Versions Compared
| Version | Old Version 10 | New Version Current |
|---|---|---|
| Changes made by | ||
| Saved on |
Key
- This line was added.
- This line was removed.
- Formatting was changed.
| Div |
|---|
Home / Installation and Configuration Guide / Configuring EmpowerID / Connecting to Directory Systems / SharePoint / Current: Federating SharePoint with EmpowerID |
In an environment with Microsoft SharePoint, you can configure EmpowerID as a claims-based authentication provider for your SharePoint farm. Using EmpowerID in this way allows you to extend EmpowerID's RBAC model to your corporate SharePoint environment, giving you greater flexibility and control over how you assign user's access. Before configuring EmpowerID as a SharePoint claims provider, the following prerequisites must be met:
| Info | ||||||
|---|---|---|---|---|---|---|
| ||||||
|
Once you have met the above prerequisites, you can configure the federated trust between EmpowerID and your SharePoint farm.
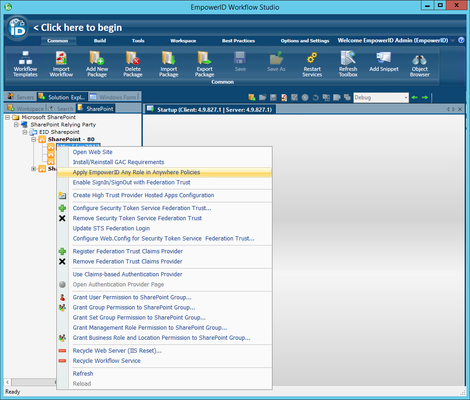
To enable the SharePoint WCF service
- On an EmpowerID Web Role server, log in to the EmpowerID Management Console as an administrative user.
- From the EmpowerID Management Console, click the application icon and select Configuration Manager from the menu.
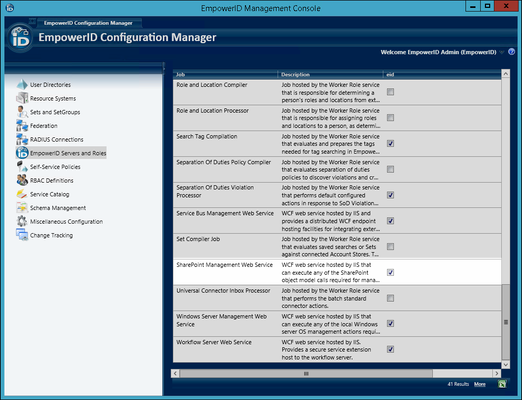
- In Configuration Manager, click the EmpowerID Servers and Roles node in the application navigation tree and locate the SharePoint Management Web Service in the Jobs grid.
- Enable the SharePoint Management Web Service on each desired EmpowerID Web Role server.
To create a SharePoint account store in EmpowerID
- On the EmpowerID Web Role server, log in to the EmpowerID Management Console as an administrative user.
- From the EmpowerID Management Console, click the application icon and select Configuration Manager from the menu.
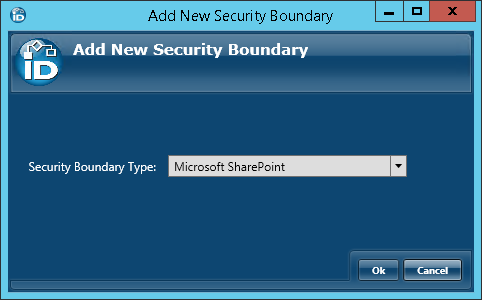
- In Configuration Manager, expand the User Directories node in the navigation tree and then click Account Stores.
- Click the Add New button.
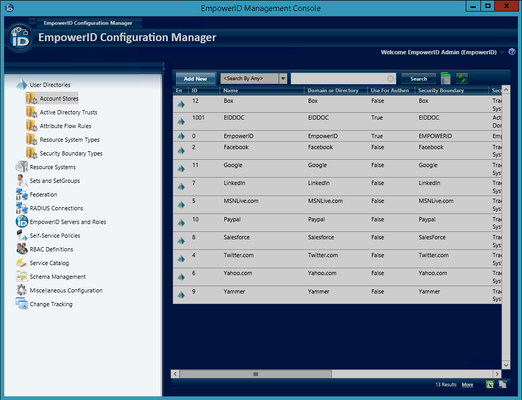
- In the Add New Security Boundary window that opens, select Microsoft SharePoint from the Security Boundary Type drop-down and then click OK.
- In the Security Boundary Details screen that appears, enter the Name, Display Name, and FQDN for the SharePoint account store.
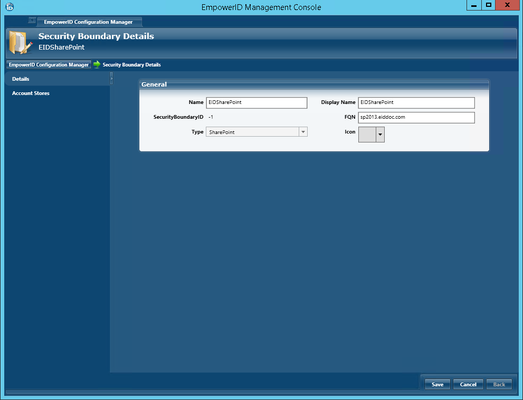
- Click Save.
To configure the SharePoint account store
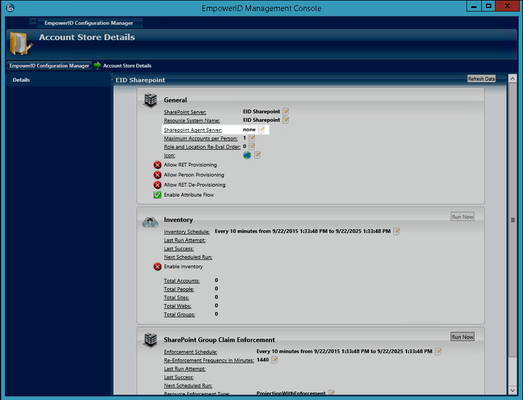
- From the Account Stores grid of Configuration Manager, double-click the SharePoint Account Store you just created, or right-click it and select Edit from the context menu.
- In the General pane of the Account Store Details screen that appears, click the Edit button to the right of the SharePoint Agent Server setting.
This opens the Choose Servers dialog, which allows you to select one or more EmpowerID Web Role servers running the SharePoint Management Web Service.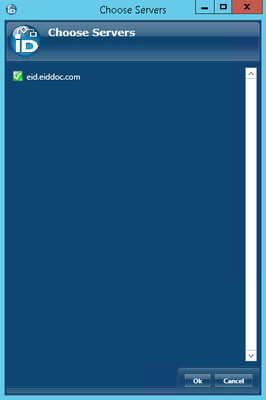
- From the Choose Servers dialog, toggle the Server button to the left of each desired EmpowerID Web Role server so that the icon for the button changes from a red sphere to a green check box and then click OK to close the dialog.

- In the General pane of the Account Store Details screen, toggle the Allow RET Provisioning button from a red sphere to a green check box if you want EmpowerID to create a Profile record in the SharePoint Profile store. This record is owned by a Person and is used to flow attribute changes to and from the SharePoint Profile record.
- In the General pane of the Account Store Details screen, toggle the Allow RET De-Provisioning button from a red sphere to a green check box if you want EmpowerID to delete the Profile record in the SharePoint Profile store when the corresponding EmpowerID Person is deprovisioned or loses this RET policy. SharePoint Profiles exist in a One-to-One relationship with Person objects in EmpowerID.
- In the General pane of the Account Store Details screen, select Allow Create Account On Membership Request to allow users without accounts to request group membership and automatically have an account created.
- In the Inventory pane of the Account Store Details screen, toggle the Enable Inventory button from a red sphere to a green check box to enable EmpowerID to inventory your SharePoint objects.
- In the SharePoint Group Claim Enforcement pane of the Account Store Details screen, click the Edit button to the right of Resource Enforcement Type and select the desired type of enforcement from the Change Resource Enforcement Type dialog that appears. The following options are available:
- No Action - No rights enforcement action occurs.
- Projection with No Enforcement - Changes to rights within EmpowerID occur only within EmpowerID; they are not passed on to the native SharePoint environment.
- Projection with Enforcement - Changes to rights within EmpowerID occur within EmpowerID and are enforced within the native SharePoint environment. This is the default setting.
Projection with Strict Enforcement - EmpowerID overrides any changes made in the native SharePoint environment. All changes made must occur within EmpowerID to be accepted. Strict Enforcement only applies to SharePoint Groups.
Info EmpowerID inventories SharePoint groups and enforcement adds one EmpowerID claim as a member of each group. The claim has the same name as the group with a GUID as the unique identifier. Getting access to the member Resource Role in EmpowerID means that this SharePoint group membership is added as a claim to the login token. SharePoint sees from the token that the member has a claim which is a member of this group.
- In the SharePoint Group Enforcement pane of the Account Store Details screen, toggle the Enable this Functionality button from red sphere to a green check box to enable SharePoint Group Claim Enforcement to occur.
Next, we need to add the SharePoint configuration settings to each SharePoint Resource System EmpowerID created for each connected SharePoint server.
To add the SharePoint configuration settings
- In Configuration Manager, click the Resource Systems tree node and then double-click the SharePoint Resource System or right-click it and select Edit from the context menu.
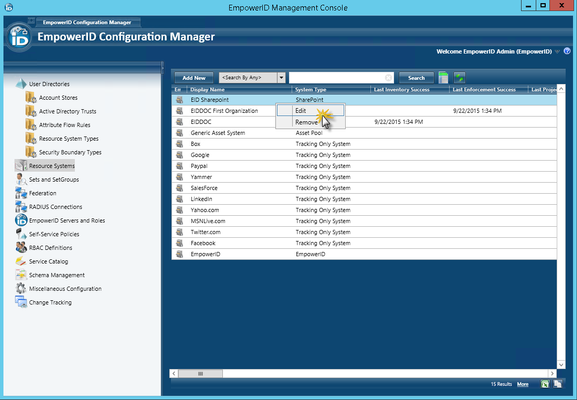
- Click the Settings tab in the SharePoint Resource System screen.
- Click Add New and then do the following:
- Type SPVersion in the Name field.
- Type your SharePoint version (2013 or 2016) in the Value field.
- Click Save.
- Click Add New again and then do the following:
- Type SPServerFQDN in the Name field.
- Type the fully qualified domain name of your SharePoint server in the Value field.
- Click Save.
- Click Add New again and then do the following:
- Type SPServerClientCertificate in the Name field.
- Type the thumbprint of the client certificate in the Value field. This is the SharePoint server certificate that EmpowerID uses to authenticate to the SharePoint Web services.
- Click Save.
- Click Add New again and then do the following:
- Type SPServerSSLCertificate in the Name field.
- Type the thumbprint of the SSL certificate in the Value field. This is the SharePoint SSL certificate that EmpowerID uses to create the endpoint identity for the SharePoint Web services.
- Click Save.
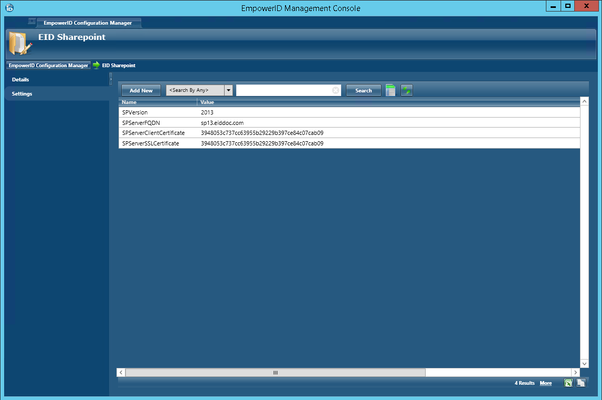
When you have completed the above, you have four Name/Value pairs that look similar to the below image. The Names must be identical to those depicted, while the Values may differ accordingly.
Next, we need to add the SharePoint certificates to the EmpowerID Certificate store. We demonstrate this in the section below.
To add the SharePoint Certificates to EmpowerID
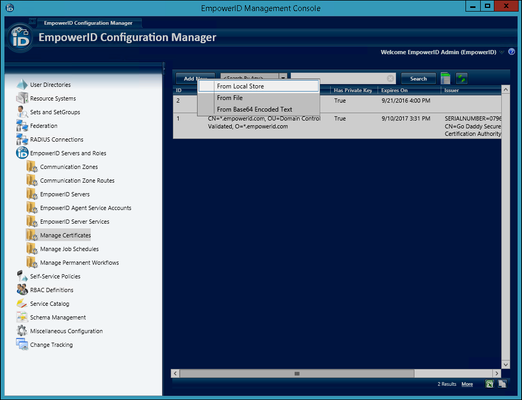
- In Configuration Manager, expand the EmpowerID Servers and Role node in the application navigation tree and then click the Manage Certificates node.
- Click the Add New button located above the Certificates grid and select From Local Store from the context menu.
- In the Windows Security dialog that appears, select the SharePoint SSL certificate you exported earlier, click OK and then click No when asked if the certificate requires a password. If you are using the EmpowerID SSL/STS certificate for your SharePoint server you can skip to step 5 below.
- Click Add New again and select From Local Store.
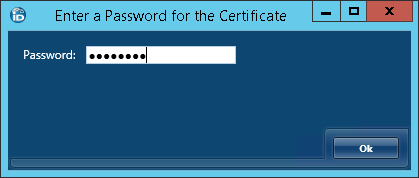
- In the Windows Security dialog that appears, select the SharePoint client certificate you exported earlier, click OK and then click Yes when asked if the certificate requires a password.
- Type the password for the certificate and then click OK.
Next, we need to map the SharePoint client certificate to an EmpowerID Person. Because the SharePoint Web services are claims-based, EmpowerID uses this Person to access those services. Create a new Person account strictly for this purpose.
To map the SharePoint Client Certificate to an EmpowerID Person
- Log in to the EmpowerID Web application as an administrator.
- From the Navigation Sidebar, expand Identities and click People.
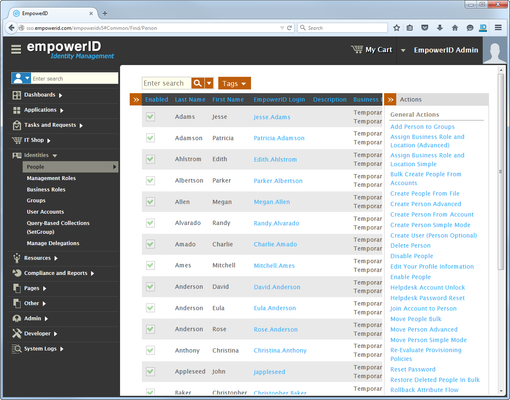
- In the Actions pane, click the Create Person Advanced link.
- Enter a first name and a last name for the Person account in the First Name and Last Name fields, respectively. As this Person account serves as a claims identity for the SharePoint Web service, you should name it accordingly. In our example, we are naming the Person "SharePoint Person Service Account."
- Specify a login in the Login field. (This user should never have to log in to EmpowerID.)
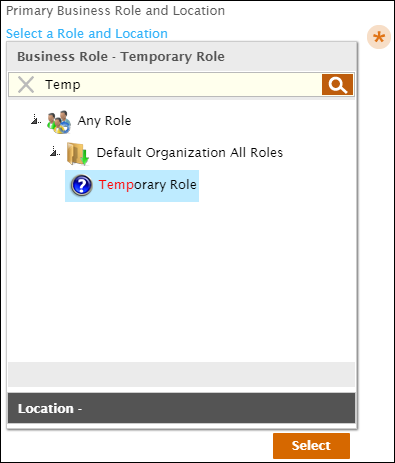
- Underneath Primary Business Role and Location, click Select a Role and Location.
- In the Business Role pane of the Business Role and Location selector that appears, type Temp, press ENTER and then click Temporary Role to select it.
- Click the Location tab to open the Location pane and then type Temp, press ENTER and click Temporary Role to select it.
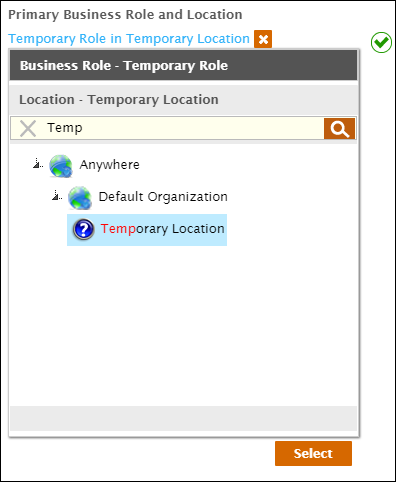
- Click Select to select the Business Role and Location for the Person account and close the Business Role and Location.
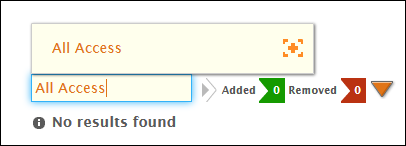
- Type All Access in the Management Role field and then click the tile for that role to select it.
- Click Save to create the EmpowerID Person.
- Once EmpowerID creates the person, navigate back to Person Manager by clicking the Find People breadcrumb at the top of the page.
- In Person Manager, search for the person you just created and then click the EmpowerID Login link for that person.
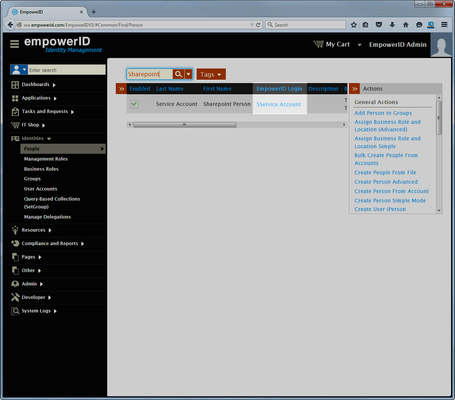
This directs you to the View One page for the person.View One pages allow you to view details about an object in EmpowerID and make changes to those objects as needed.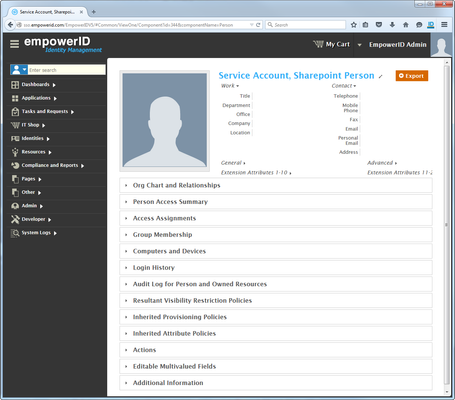
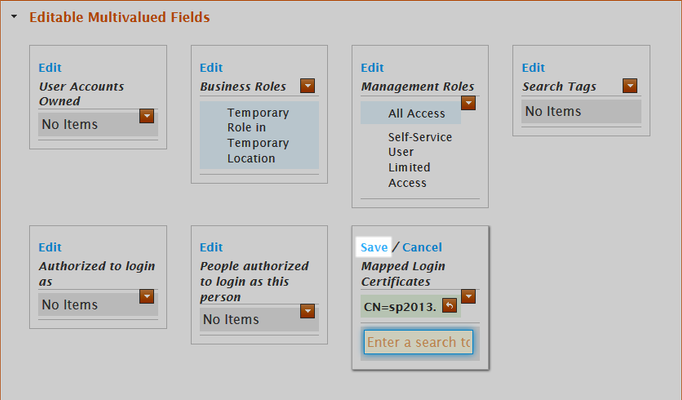
- From the View One page for the person, expand the Editable Multivalued Fields accordion and then click the Edit link in the Mapped Login Certificates pane.
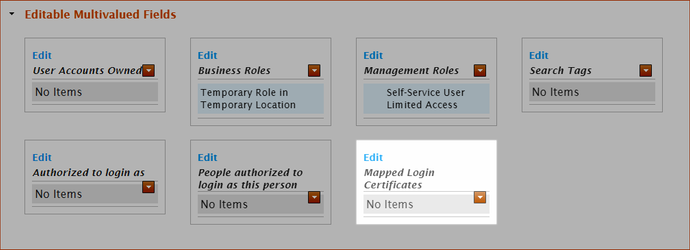
- Search for the SharePoint client certificate and then click the tile for the certificate to select it.
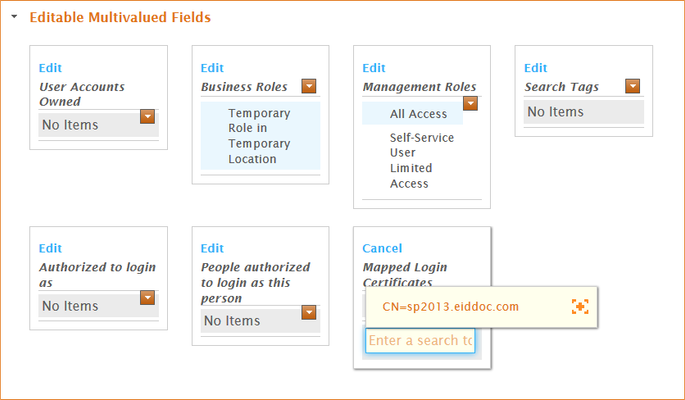
- Click the Save link.
Next, we need to create a WS Federation Connection for SharePoint in EmpowerID. We demonstrate this in the section below.
To create a WS-Fed Connection for SharePoint
- From the Configuration Manager application tree, expand the Federation > WS-Federation nodes and then click WS-Federation Connections.
- Click the Add New button located above the Configuration Manager grid. In the WS-Federation Single Sign-On Details screen that appears, do the following:
- Type a name for the WS-Federation connection in the Name field.
- Type a description for the WS-Federation connection in the Description field.
- Type http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name in the Map to Account Claim Type field.
- Type ~/Resources/Content/Images/Logos/EmpowerIDDark.png in the Image field.
- Select EmpowerID from the Account Store drop-down list.
The screen looks similar to the following image.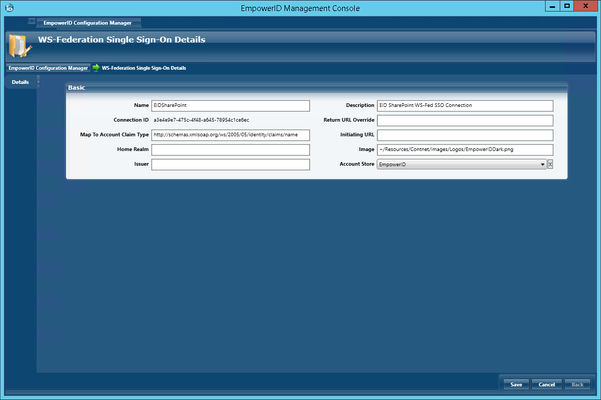
- Click Save.
Next, we need to configure a federated trust between the EmpowerID Security Token Service (STS) and your SharePoint.
To configure a federated trust between EmpowerID and SharePoint
Log in to Workflow Studio as an administrative user and from Solution Explorer, click the SharePoint tab to view the SharePoint resource system you just added to EmpowerID.
Note The following steps need to be performed once for each SharePoint farm in your environment.
Click the node for your SharePoint system and wait for Workflow Studio to load your SharePoint sites.
You should now see your sites in the SharePoint tree under your SharePoint resource system.Info If your SharePoint sites do not appear in the SharePoint tree, ensure that the SharePoint Management Web Service is enabled on at least one EmpowerID Web Role server and that the SharePoint Agent Server is set on the SharePoint Account Store Details screen.
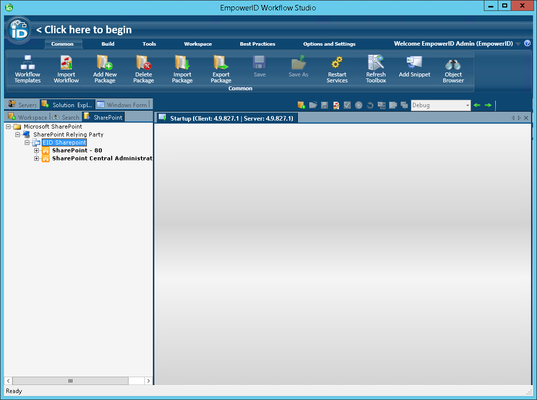
- From the SharePoint tree, expand the node for your SharePoint site and then right-click your SharePoint Site Collection URL and select Enable SignIn/SignOut with Federation Trust from the context menu.
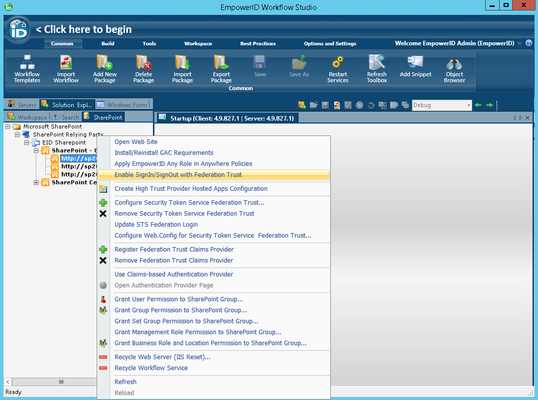
- Click Yes to confirm that you want to proceed with the overwrite.
- Right-click your SharePoint site collection URL again and select Register Federation Trust Claims Provider from the context menu.
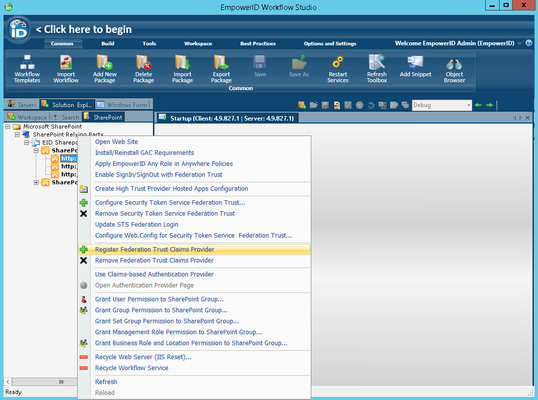
- Click Yes to confirm you want to register the EmpowerID SharePoint Claims Provider.
- Click OK to close the Success message box.
- From the SharePoint tree, right-click your SharePoint site URL again and select Configure Security Token Service Federation Trust from the context menu.
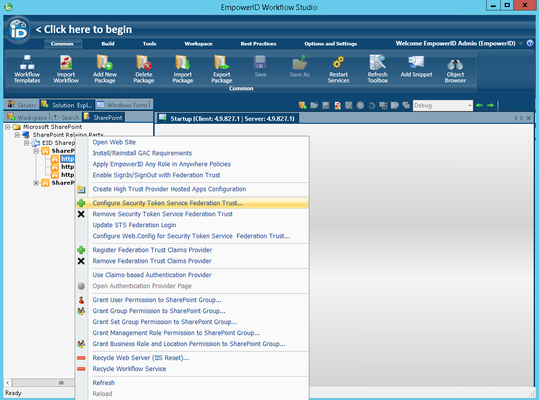
- In the Federation Trust wizard that appears, click Next.
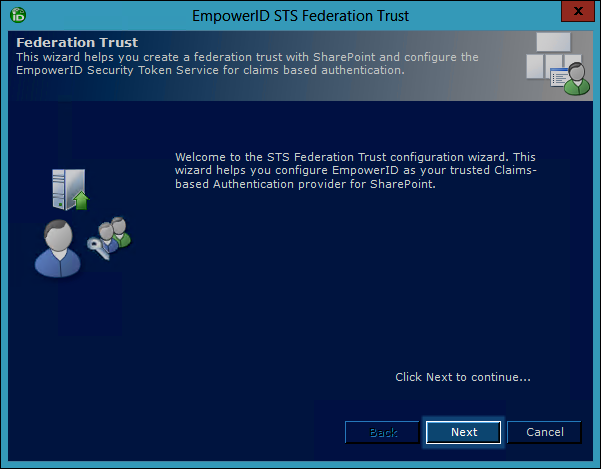
- Select the STS certificate and the Root Authority certificate and then click Next. (This is the Server certificate and the CA for that certificate configured for each EmpowerID Service.)
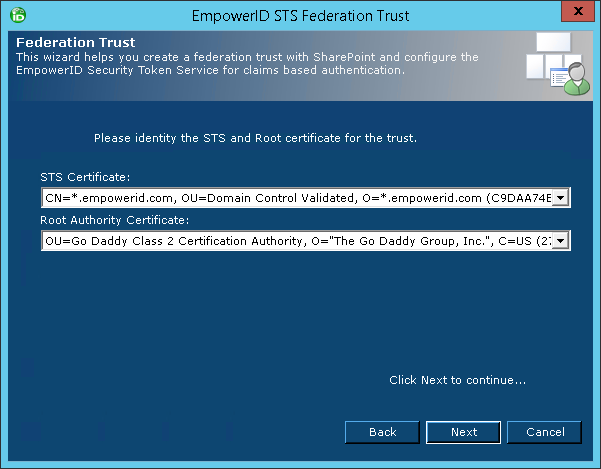
- Verify that the values for Identity Provider, Passive STS, Service Provider Connection and Realm are correct and click Next. The following image shows what the wizard looks like with the above values entered for our environment.
- Click Next to complete the registration.
- Select the STS certificate and the Root Authority certificate and then click Next. (This is the Server certificate and the CA for that certificate configured for each EmpowerID Service.)
- From the SharePoint tree, expand the SharePoint Central Administration node and then right-click the Central Administration site URL and select Open Web Site from the context menu.
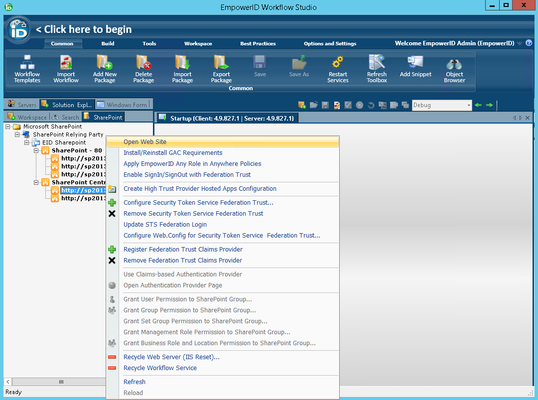
- From Central Administration, click Security section and then click the Manage Trust link underneath General Security.
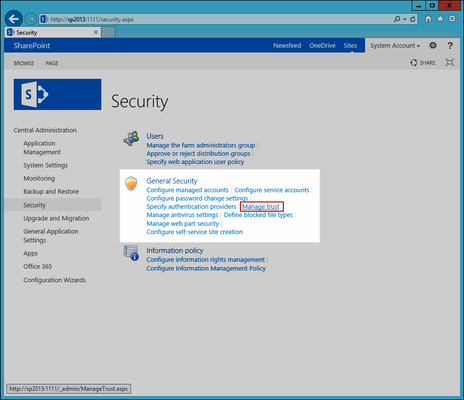
You should see EmpowerID listed as a Trusted Service Provider. - Click the EmpowerID link to select it and then click the Edit button in the Trust Relationships ribbon.
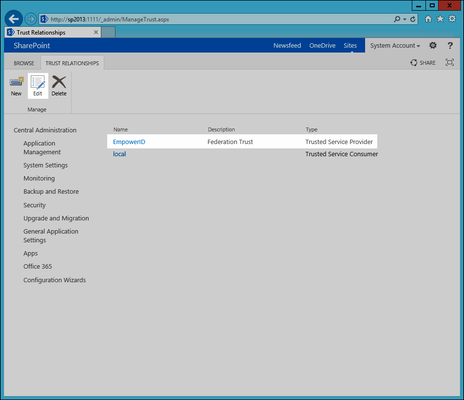
- In the Establish Trust Relationship dialog that appears, verify the following and then click OK to close the dialog.
- The Root Certificate thumbprint matches the STS root or STS intermediate certificate used in Step 10.
- The Security Token Service (STS) certificate thumbprint matches the STS certificate used in Step 10.
- (Optional) - If the STS certificate used in Step 10 chains to a root certificate that has not yet been added to the SharePoint certificate store, return to the Trust Relationships page and click New.
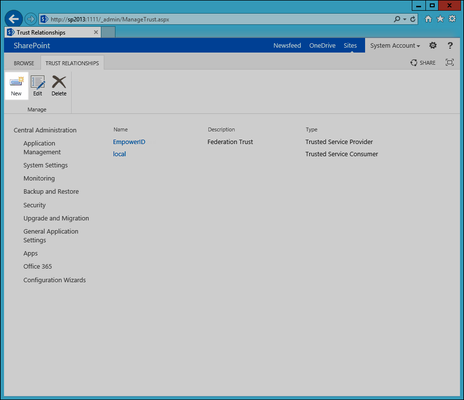
In the Establish Trust Relationship dialog that appears, type a name of your choosing in the Name field and then click the Browse button under Root Authority Certificate.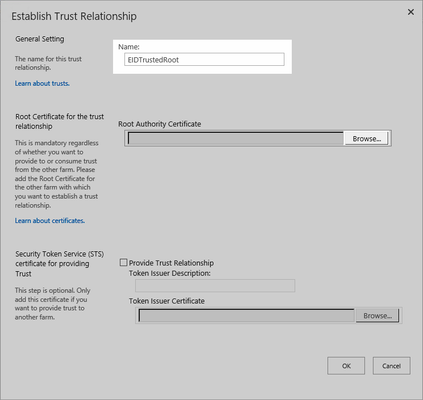
- Browse the file system and select the certificate that serves as the root certificate in the STS certificate chain and click OK.
- Click OK to close the Establish Trust Relationship dialog.
Now that the federated trust has been configured, you can convert your SharePoint sites from Windows Auth to Claims-based. We demonstrate this below.
To convert existing SharePoint sites to Claims Auth
| Note |
|---|
The following steps need to be performed for each SharePoint web application that you wish to use Claims-based Authentication |
- In Workflow Studio, right-click the root SharePoint site collection of the SharePoint web application that you wish to convert from Windows authentication to claims-based and select Use Claims-based Authentication Provider from the context menu.
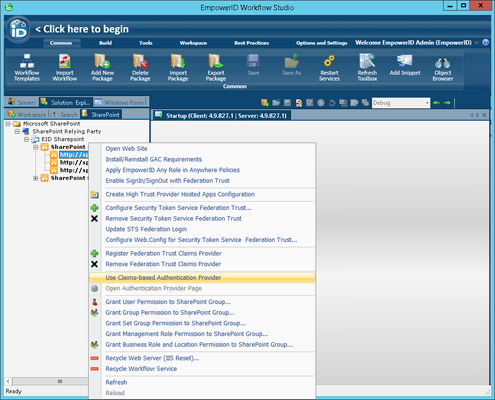
- Click Yes to confirm you want to use EmpowerID as a claims-based authentication provider for the site collection.
- Click OK to close the Success message box.
- Back in the SharePoint tree of Workflow Studio, right-click the SharePoint site collection and select Recycle Web Server (IIS Reset) to Reset IIS one more time.
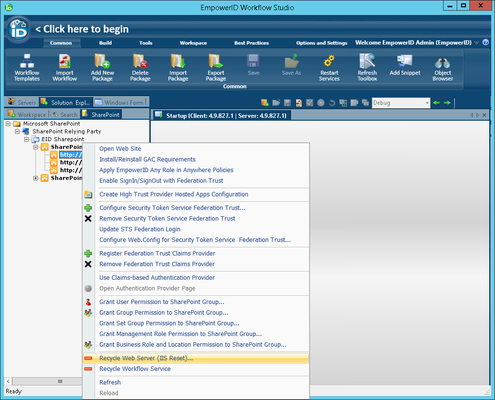
- Click Yes to reset IIS.
- Click OK to close the IIS reset completed message box.
- From the SharePoint tree, expand the SharePoint Central Administration node and then right-click the Central Administration site URL and select Open Web Site from the context menu.

- In the SharePoint Central Administration page that appears, under the Application Management section, click Manage web applications.
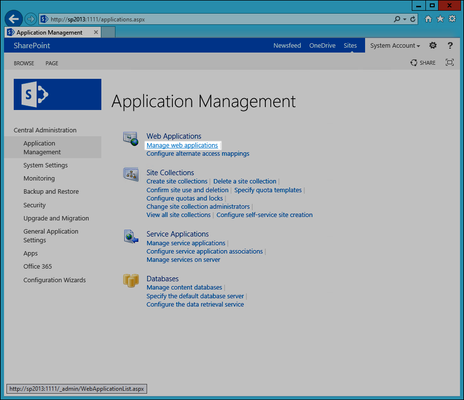
- In the Web Applications Management page that appears, click the SharePoint web application you are federating with EmpowerID and then click the Authentication Providers button in the ribbon.
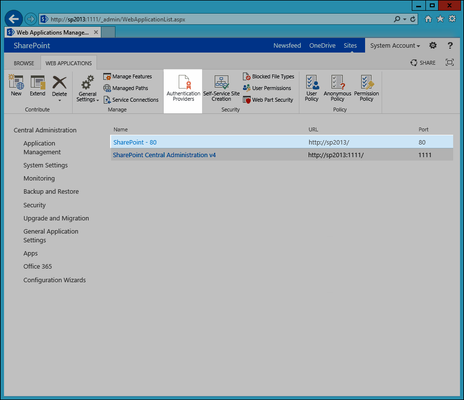
- In the Authentication Providers dialog that appears, click the desired SharePoint zone for the SharePoint web application you are federating with EmpowerID.
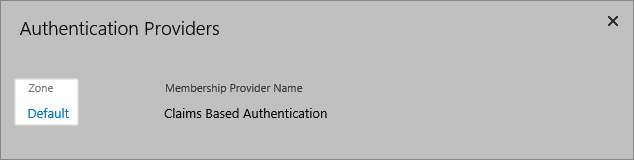
- In the Edit Authentication page that appears, scroll to the Claims Authentication Types pane, select Trusted Identity Provider and then select EmpowerID.
Scroll down to the bottom of the Edit Authentication page and click Save.
Note The following steps need to be performed for each SharePoint site collection that resides within a SharePoint web application that uses Claims-based Authentication.
- From Central Administration, click Application Management and then click Change site collection administrators under Site Collections.
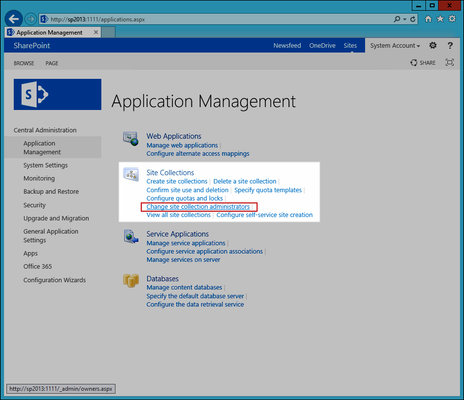
- In the Site Collection Administrators page, click the Browse button to the right of the Secondary site collection administrator field.
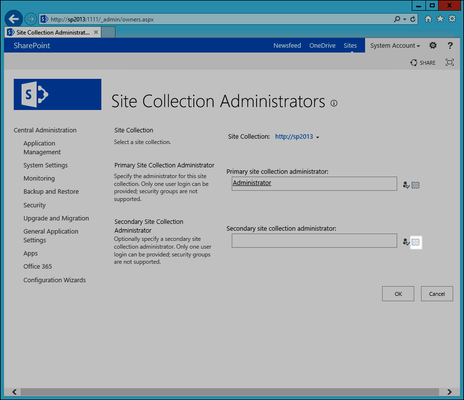
- In the Select People dialog that appears, click the People node under the EmpowerID Identity Provider node and then click EmpowerID Built-In Administrator. This is necessary to allow the EmpowerID Administrator the ability to log in to the SharePoint site to set permissions for your EmpowerID users once the site has been converted.
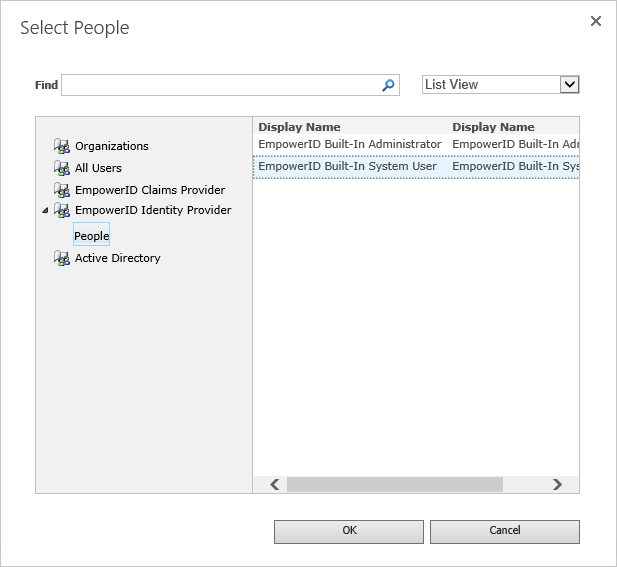
Click OK to close the Select People dialog and then click OK to close the Site Collection Administrators page.
Note The following steps need to be performed for each SharePoint server that services the web application being federated
From the SharePoint tree of Workflow Studio, right-click the SharePoint site again and select Configure Web.Config for Security Token Service Federation Trust from the context menu.
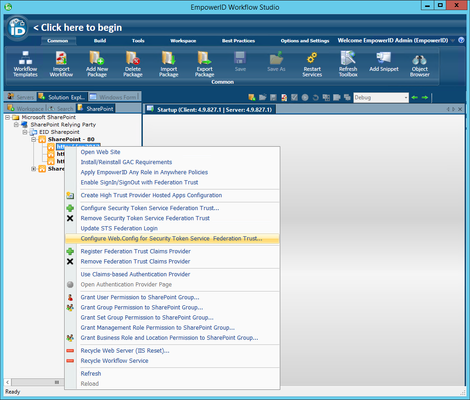
Note Make a backup of the Web config file before proceeding with the steps below.
In the EmpowerID STS SharePoint Web.Config Configuration dialog that appears, do the following:
- Ensure the Site Collection, Passive STS, and Realm fields are populated correctly. If any are incorrect, add the correct values.
- Select the Relying Party certificate from the Relying Party Certificate drop-down. (This is the same Server certificate configured for each EmpowerID Service.)
- Click the Web.Config button (...) and type the path to the Web.config file for your SharePoint site in the dialog. By default, this file is located at "\\servername\c$\inetpub\wwwroot\wss\VirtualDirectories\".
- Ensure that both the Passive STS Require STS and Create Federation Trust with EmpowerID based on the RP certificate, Realm and Site Collection if one does not already exist options are selected.
- Ensure that the Realm value is the FQDN of your SharePoint server and/or load balancer with /_trust appended.
The EmpowerID STS SharePoint Web.Config Configuration dialog looks similar to the following image:
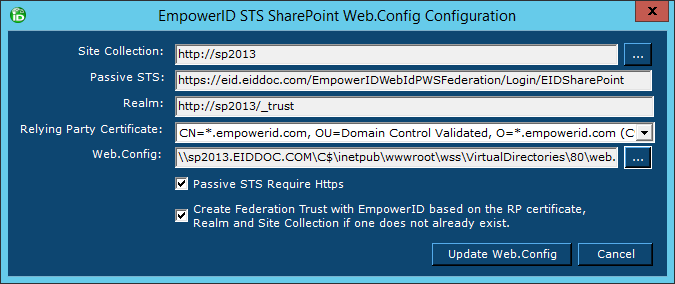
- Click the Update Web.Config button.
- Click Yes in the Confirmation message box.
- Click OK to close the Success message box.
To configure a Trusted Endpoint for a DNS alias
- If you have an external DNS alias for your SharePoint site, log in to Workflow Studio and click the Application Menu, click the Management Tools link and then click Trusted EndPoint Configuration.
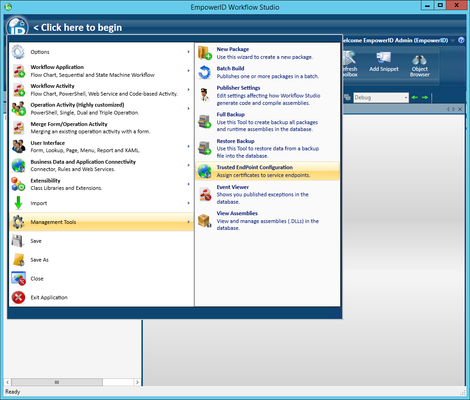
- On the Trusted EndPoint Configuration tab, on the right hand side under Certificates, right click your certificate and choose Add New Trust URI.
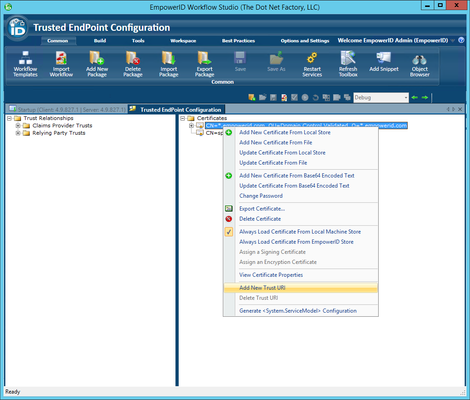
- Enter the external DNS alias of your SharePoint environment appended with /_trust and click OK.
Now that EmpowerID has been configured as a claims provider for the SharePoint Site Collection, you need to turn on inventory and enable SharePoint Group Enforcement claims in EmpowerID. We demonstrate this below.
To enable inventory and claims enforcement
- Return to the SharePoint Account Store Details screen in the EmpowerID Management Console.
- In the Inventory pane of the SharePoint Account Store Details screen, toggle the Enable Inventory button from a red sphere to a green check box to enable EmpowerID to inventory your SharePoint objects.
- In the SharePoint Group Claim Enforcement pane of the SharePoint Account Store Details screen, toggle the Enable this Functionality button from red sphere to a green check box to enable SharePoint Group Claim Enforcement to occur.
Now that EmpowerID has been configured as a claims provider for the SharePoint Site Collection, you can (optionally) grant permissions to your EmpowerID users for SharePoint access. We demonstrate this below by granting all EmpowerID Business Roles membership to the Viewers SharePoint group.
To grant SharePoint permissions to EmpowerID users
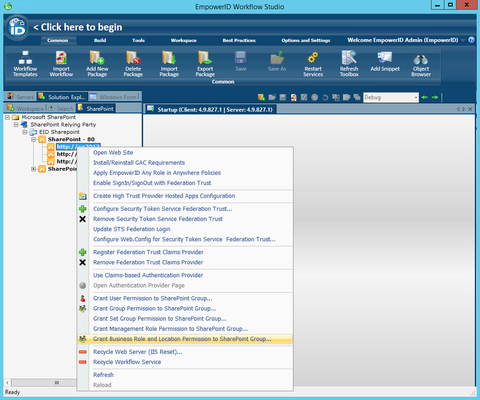
- From Workflow Studio, right-click the SharePoint Site and select Grant Business Role and Location Permission to SharePoint Group from the context menu.
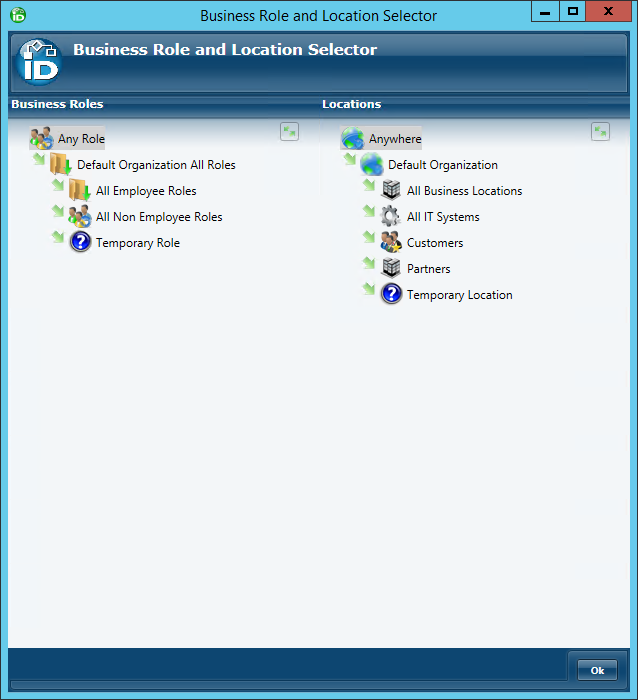
- In the Business Role and Location Selector that opens, select the desired Business Role from the Business Roles tree and the desired location from the Locations tree and then click OK. In our example, we have selected Any Role in Anywhere.
- In the Grant Business Role and Location Permission dialog that appears, select the desired SharePoint group(s) from the lower pane and then click OK.
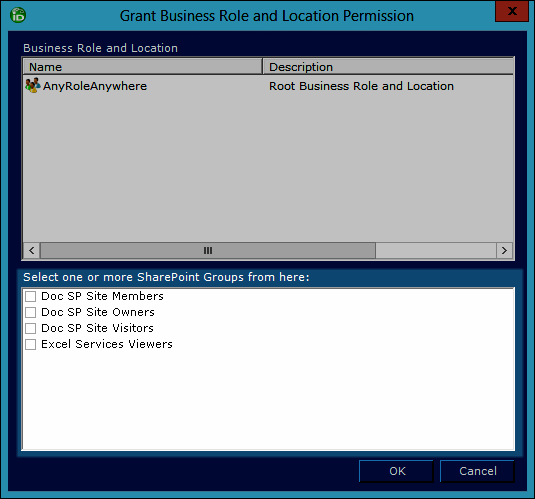
- Click Yes to confirm your decision.
Your EmpowerID users should now be able to log in to the SharePoint site using EmpowerID as the claims provider. You can test this by navigating to the SharePoint site from your browser. You are redirected to the EmpowerIDWebIdPWSFederation application, where you are prompted to enter your EmpowerID credentials.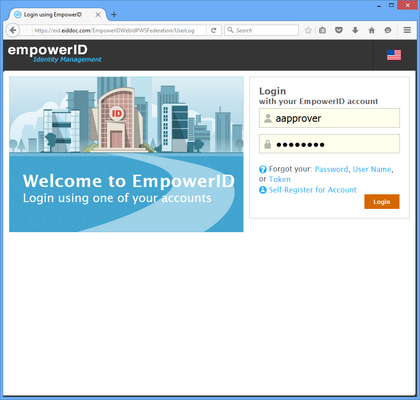
- Enter your credentials and click Login. You are authenticated in EmpowerID and redirected to the SharePoint site.
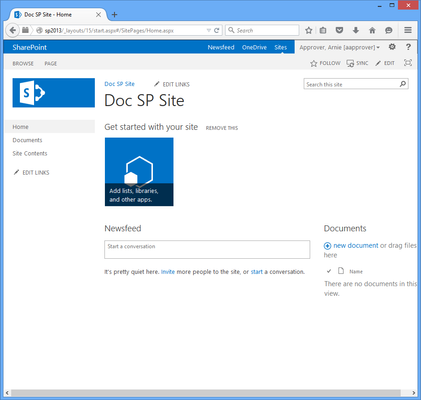
| Note |
|---|
If you have customized SharePoint master pages for any Web application, you must add the Any Role in Anywhere Business Role and Location to the User Policy for that Web application; otherwise, SharePoint will deny your EmpowerID users access to your SharePoint sites.
|
| Info | ||||
|---|---|---|---|---|
| ||||
| Div | ||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ||||||||||||||||||||||||
|