Versions Compared
Key
- This line was added.
- This line was removed.
- Formatting was changed.
EmpowerID uses multiple Windows services to host job functions as well as a variety of IIS Web REST Services to perform its processing. Each of the Windows Services and the IIS Application Pool Identities require a user identity (service account) with the necessary privileges to access the EmpowerID database. Before you install EmpowerID, you should first create these accounts, giving them the necessary access rights to interact with the EmpowerID database and the local machine on which EmpowerID is installed. To delegate the necessary access rights, EmpowerID recommends you follow the security practice of least privilege by granting service accounts the minimum access needed to perform the tasks associated with each. To implement least privilege, you will need to do the following:
- Create one or more service accounts for running the EmpowerID Windows services and EmpowerID IIS app pools
- Create a user account on the server hosting the EmpowerID Identity Warehouse and give that account read and write access to the database backup folder, as well as the ability to restore a SQL database
- Restore the EmpowerID Identity Warehouse using the above specified user account
- Create SQL logins for each service account and grant those logins the required rights to the EmpowerID Identity Warehouse
- Install EmpowerID using the specified local admin account
- On each server hosting an EmpowerID installation, grant the service accounts the required permissions needed to GAC EmpowerID assemblies and perform everyday operations.
This article takes you through each of these steps, demonstrating how to install EmpowerID using the recommended least privilege configuration.
| Warning | |||||||
|---|---|---|---|---|---|---|---|
Prior to running EmpowerID, you must install the Microsoft IIS CORS and URL Rewrite modules on each EmpowerID server. To do so, please run the PowerShell script below in administrative mode.
|
| Tip |
|---|
|
To install EmpowerID using least privilege
Create an EmpowerID service account for your domain. This account will be used to set the least privileges needed to support GAC'ing EmpowerID assemblies and performing everyday operations. After you create the account, retrieve its SID. The SID will be used to grant the account the necessary privileges to run each EmpowerID Windows service.
Create an application pool account for your domain. This account will be used to run the EmpowerID application pools. After you create the account, retrieve its SID. The SID will be used to grant the account the necessary permissions to run each EmpowerID Windows service.
Div class short-code-block Code Block language text theme Confluence WMIC useraccount WHERE Name="EmpowerIDServiceAccount" GET SID
- Create a local user account on the SQL server that is to host the EmpowerID SQL Identity Warehouse and give the account read and write access to the database backup folder.
- Create a SQL login for the above user account and grant the login the ability to restore a SQL database.
- Log in to the SQL server as the above user and restore the EmpowerID database by doing the following:
- Right-click the Databases node and select Restore Database.
- Under Source, select Device and enter the path to the EmpowerID.bak folder.
- Under Destination, enter EmpowerID (to avoid the longer database name).
- Click OK to restore the database. This process takes several minutes.
- On the SQL Server, create logins for each service account and give those accounts the right to alter the database. Specifically, each service account must have the following database capabilities:
- Connect
- Authenticate
- Execute
- Delete
- Insert
- Select
- Update
- Alter — Needed on the following tables only to allow for truncation:
- PersonOrgRoleOrgZoneReEvalTempAccountData
- PersonOrgRoleOrgZoneReEvalTempPersonData
- PersonManadatoryAttributesTemp
- PersonMandatoryAttributesTempPreview
- PersonMandatoryAttributesOverwritePreview
AccountObjectAttributeOutboxPreview
Div style margin-left:-60px; margin-top:20px; Info To facilitate the granting of these privileges, EmpowerID has created a Server Role named EmpowerIDService. You can map this role to each service account on the EmpowerID database.
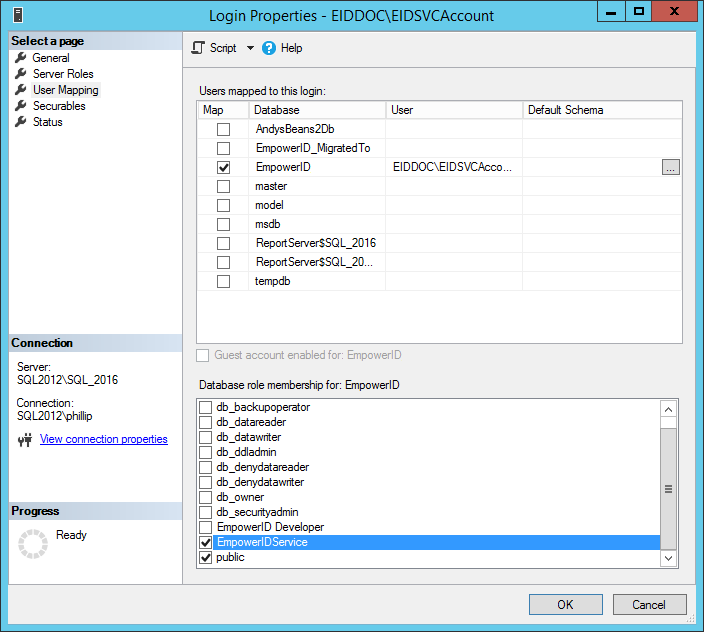
Div style margin-left: -95px;;margin-top: 20px; Note If you are installing a build that is newer than 6.0.142.0, please skip the below steps and following the steps in the Installing EmpowerID in Post 6.0.142.0 Builds drop-down.
- Next, log in to the server that is to host the EmpowerID installation as a local administrator and open the EmpowerID.msi.
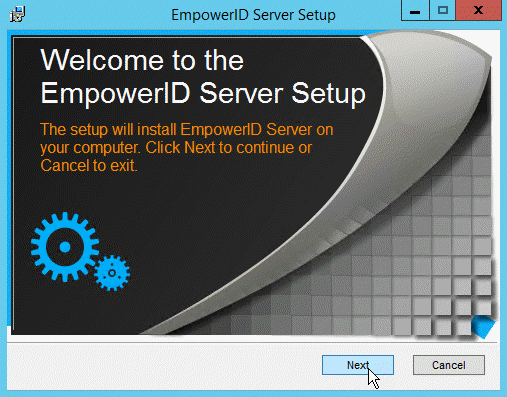
- In the EmpowerID Server Setup that appears, click Next to begin the installation.
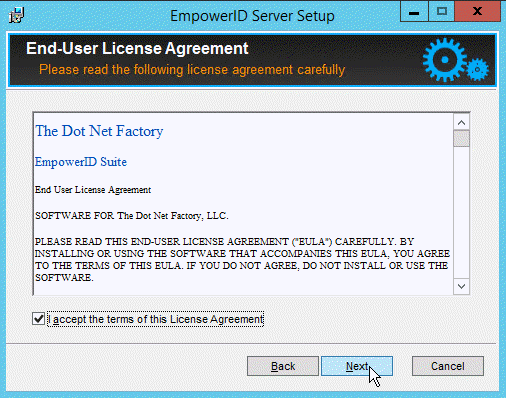
- Accept the license agreement and click Next to continue.
- Review the path where EmpowerID will be installed and click Next. If you want to install EmpowerID in a different directory, click the Change button to choose a new path and then click Next.
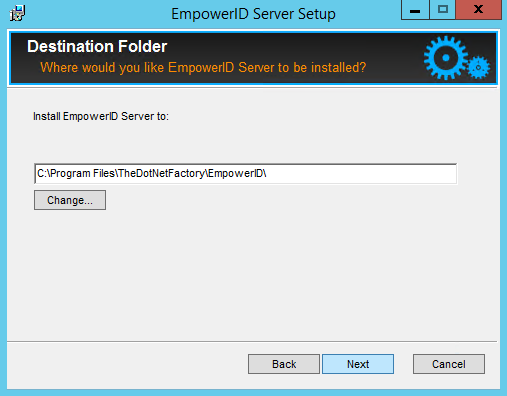 Image Modified
Image Modified - Click Install to begin the installation.
 Image Modified
Image Modified Wait for the installer to complete the installation and then click Finish to close the installer.
 Image Modified
Image ModifiedAnchor newinstallmethod newinstallmethod
| Info | ||
|---|---|---|
| ||
To configure your EmpowerID installation
From the Start menu, search for the EmpowerID Configurator, right-click it and select Run as administrator from the context menu.
EmpowerID Configurator opens. You use the configurator to connect EmpowerID to your SQL server, license your copy of EmpowerID, as well as to configure default email settings, certificates, IIS Web Sites, and the EmpowerID Windows services.Note If you close the Configurator before you finish, to avoid becoming unable to log in as empoweridadmin, here is how to reopen it in install mode:
- In File Explorer, navigate to C:\Program Files\TheDotNetFactory\EmpowerID\Programs.
- In the address bar, type cmd.
- In the command prompt that appears, type empowerid.configurator.exe install.
 Image Modified
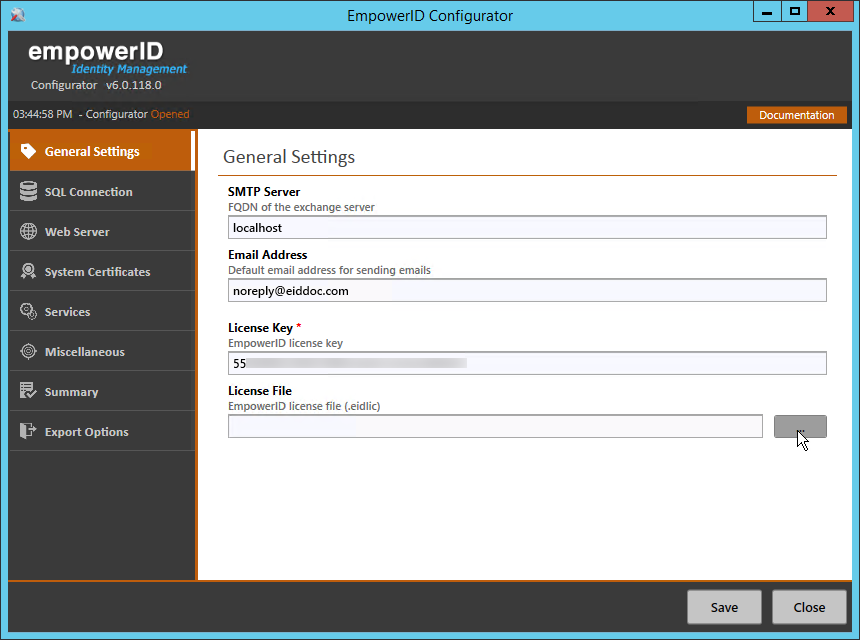
Image Modified- From the General Settings tab of the EmpowerID Configurator, do the following:
- In the SMTP Server field, type the FQDN of the Exchange server EmpowerID should use for sending any automated emails generated by the system.
- In the Email Address field, type the default email address EmpowerID should use for sending any automated emails generated by the system.
- Type the licensing key you received from EmpowerID in the License Key field and then click the Add License File (...) button.
- In the Open File dialog that appears, locate and select the EmpowerID License File (.eidlic) you received from EmpowerID and then click Open.
- From the SQL Connection tab of the EmpowerID Configurator, do the following:
- Type the name or IP address of the SQL server you are using for EmpowerID in the Server Name field.
Under Authentication, select Windows Authentication.
Info Or select Sql Azure to use a cloud-based Microsoft Azure SQL Database.
- Select the EmpowerID database from the Database Name drop-down.
- Test the connection by clicking Test Connection.
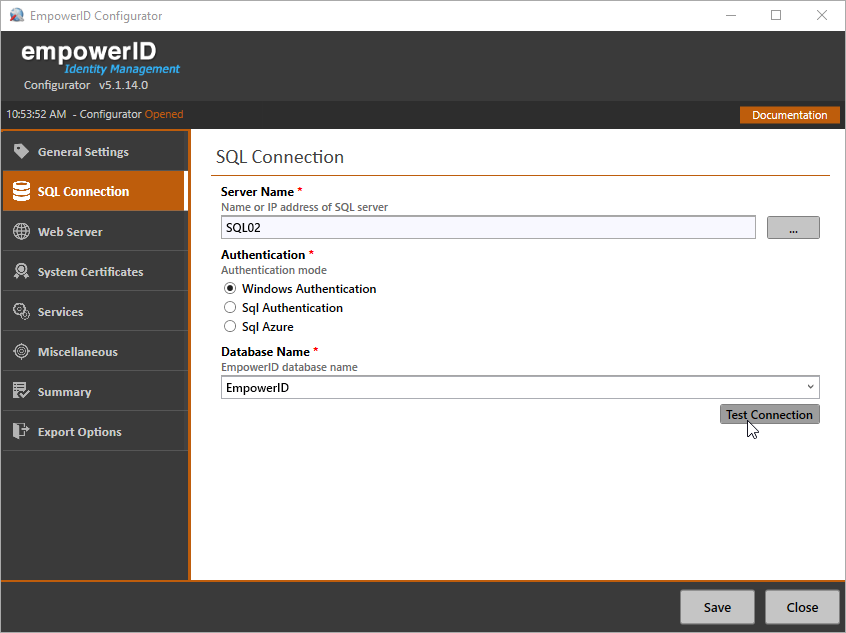
- Click OK to close the connection message.
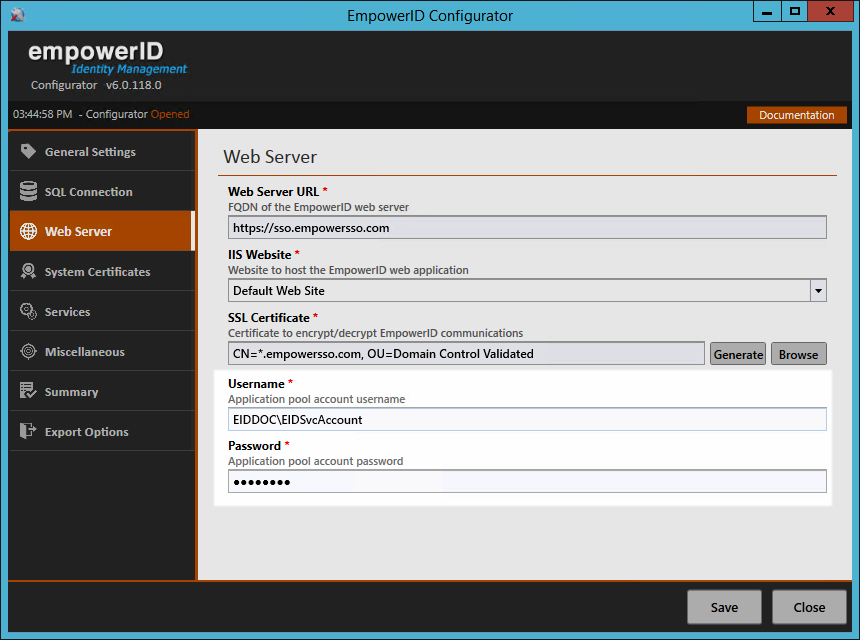
- From the Web Server tab of the EmpowerID Configurator, do the following:
- Type the FQDN of your EmpowerID Web server in the Web Server URL field. Be sure to use the https scheme.
- Select an existing Web site to host the EmpowerID Web application from the IIS Website drop-down or enter a name to create a new site. By default, EmpowerID selects the Default Web site.
- Under SSL Certificate, click Browse, choose whether to select the SSL certificate from the local certificate store or browse for the certificate PFX file and then click OK.
- Locate and select the SSL certificate you want to use for encrypting EmpowerID communications and click Open.
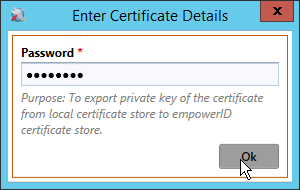
In the Password field of the Enter Certificate Details dialog that appears, enter a password and then click OK to close the dialog.
Info icon false A password is required for exporting the private key of the certificate from the local certificate store to the EmpowerID certificate store.
- Enter the Username and Password for the service account running the EmpowerID application pools.
- From the System Certificates tab of the EmpowerID Configurator, do the following:
Under Federation Certificate, click the Browse button and select the STS certificate EmpowerID should use for signing SAML assertions. The format for the certificate is PFX.
Tip This certificate can be the same certificate as the one you selected for SSL.
- In the Password field of the Enter Certificate Details dialog that appears, enter a password and then click OK to close the dialog.
- Under Server System Access Certificate, click the Generate button.
- In the Password field of the Enter Certificate Details dialog that appears, enter a password and then click OK to close the dialog.
- Review the information in the Certificate information window that appears and then click OK to close the window.
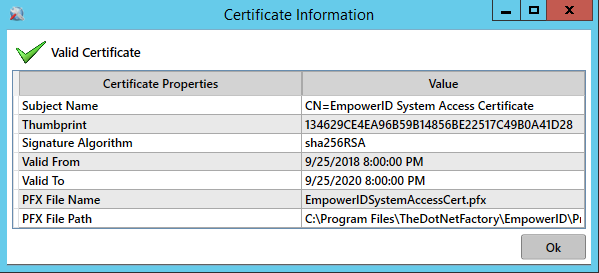 Image Modified
Image Modified
- From the Services tab of the EmpowerID Configurator, do the following:
- Underneath Windows Services, select each EmpowerID Windows service you want to install on the server, providing the user name and password for the service account identity that is to run each. These services include the following:
- EmpowerID Web Role Service — This service is required on all EmpowerID Web servers and is responsible for managing workflow-related services and global assembly cache content synchronization.
- EmpowerID Worker Role Service — This service must be on a server with IIS installed and is responsible for processing the EmpowerID Web Service Garden as well as running scheduled EmpowerID jobs and long running tasks, such as RBAC security compilation and inventory processing.
- EmpowerID Radius Service — This service provides RADIUS authentication for routers, switches and other RADIUS-compliant devices
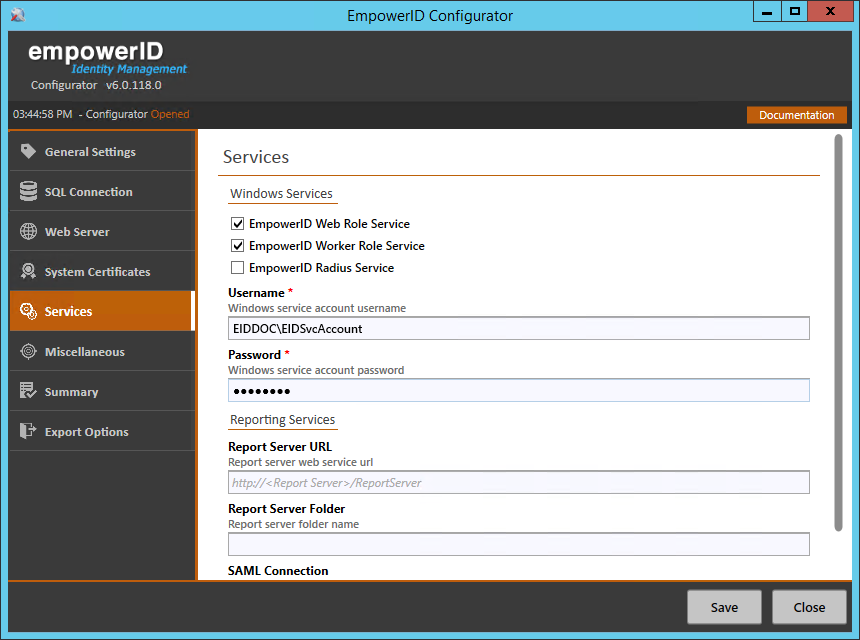
- If you are using Reporting Services for EmpowerID reports, underneath Reporting Services do the following:
- Type your report server web service URL in the Report Server URL field.
- Type the report server folder name in the Report Server Folder field.
- Type the SAML service provider connection for SSRS in the SAML Connection field.
- Underneath Windows Services, select each EmpowerID Windows service you want to install on the server, providing the user name and password for the service account identity that is to run each. These services include the following:
- From the Miscellaneous tab of the EmpowerID Configurator do the following:
To use a separate CDN (Content Delivery Network) in place of your default EmpowerID Web server to deliver the CSS, image and script files used by the EmpowerID Web application, type the URL to the CDN in the CDN Server URL field.
Info You can deploy EmpowerID's static content to a separate, resolvable server (with a different DNS), or you can deliver the content to a true CDN with replication and geographical load-balancing, such as those offered by AWS or Azure. Using a separate CDN in this way can improve response times because the browser caches the content and EmpowerID refrains from sending cookies on each call (as it does in the default configuration).
- Deselect Enable Minification if you do not want to minify the CSS and JavaScript files. Please note that minification is recommended.
- Click the Summary tab and review the changes you are about to make to the system and click Save when ready.
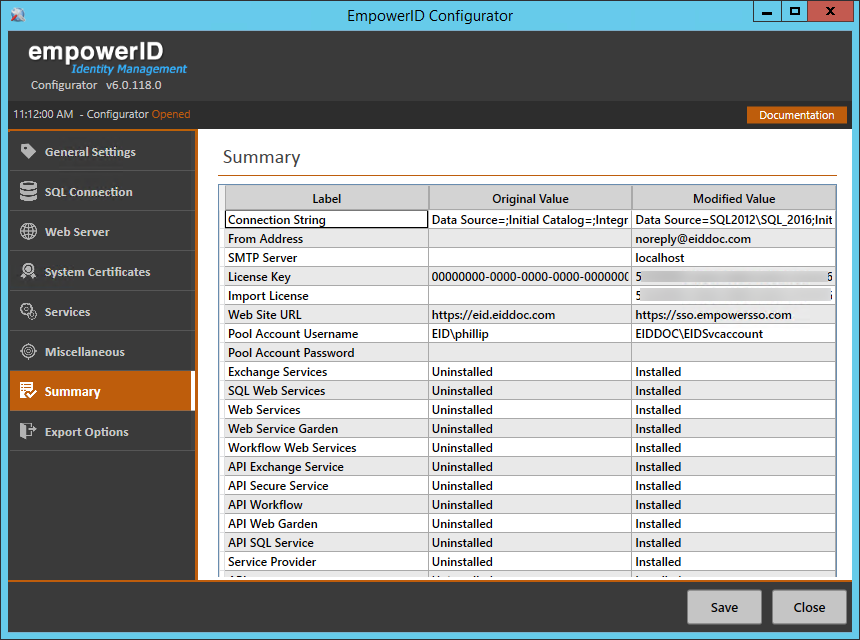
- Click Yes when asked if you want to apply all the changes.
- Click OK to close the Settings have been saved dialog.
- Optionally, from the Export Options tab, do the following:
- Select each file you want to export.
- Click the EmpowerID MSI ellipses button (...) and browse to the EmpowerID MSI file location on your server.
- Select the MSI and click Open.
- Select the folder for the exported files by clicking the Output Folder ellipses (...) button and browsing to the desired folder.
- Click Export and then click OK to close the Export Success message.
- From the Start menu, open Internet Information Services (IIS) Manager and do the following:
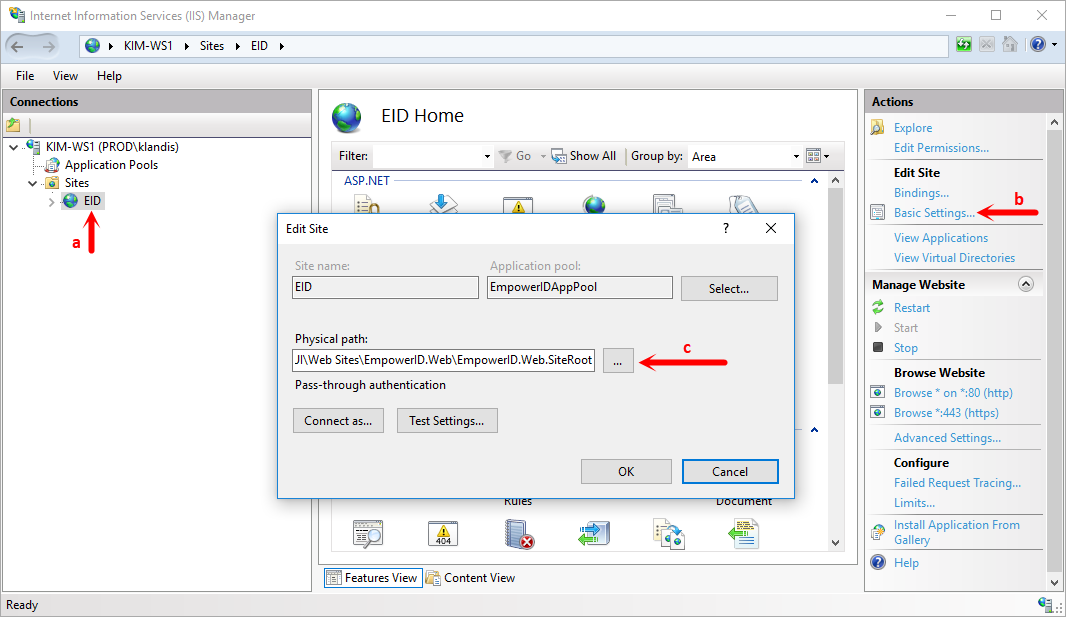
- In the Connections pane, expand Sites and select your EmpowerID site.
- In the Actions pane, click Basic Settings.
In the Edit Site dialog that appears, change the Physical Path to a path like the following:
C:\Program Files\TheDotNetFactory\EmpowerID\Web Sites\EmpowerID.Web.SiteRootInfo This connects EmpowerID to the latest web.config file that contains the most secure settings.
- Click OK to save the setting.
- Open Services.msc and stop the EmpowerID Web Role Service.
Now that you have installed and configured EmpowerID, the next step is to grant your dedicated EmpowerID service account the access to a number of folders and files on your EmpowerID server,. permissions for EmpowerID Windows services and local machine rights that account needs to run EmpowerID.
To grant local machine rights
The EmpowerID service account interacts with the local machine to perform a variety of maintenance procedures, including the distribution and maintenance of new workflows and other Workflow Studio published items. The service account needs the following access rights on the local machine:
- Install files in to the local global assembly cache (GAC)
- Read the registry
- Read certificates in the local certificate store
- Spin child processes
- Run C# compiler in the background if and when necessary
- create files in the temp folder
- Run remote PowerShell for Microsoft Exchange, if that Server Role is enabled in EmpowerID
- Create files and folders in the following locations:
- C:\ProgramData
- C:\Program Files\TheDotNetFactory\Programs
To grant these rights, run the following PowerShell cmdlet in administrative mode on the local machine.
| Info |
|---|
Be sure to replace the value for EIDSrvcPrinciple with the domain/principle for your environment. |
| Div | |||||||
|---|---|---|---|---|---|---|---|
| |||||||
|
After running the above cmdlet, verify that the service account has full permissions to the below files, folders and registry key. These permissions are needed to support installing files to the local global assembly cache (GAC):
- %windir%\assembly
- %windir%\Microsoft.Net\assembly
- %windir%\Microsoft.Net\Framework64\v4.0.30319\ngen.log
- EmpowerID Installation folder
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fusion\PublisherPolicy\Default
After running the above cmdlet, verify that the service account has read permissions to the following folder, as well as full permissions to the registry key. These permissions are needed to support the day-to-day operations of EmpowerID:
- %windir%\System32\inetsrv\config
- HKEY_LOCAL_MACHINE\SOFTWARE\TheDotNetFactory
| Info |
|---|
If any of the permissions are missing, you will need to manually set them. |
To grant rights to the application pool identity
The application pool identity requires read access to the EmpowerID web site folders. Additionally, the application pool identity needs to be able to restart the EmpowerID Windows services. To grant the necessary permissions to the Windows services do the following:
- Retrieve the SID for the EmpowerID Web Services application pool account.
Open a command prompt in administrative mode and display the security descriptor for the EmpowerID Web Role Service by running the below command for the EmpowerID Web Role Service. In the command, we are writing the output to a text file named "EIDWebRole_SecurityDescriptor."
Div class short-code-block Code Block language text theme Confluence sc sdshow "EmpowerID Web Role Service" > EIDWebRole_SecurityDescriptor.txt
Run the following command to open the text file:
Div class short-code-block Code Block language text theme Confluence notepad.exe > EIDWebRole_SecurityDescriptor.txt
You should see the following output in the text file:
Div Code Block language text theme Confluence D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)
Locate and copy the permissions for the Built-in administrators so that the file looks as follows:
Div Code Block language text theme Confluence D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)
In the second set of permissions for the Built-in administrators, replace BA with the SID of the application pool account so that the file looks similar to that shown below. Please note that the SID for your account will differ accordingly.
Div Code Block language text theme Confluence D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-1871625359-1900012290-2536039220-1591)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)
Return to the command prompt and set the new security permissions.
Div Code Block language text theme Confluence sc sdset D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-1871625359-1900012290-2536039220-1591)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)
Repeat steps 2 through 6 above for the EmpowerID Worker Role Service.
When ready, start the EmpowerID Web Role Service to GAC EmpowerID DLLs.
This completes installing EmpowerID for least privilege.Info Please note that full GAC'ing can take several minutes to complete. Ensure that all DLLs have been added to the GAC before running any EmpowerID Workflows or performing any further configuration of the system. You can view the results in the EmpowerIDServerGACReference table of the EmpowerID Identity Warehouse. When the process is completed, the number of records in the EmpowerIDServerGACReference table should be the same as those in the GACReferenceLibrary table.
| Div | ||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ||||||||||||||||||||||
|