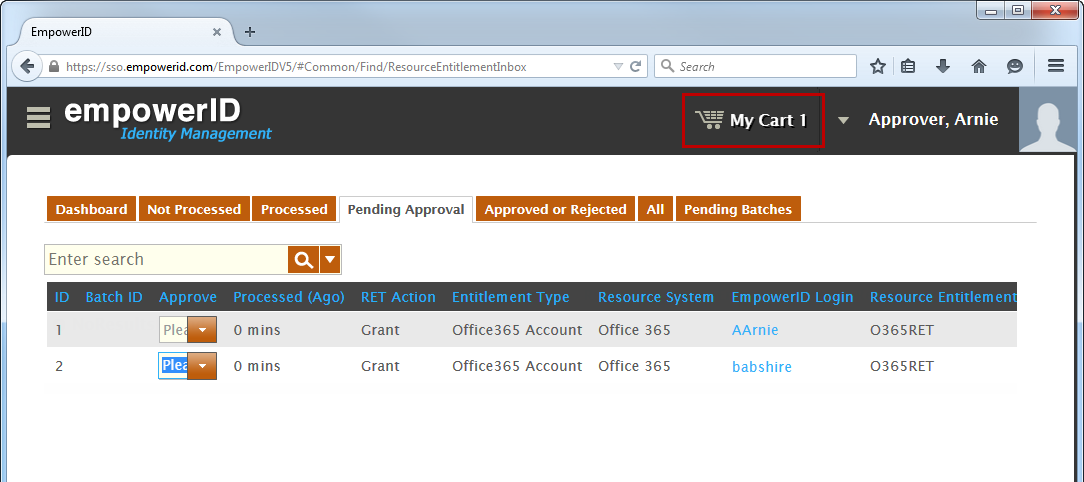 Image Added
Image Added - Repeat for each RET you want to approve.
- When finished adding approvals to your cart, click the cart, type a reason for the approval in the cart dialogue and then click Submit.
- Wait several seconds for RET Inbox to process the approval and then click the Processed tab to see an entry with a RET Action of Grant for the Office 365 user account.
 Image Removed
Image Removed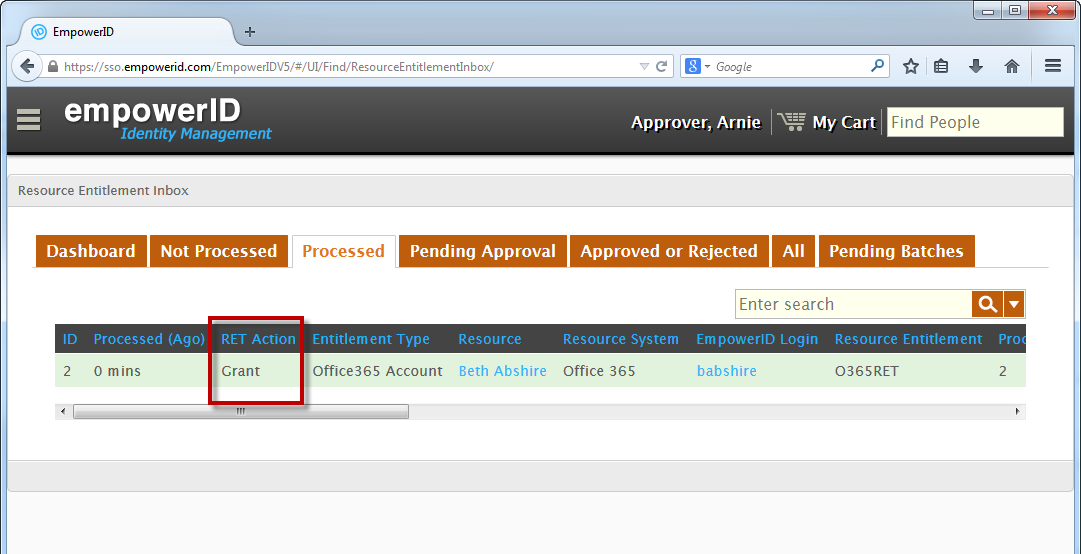 Image Added
Image Added
To verify the RET policy provisioned new licensed users in Office 365
- From your Web browser log in to your corporate Office 365 account as an administrator.
- From the Office 365 admin center, click users and groups and search for the user whose account you just approved.
 Image Removed
Image Removed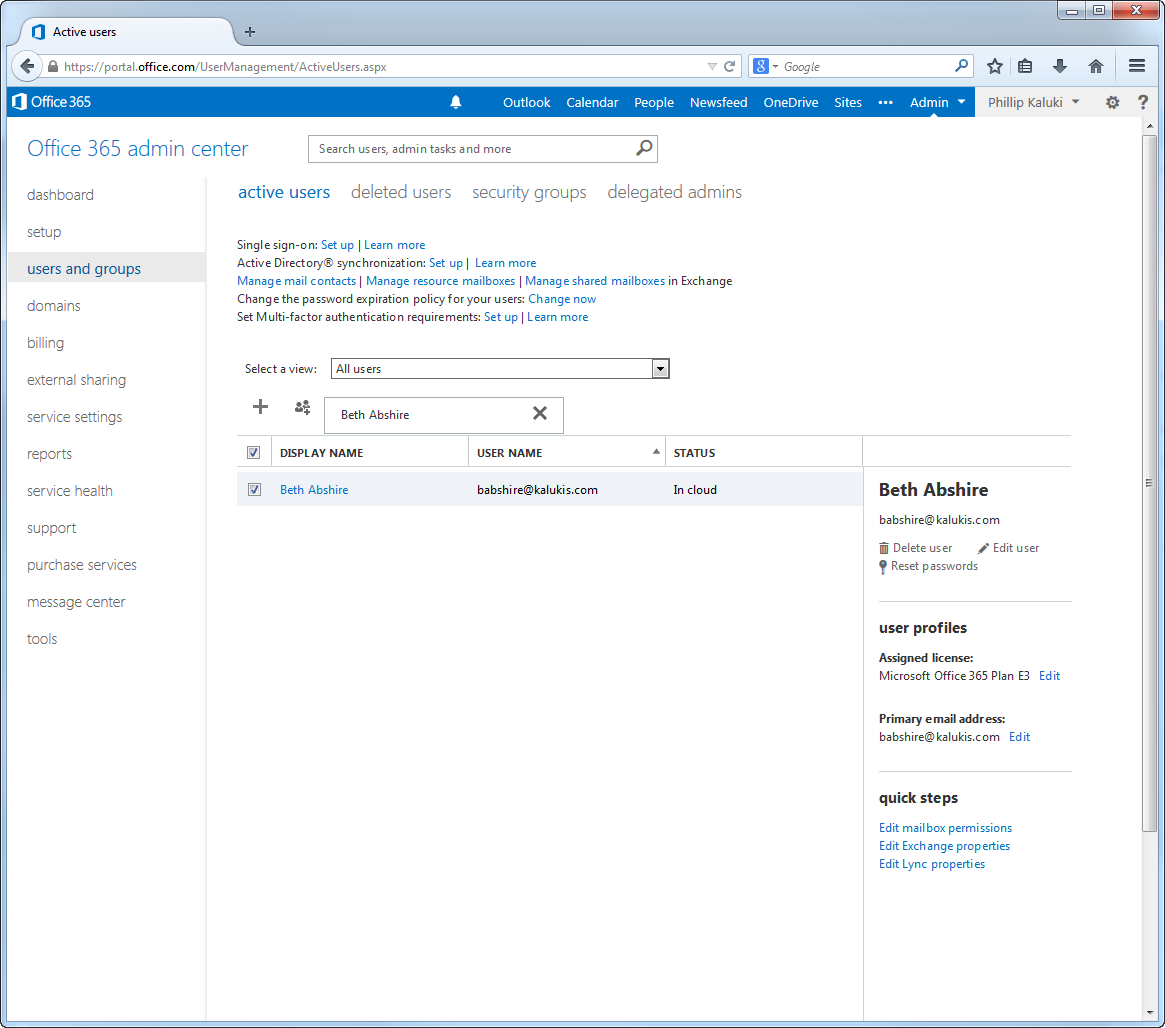 Image Added
Image Added - Click the link for the specified user to navigate to that user's page and verify the information therein, including the licensing information. You should see that the user has all the licenses pertinent to the Office 365 subscription.
| Info | ||||
|---|---|---|---|---|
| ||||
| Div | ||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ||||||||||||||||||||||
|