Versions Compared
| Version | Old Version 15 | New Version Current |
|---|---|---|
| Changes made by | ||
| Saved on |
Key
- This line was added.
- This line was removed.
- Formatting was changed.
| Div | ||
|---|---|---|
| ||
/wiki/spaces/E2D/pages/29982926 / Installation and Configuration / Connecting to Directory Systems / Current: Connecting to Google Apps |
| Excerpt | ||||
|---|---|---|---|---|
|
EmpowerID includes a Google Apps connector that can be used for adding Google Apps to the EmpowerID Identity Warehouse as a managed account store. This allows EmpowerID to update your Google Apps, creating, editing, and deleting users and groups, as well as provides the basis for setting up seamless SSO access to those accounts from EmpowerID.
| Info | ||
|---|---|---|
| ||
In order to connect EmpowerID to Google Apps, the following prerequisites must be met in Google:
|
| Info |
|---|
For help on setting up your Google Apps account, see Google's help topics on the subject. Some links you may find useful include the following: Managing projects in the Developers Console: Using OAuth 2.0 for Server to Server Applications, including delegating global authority to the service account: Directory API scope: |
After ensuring you have met the above prerequisites as well as those specified in the Getting Started with Directory Systems topic, you connect EmpowerID to Google Apps by doing the following:
- Importing the Service Account Certificate to the EmpowerID Server Certificate stores.
- Adding the Service Account Certificate to the EmpowerID Identity Warehouse
- Creating an account store in EmpowerID for Google Apps.
- Configuring EmpowerID settings for the account store connection, including whether to provision EmpowerID Persons during inventory or in batches using the Account Inbox permanent workflow (recommended).
- Reviewing and configuring the attribute flow rules for the account store.
- Turning on inventory.
- Enabling the Account Inbox Permanent Workflow when ready—if you are using batch processing to provision Person objects from the inventoried user accounts. This is the recommended method.
- Monitoring Inventory.
To import the Service Account Certificate to the EmpowerID Server Certificate Stores
- From MMC on the EmpowerID server, add the Certificates snap-in for the local computer.
- Expand the Certificates node, right-click Personal, point to All Tasks and click Import.
- In the Certificate Import Wizard that appears, click Next.
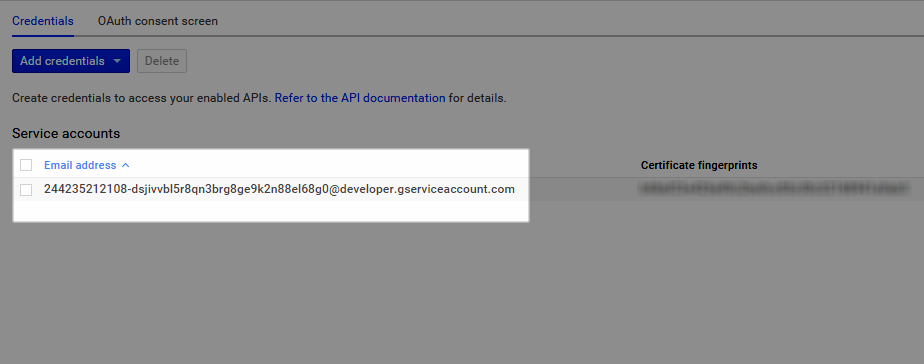
- Click Browse and locate the Service Account certificate Google created for you.
- In the Open window that appears, select your certificate and click Open.
- Back in the Certificate Import Wizard, click Next.
- Enter the password for the private key, mark the certificate as exportable, and then click Next. If you do not make the certificate exportable, an error will occur when adding it to the EmpowerID certificate store.
- Click Next again.
- Click Finish.
- Locate the Service Account certificate in the Personal store and copy it.
- Paste the Service Account certificate you just copied from the Personal store in to the Trusted Root Certification Authorities certificate store.
To add the Service Account Certificate to EmpowerID
- Open the EmpowerID Certificate Manager. In a default installation of EmpowerID, the path to the executable is located at "
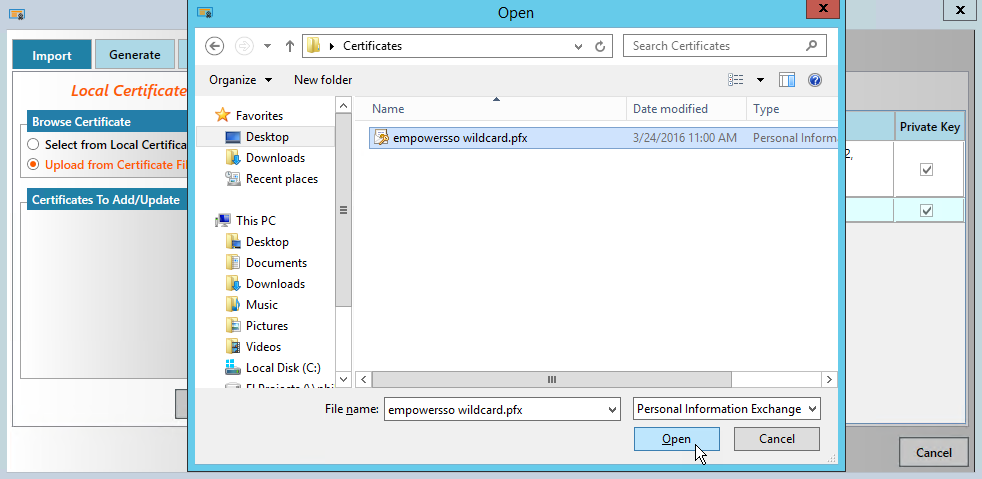
C:\Program Files\TheDotNetFactory\EmpowerID\Programs\EmpowerID.CertificateManager.exe". - From the Import tab of the EmpowerID Certificate Manager, select the appropriate method for importing the certificate and follow the dialogs for that method. For example, if you are importing a certificate from file, select Upload from Certificate File and then browse for the file.
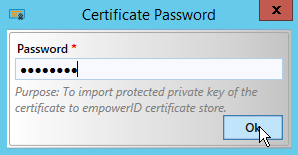
- Enter a password for the certificate and click Ok.
To create an Account Store for Google Apps Connector
- Log in to the EmpowerID Management Console as an administrator.
- Click the application icon and select Configuration Manager from the menu.
- In Configuration Manager, select the Account Stores node and then click the Add New button above the grid.
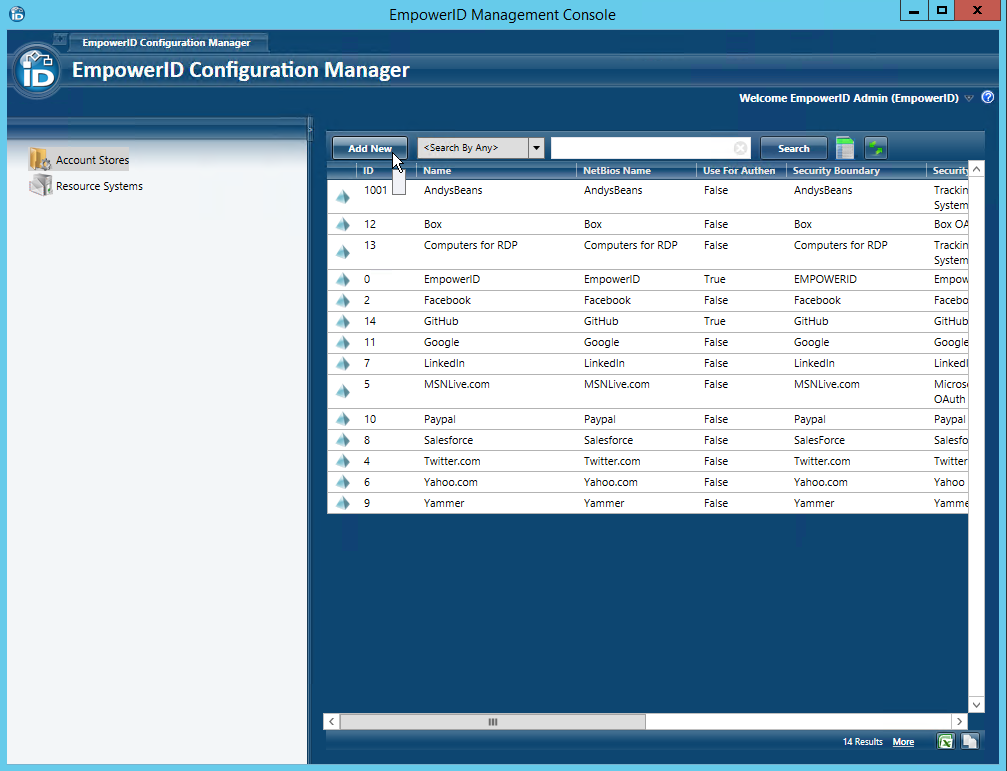
- In the Add New Security Boundary window that opens, select Google Apps from the Security Boundary Type drop-down list and then click OK.
- In the Add Google Connection window that appears, do the following:
- Type the name of your Google Apps domain name in the Domain field.
- Type the username of the service account you created in Google Apps for EmpowerID in the Username field.
- Type the password for the EmpowerID service account in the Password and Confirm Password fields.
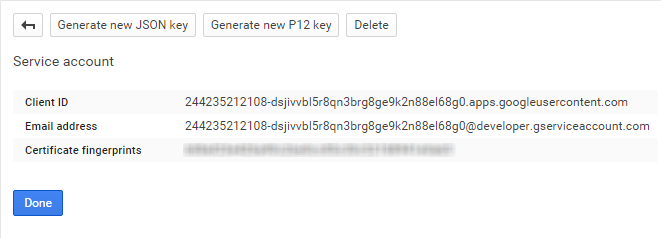
- In the OAuth Service Account (SA) Email field, type the email address Google created when it generated the P12 certificate linking the EmpowerID service account to the EmpowerID project.
In the OAuth SA Certificate Thumbprint field, type the certificate fingerprint of the P12 certificate Google that generated to link the EmpowerID service account to the EmpowerID project.
Info If the values entered in the Add Google Connection window are incorrect, EmpowerID will not be able to authenticate to Google and the connection will fail.
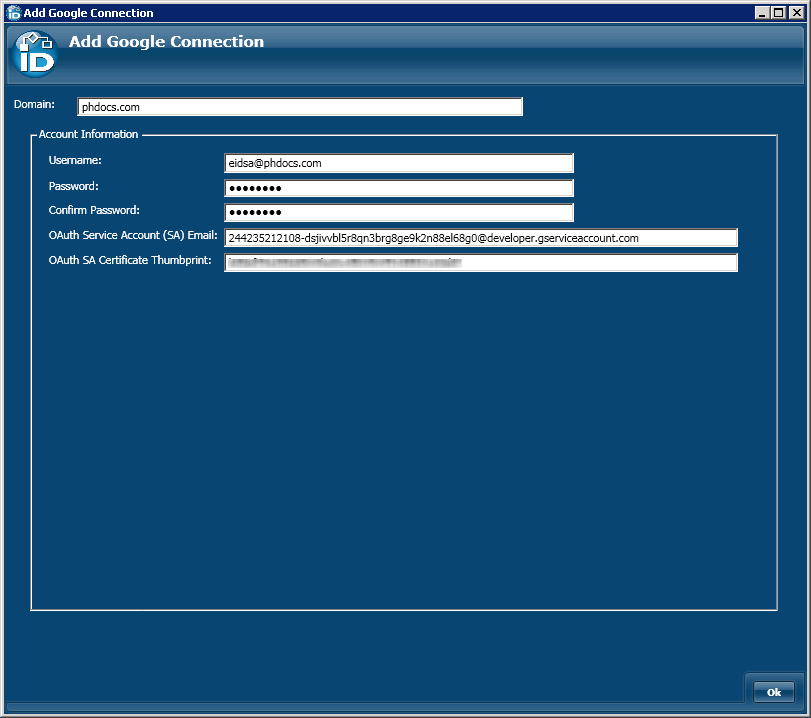
- Click OK to close the Add Google Connection window.
- From the General pane of the Google Apps Account Store Details screen, enable each desired feature by toggling the icon to the right of each feature from a red sphere to a green check box. For example, if you wish to allow password synchronization to occur between EmpowerID and Google, toggle the red sphere to the right of Allow Password Sync to a green check box, as shown in the below image. An explanation of the other setting in this pane follows the image.
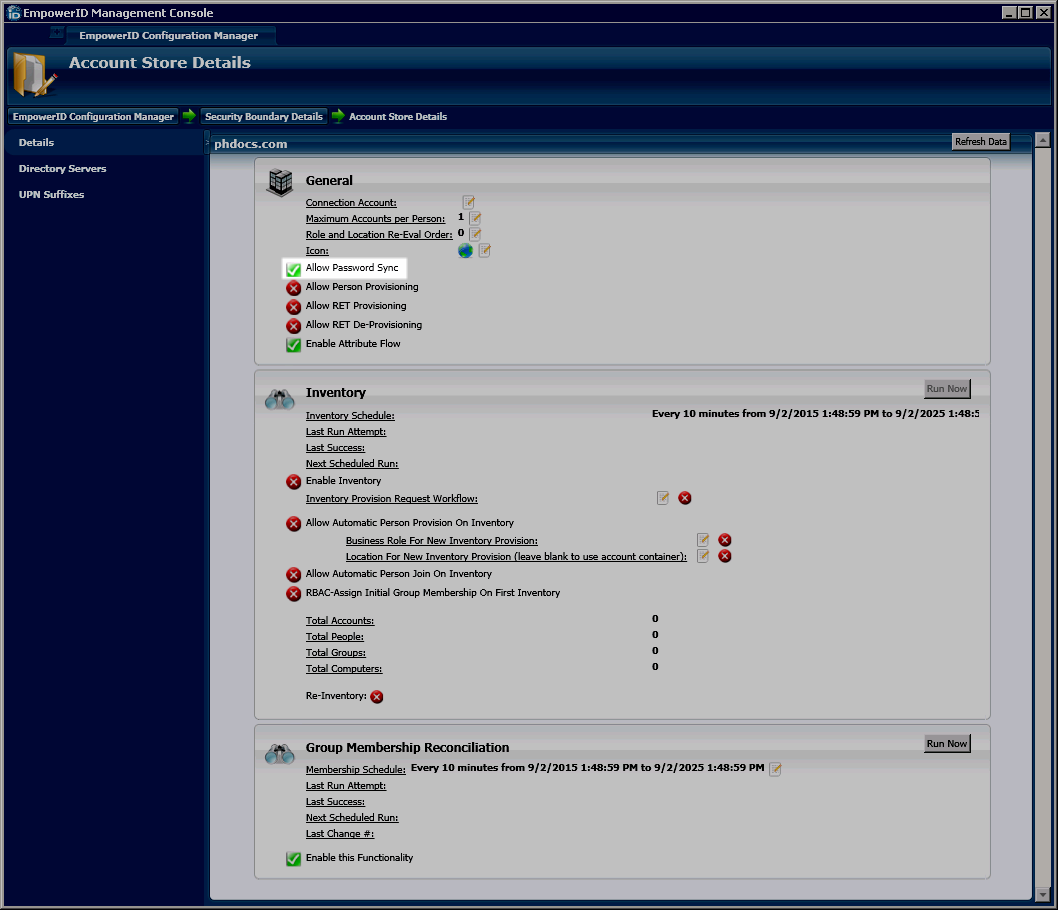
- Allow Person Provisioning — This specifies whether Person objects can be created from each inventoried user account EmpowerID. If enabled, EmpowerID either will create a new Person object for each new user account or join those user accounts to existing EmpowerID Person objects based on the configuration of your Join and Provision Rules (described in further details below).
- Allow RET Provisioning — If enabled, EmpowerID applies any Resource Entitlements policies to each person provisioned from an inventoried AWS account if those people are placed in a Business Role and Location that is targeted by a Resource Entitlement Policy.
- Allow RET De-Provisioning — If enabled, EmpowerID removes any Resource Entitlements received by the AWS users if those users no longer meet the criteria for those resources.
- Enable Attribute Flow — This specifies whether to allow changes to user attributes to flow between EmpowerID and the account store.
From the Inventory pane of the Account Store Details screen, do the following:
Info EmpowerID recommends using the Account Inbox to provision Person objects from user accounts. The below information is included to make you aware of the option to provision during inventory.
Toggle Allow Automatic Person Provision On Inventory to reflect your policy for the account store (red sphere for disable and green checkbox for enable). When enabled (and Allow Person Provisioning is enabled for the account store), EmpowerID will provision Person objects for all new accounts discovered during inventory in real-time, if they meet the conditions of your Provision rules.
Tip icon false - Toggle Allow Automatic Person Join On Inventory to reflect your policy for the account store (red sphere for disable and green checkbox for enable). When enabled (and Allow Person Provisioning is enabled for the account store), EmpowerID will attempt to join any new accounts discovered during inventory — if it finds one that matches the conditions of the Join rules for the account store. If this setting is not enabled, EmpowerID will not join secondary accounts to an EmpowerID Person, but will instead provision new EmpowerID Persons for each of those additional accounts.
The last action to perform on this screen is to enable inventory. However, before doing so, it is important to configure the attribute flow rules for the account store and to enable the Account Inbox if batch processing of those accounts is desired.
To configure Attribute Flow rules
| Tip | ||
|---|---|---|
| ||
Open a browser and log in to the EmpowerID Web application.
- From the Navigation Sidebar, expand Admin > Applications and Directories and click Attribute Flow Rules.
From the Attribute Flow Rules page, click the Advanced Search drop-down button, enter the name of the account store for which you want to configure the flow rules and then click Search to filter the rules shown in the grid.
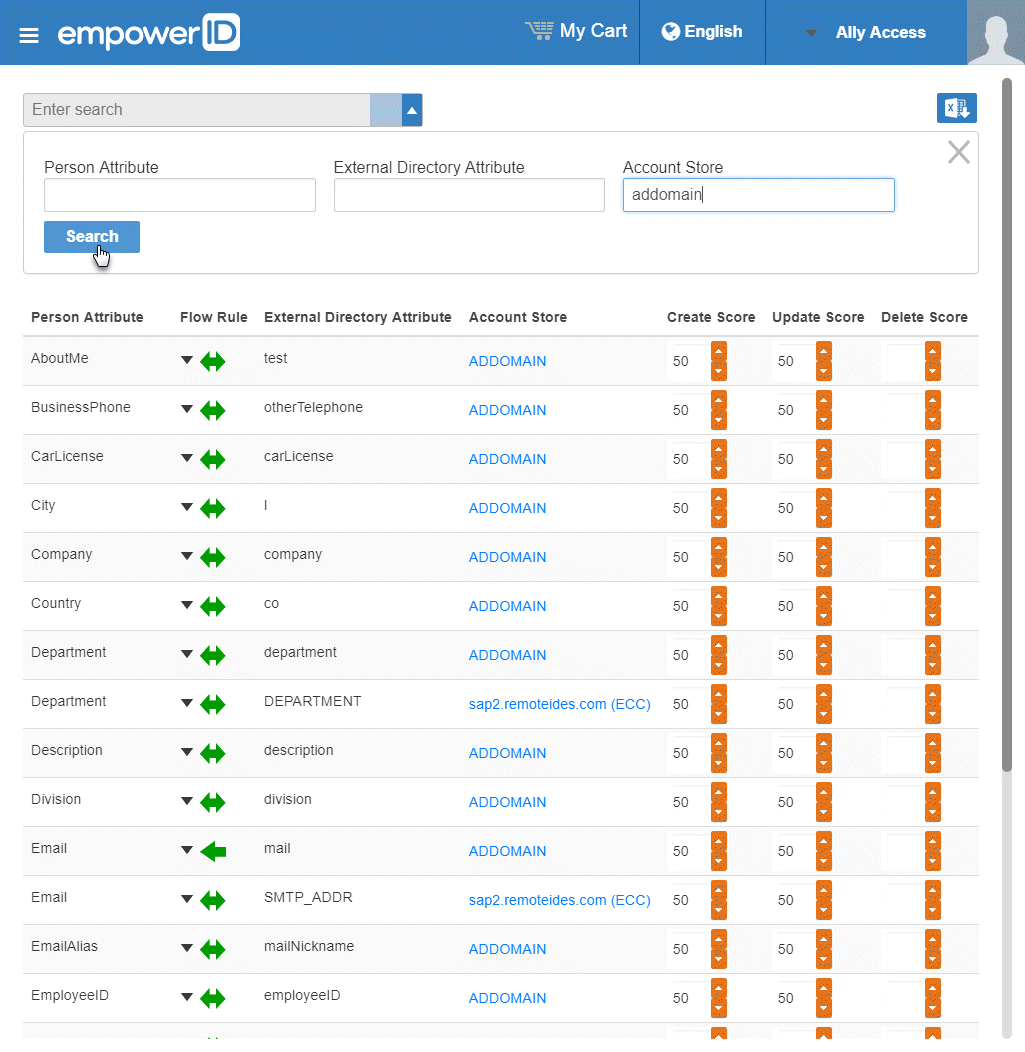
Info The attributes from the EmpowerID Person object are displayed in the left column with the corresponding attributes from the account store displayed in the right column.
To change the flow for an attribute, click the Attribute Flow drop-down located between the Person Attribute column and the External Directory Attribute column, and select the desired flow direction from the context menu.
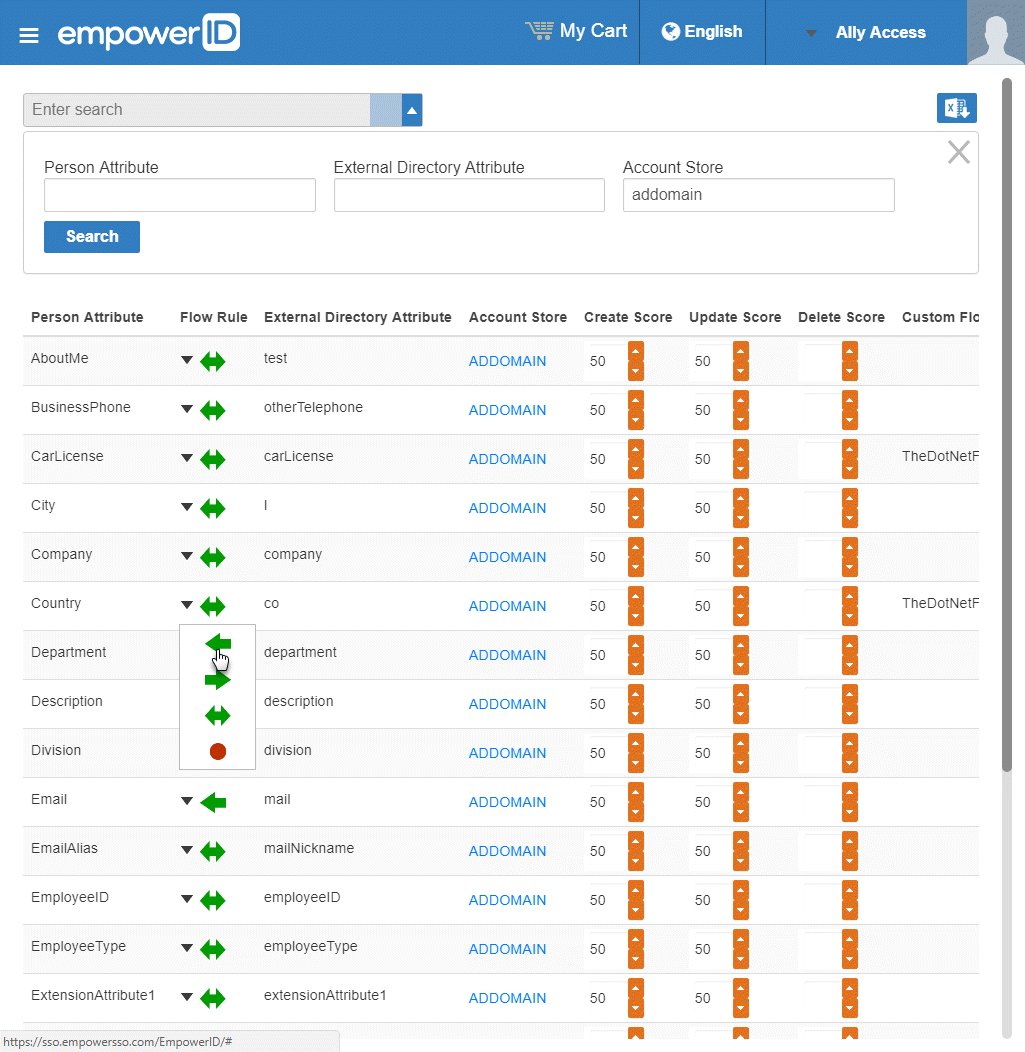
To change the score for any of the available CRUD operations (Create, Update and Delete), enter the new score in the appropriate field. By default, scores are weighted evenly, which means that a change to an attribute originating in one connected external directory has the same authority as a change to an attribute occurring in another connected external directory.
Info EmpowerID only considers scores for attribute CRUD operations when multiple account stores with the same user records are connected to EmpowerID, such as would be the case if an HR System and Google Apps were being inventoried by EmpowerID.
To turn on inventory
Return to the Account Store Details screen in Configuration Manager.
Look over your settings one last time and when satisfied, turn on inventory by toggling the Enable Inventory button from a red sphere to a green check box.
If you are using the Account Inbox to provision or join the user accounts in Google to Empower Persons, you need to turn on the Account Inbox. This is demonstrated in the below section.
To enable the Account Inbox permanent workflow
- From the Navigation Sidebar of the EmpowerID Web interface, expand Admin > EmpowerID Servers and Settings and click Permanent Workflows.
- From the Permanent Workflows page, click the Display Name link for Account Inbox.
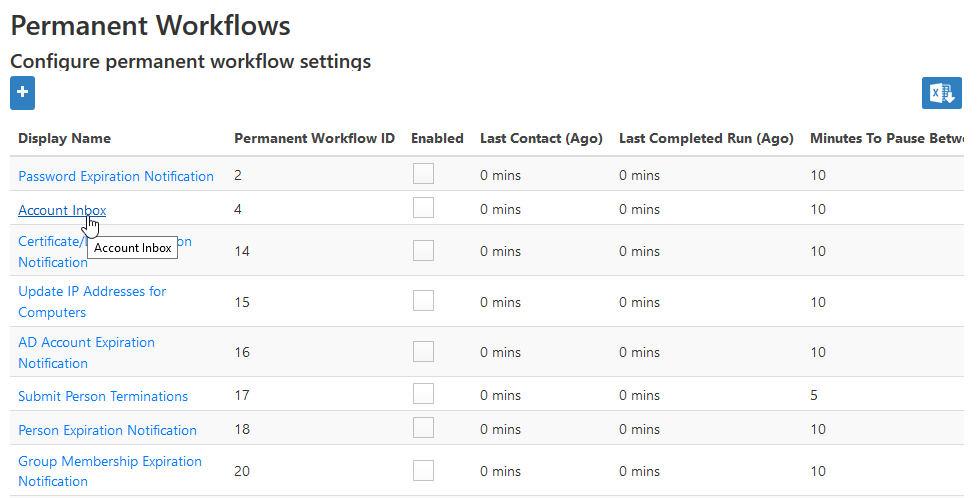
- From the View One page for the workflow that appears, click the edit link for the workflow.
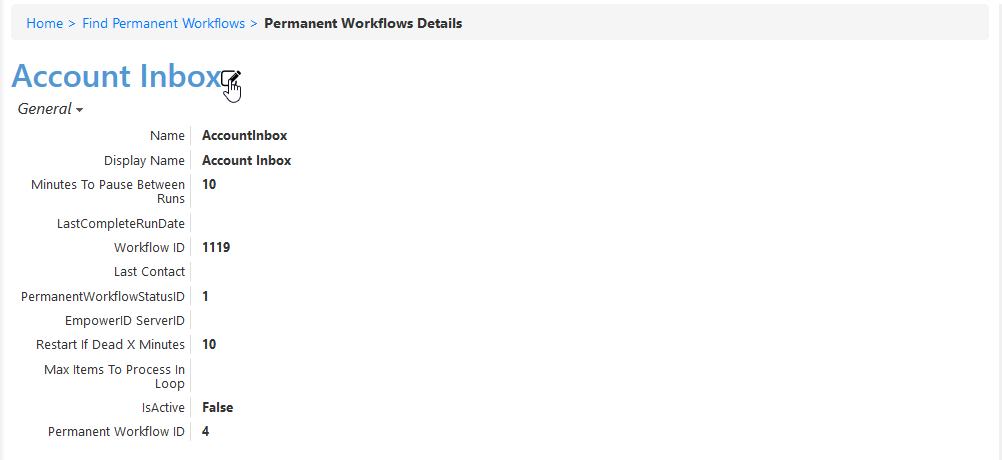
- From the Permanent Workflow Details form that appears, select Enabled and then click Save. Based on the default settings applied to the workflow, EmpowerID will process 1000 of the user accounts in the Account Inbox every ten minutes, provisioning Person objects from those user accounts and joining them together based on the Join and Provision rules applied to the account store.
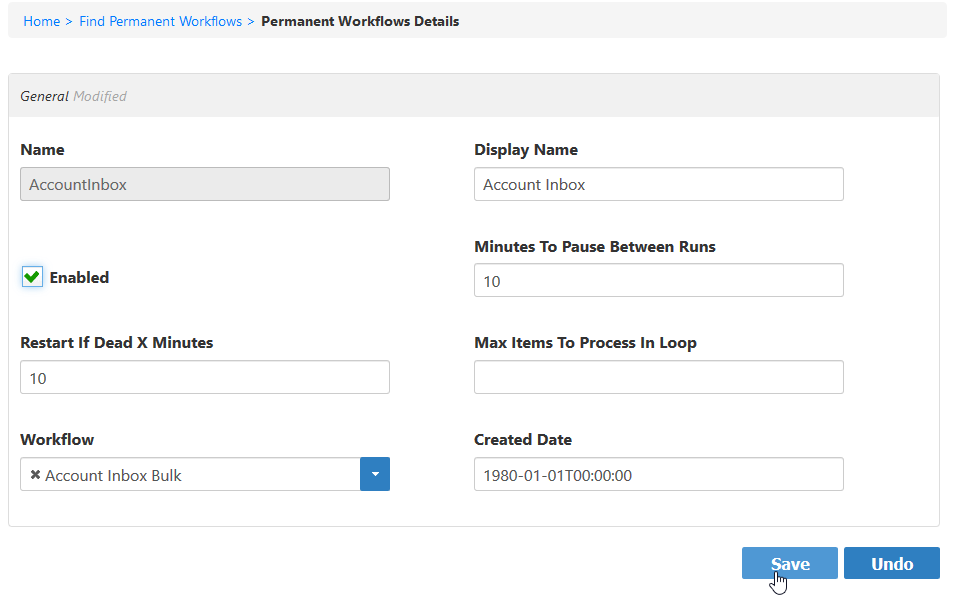
To monitor inventory
- From Navigation Sidebar, expand System Logs > Policy Inbox Logs and click Account Inbox.
The Account Inbox page appears. This page provides tabbed views of all information related to processing new user accounts discovered in a connected account store during inventory. An explanation of these tabs follows.
- Dashboard - This tab provides a quick summary of account inbox activity.
- Not Processed - This tab displays a grid view of all inventoried user accounts not yet used to provision a new EmpowerID Person or joined to an existing Person. Any accounts that fail to meet the Join and Provision rules are displayed here as well.
- Failed - This tab displays a grid view of any account joining or provisioning failures.
- Ignored - This tab displays a grid view of all accounts ignored by the account inbox. Accounts are ignored if they do not qualify as user accounts.
- Joined - This tab displays a grid view of all accounts joined to an EmpowerID Person. Joins occur based on the Join rules applied to the account store.
- Processed - This tab displays a grid view of all accounts that have been used to either provision a new EmpowerID Person or joined to an existing EmpowerID Person.
- Provisioned - This tab displays a grid view of all accounts that have been used to provision an EmpowerID Person. Provisioning occurs based on the Provision rules applied to the account store.
- Orphans - This tab displays a grid view of all user accounts without an EmpowerID Person.
- All - This tab displays a grid view of all user accounts and the status of those accounts in relation to the Account Inbox.
| Div | ||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ||||||||||||||||||||||
|