Versions Compared
Key
- This line was added.
- This line was removed.
- Formatting was changed.
EmpowerID 2018 2019 has many new features, numerous enhancements, and multiple fixed issues to make the EmpowerID user experience better than ever.
| HTML Comment |
|---|
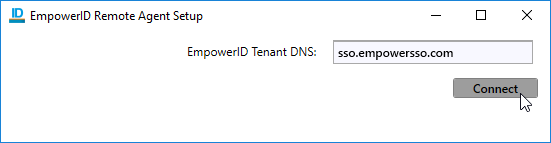
Cloud Gateway The EmpowerID Cloud Gateway enables your EmpowerID Cloud tenant to inventory and manage your on-premise systems without requiring ports to be opened on your firewall. The Cloud Gateway is a lightweight client that can be installed on a Windows desktop or server machine in your on-premise network. The Cloud Gateway client then makes a secure and encrypted outbound HTTPS connection to an EmpowerID queue in Azure as a bridge for communication between the EmpowerID Cloud servers and your on-premise network. You can install multiple Cloud Gateways on-premise for fault tolerance and increased performance. For more information, see Configuring the EmpowerID Cloud Gateway.
Mobile Phone Registration The EmpowerID Mobile App provides multi-factor authentication (MFA) and chatbot help. The authentication feature provides both push and passcode authentication. You can download the app from the Google Play Store and the Apple App Store for Android and iOS, respectively. You can register multiple devices to your EmpowerID account and you can register multiple accounts to the same device. For more information, see Using the EmpowerID Mobile App.
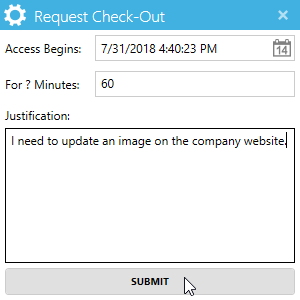
Privileged Application Launcher When a manager wants to delegate temporary access to a privileged application to an employee with otherwise limited access, sharing a password is not the most secure way to do so. The Privileged Application Launcher allows employees to submit requests to check out vaulted credentials for a specified number of minutes using their own password. For more information, see Installing the Privileged Application Launcher.
|
New Features
| Div | ||||
|---|---|---|---|---|
| ||||
Enhanced Privileged Session Manager |
Privileged Session Manager (PSM) is updated to record and monitor privileged sessions, and to be hosted as a Docker Swarm on local or cloud service locations. You can configure PSM to record session activity when users check out credentials for a managed computer, allowing Access Managers and other administrators to view what users do on the computer during a session, and to terminate a session if necessary. It is also updated to comply with new European Union GDPR laws. For more information, see the following topics:
- Checking out credentials and initiating a Privileged Session Manager (PSM) session (Checking Out Credentials and Initiating an RDP Session)
- Watching and monitoring a live PSM session (Viewing Privileged Session Details)
- Terminating a live PSM session (Terminating a Privileged Session)
- Turning off monitoring and recording to comply with new European Union GDPR laws (Creating Privileged Session Policies)



| Div | ||||
|---|---|---|---|---|
| ||||
More Core Functionality Moved to the Web Application |
More functionality is moving to the web application so that you can configure EmpowerID without using the EmpowerID Management Console. The Management Console retains some functionality in 2018, but now you can also perform many new functions in the web application, including:
- Mapping roles and locations (Mapping Locations)
- Setting server roles and server jobs (Configuring Server Roles)
- More system settings for configuring EmpowerID
- Creating account stores (/wiki/spaces/EIAG/pages/453181868)
- Attribute flow rules (Configuring Attribute Flow)


| Div | ||||
|---|---|---|---|---|
| ||||
More Connectors Out of the Box |
VMware ESXi
The ESXi connector allows organizations to bring the user, permissions, and roles data in their stand-alone VMware ESXi systems to EmpowerID, where it can be managed and synchronized with data in any connected back-end user directories. See VMware ESXi for more information.
Once connected, you can manage this data from EmpowerID in the following ways:
- Create new users
- Edit user attributes
- Delete users
- Create new roles and permissions
- Manage roles and permissions membership
- Delete roles and permissions

SAP
EmpowerID includes an SAP connector capable of connecting with the two main SAP modules used for managing identity information: ECC and HCM.
The ECC module stores information for accessing SAP, and the means for authorizing to SAP, which includes:
- action groups,
- profiles, and
- individual authorization objects.
The HCM module manages employees and often serves as the authoritative source for employee information, including employment status, location, roles and responsibilities. When EmpowerID connects to any one of these SAP modules, it creates a singular account store object for that module with configurable settings for specifying how EmpowerID is to manage the identity information. The Process SAP Group Owners permanent workflow monitors SAP action groups and processes SAP group owners.
For more information, see SAP.

ServiceNow
The ServiceNow connector lets you create, synchronize, and manage ServiceNow users, groups, roles, locations, companies, user roles, and group membership within EmpowerID. Once you connect to ServiceNow, your ServiceNow developers can configure service catalog requests to allow your ServiceNow users to request groups, memberships, et cetera, and have them go for approval in EmpowerID.
With the EmpowerID ServiceNow Connector, you can manage all of the following functions in ServiceNow.
Account Management
- Inventory ServiceNow users as EmpowerID accounts
- Create, update, and delete users
- Enable, disable, and change passwords of users
Group Management
- Inventory ServiceNow groups as EmpowerID groups
- Inventory ServiceNow group memberships as EmpowerID GroupAccounts
- Create, update, and delete groups
- Add and remove members of groups
Locations and Companies
- Inventory ServiceNow locations as EmpowerID ExternalOrgZones
- Inventory ServiceNow companies within the locations as EmpowerID ExternalOrgZones
Roles
- Inventory ServiceNow roles as EmpowerID ExternalOrgRoles
For more information, see ServiceNow.

Webex Enterprise
The Webex Enterprise connector allows organizations to manage and synchronize Webex Enterprise user data. Once connected, you can manage this data from EmpowerID in the following ways:
- Inventory users
- Provision new users with Provisioning policies or workflows
- Update users
- Enable or disable users
- Unlock users
- Reset user passwords

| Div | ||||
|---|---|---|---|---|
| ||||
Reverse Proxy NGINX Module |
The EmpowerID Reverse Proxy or microservices gateway is a dockerized NGINX module that is a key component of any Zero Trust or microservices security architecture. As a component of the EmpowerID WAM System, the Reverse Proxy stands in front of protected Web applications and Docker containers, restricting access to the resources served by those applications by intercepting all HTTP traffic bound for those applications, evaluating and processing each request using EmpowerID's hybrid RBAC / ABAC engine.
As a WAM component, the EmpowerID reverse proxy provides web environments with seamless access to all of the identity management facilities of EmpowerID. This means that organizations can use the EmpowerID reverse proxy to provide the same level of security for the resources that live on their web servers as they provide for the resources that live in their directories and other such similar resource systems.
The EmpowerID Reverse Proxy controls access to web applications and APIs without requiring the installation of an agent. To configure the reverse Proxy, an OpenID Connect OAuth application record is created in EmpowerID, with an associated SAML connection linked to it for use in defining attribute statements. The Reverse Proxy uses this OAuth connection when making API calls to the EmpowerID REST endpoints to retrieve its configuration and for making real-time ABAC access checks. Web applications protected by the Reverse Proxy are created in EmpowerID as web applications with their protected URLs and paths registered as "Application Subcomponents." RBAC and ABAC policies can be applied to determine who may have access to these subcomponents/URL paths. After creating the appropriate reverse proxy components in the EmpowerID Web interface, you configure the reverse proxy application files with the appropriate information for your environment.
The below diagram shows all the components and configuration files associated with the EmpowerID reverse proxy. Click the image for an expanded view.

| Div | ||||
|---|---|---|---|---|
| ||||
Responsible Parties |
EmpowerID now supports assigning and tracking responsible parties for key objects like accounts, groups, computers, management roles, locations, and shared credentials. This responsibility relationship differs from that of a Person owning an account. An account owned by a Person represents that person and serves as their personal account. Responsible parties are assigned to signify who is responsible for an IT object from a security and audit perspective. For more information, see Responsible Parties.

Any EmpowerID RBAC Actor Type can be assigned as the responsible party, but most organizations configure EmpowerID to only allow the assignment of a Person. The field that stores this assignment is called OwnerAssigneeID, and you can find it in each supported object's table.
You can assign responsibility for EmpowerID objects using the Responsible Party property on the Details page for the object, or you can bulk assign responsibility for a number of the same type of objects using an action found on the object type's View Many page. Once assigned, you can transfer responsibility from one party to another.
When a person is leaving or changing positions, you can transfer all of their responsibilities to another party. You can either do this manually, using the Transfer Responsibilities workflow, or automate the process in a Planned Leaver Event.
The following new request workflows support these new features:
- UpdateOwnerAssignee
- AssignOwnerForAccounts
- AssignOwnerForGroups
- TransferAccountOwner
- AssignOwnerForManagementRoles
- TransferAccountsOwner
- TransferGroupOwner
- AssignOwnerForComputers
- AssignOwnerForResources
- TransferResourceOwner

| Div | ||||
|---|---|---|---|---|
| ||||
Core Identity |
EmpowerID now supports the concept of a Core identity so that you can log in with different Person identities that are all linked to the same Core ID. Just as a person can have multiple user accounts in different external directories, so a core identity can have more than one persona. You can enable EmpowerID to create core identities when more than one person is discovered during inventory that shares the same name, birth date, or any attributes that you specify in the system settings. A person that is attached to a core identity is presented at login with a selection of personas to log in as, and once logged in, can switch between personas. The new ProvisionCoreIdentityBulk permanent workflow monitors the ProcessAccountInbox request workflow and provisions core identities as necessary. For more information, see Core Identities.


| Div | ||||
|---|---|---|---|---|
| ||||
Enhanced PAM Features |
Now you can use vaulted admin credentials in a PowerShell script (Retrieving Credentials in a PowerShell Session)


| Div | ||||
|---|---|---|---|---|
| ||||
New Group Membership Features |
Two new permanent workflows automate group membership processes to ensure that sensitive groups always have the right members.
- The new ContinouousRecertification permanent workflow constantly monitors membership changes in groups and generates recertification tasks for group owners. This ensures that access changes to sensitive groups comply with security policy.
- The GroupMembershipExpirationNotification permanent workflow monitors group membership expiration dates, and notifies group owners of expired memberships.

| Div | ||||
|---|---|---|---|---|
| ||||
New Audit and Clean-Up Features |
- Several new permanent workflows help your organization to stay up-to-date on audits and expired items.
- The Unreviewed Recertification Task Notification permanent workflow monitors unreviewed audit tasks, and notifies assigned reviewers of their unreviewed tasks.
- The Create Scheduled Certification Audit permanent workflow creates and runs any scheduled certification audits.
- The Close Revoke Re-certification Unreview Tasks After Due Date permanent workflow closes any revoke tasks that remain unreviewed beyond the recertification due date.
- The Check in Shared Credential permanent workflow monitors shared credential check-outs, and automatically checks them in when the requested time has expired.
- The ScheduledCredentialPasswordReset permanent workflow monitors password reset schedules for shared credentials and resets passwords at the specified times.
- The DeleteTemporaryPeopleCreatedDuringSignup permanent workflow monitors temporary people created during signup and deletes them after 60 minutes.
See the Workflow Library for a full listing of permanent workflows and request workflows.

| Div | ||||
|---|---|---|---|---|
| ||||
User Agreements |
You can now use HTML to attractively style user agreements (two are included out of the box) to display to users when they sign in. For more information, see Setting Up Password Manager Policies.


| Div | ||||
|---|---|---|---|---|
| ||||
Safely Remove Group Memberships Flagged as CreatedFromAccountStore When an RBAC Policy Is Removed |
When there is an RBAC policy for group enforcement (other than full enforcement), a flag marks any affected group accounts as RBACAssigned. If the group account later loses the policy, the RBACAssigned flag gets set back to false but the group membership remains in place to prevent the accidental removal of valid memberships when someone is testing policies and then removing them.
Since many companies do want to remove the membership once policies are removed, we added a new date field called RbacAssignmentConfirmationDate. This date is only set for group accounts that are flagged as CreatedFromAccountStore and are subsequently flagged as RBACAssigned. The date field is set to seven days after the RBACAssigned flag is set to true, and it represents the time until the RBAC-assigned group account becomes fully managed by EmpowerID.
- If the RBAC policy that flags the group account as RBACAssigned is rolled back before the seven days expires, then the RBACAssigned flag is set to false, the date is cleared, and the group account remains.
- If the RBAC policy that flags the group account as RBACAssigned is rolled back after the confirmation date, then the group account is removed, the same as any other policy assignment.

| Div | ||||
|---|---|---|---|---|
| ||||
Single Login Experience When Using the EmpowerID Reverse Proxy |
The OAuth Identity Provider (IdP) login page now provides the same user experience as other login pages. The following changes make for a more user-friendly experience:
- Removed all OAuth authentication cookie references.
- Changed handling of IdP authentication cookies so that logging in twice is not required.
- Updated OAuth browser flows to support external IdP authentication.
- Added IdP tiles such as Facebook, GitHub, Salesforce, et cetera, to appear on the OAuth login page based on the IPDomain settings.

| Div | ||||
|---|---|---|---|---|
| ||||
Security Upgrades |
EmpowerID 2018 includes numerous security updates in response to evolving changes in security needs.


| Div | ||||
|---|---|---|---|---|
| ||||
Redesigned UI |
The theme of the EmpowerID web application has been redesigned, and many new pages have been added.
The IT Shop has a new theme.

EmpowerID 2018 has a new ServiceNow Manager page.

All Features and Enhancements
| Feature | Description | Documentation |
|---|---|---|
| EMPOWERID-3 | As a system administrator, I want to be able to retrieve vaulted privileged credentials from EmpowerID for use in my PowerShell interactive sessions so that I can run PowerShell actions as an admin even though I am not an admin to support least privilege | Retrieving Credentials in a PowerShell Session |
| EMPOWERID-34 | As an EmpowerID customer, I want to easily install the EmpowerID Cloud Gateway | Configuring the EmpowerID Cloud Gateway |
| EMPOWERID-35 | As an EmpowerID customer, I want to register my EmpowerID Cloud Gateway and have it immediately work | Configuring the EmpowerID Cloud Gateway |
| EMPOWERID-38 | As an EmpowerID end user, I want to register my mobile phone during the login process | Registering a Mobile Device |
| EMPOWERID-40 | As an EmpowerID end user, I want to delete a registered mobile phone | Deleting a Registered Mobile Device |
| EMPOWERID-41 | As an EmpowerID end user, I want to edit the name of a registered mobile phone | Editing the Name of an Account |
| EMPOWERID-42 | As an EmpowerID end user, I want to perform push MFA and approve/reject on my registered mobile phone | Sending a Push |
| EMPOWERID-43 | As an EmpowerID end user, I want to perform OATH MFA using the code on my registered mobile phone | Submitting an Authentication Code |
| EMPOWERID-78 | As an end user, I would like to initiate an RDP session to a server for which I have checked out an applicable credential | Checking Out Credentials and Initiating an RDP Session |
| EMPOWERID-66 | As an EmpowerID system administrator, I want to run an all-in-one Docker instance of EmpowerID. | |
| EMPOWERID-67 | As an EmpowerID system administrator, I want to run a split multi-service Docker EmpowerID farm. | |
| EMPOWERID-80 | As a security admin, I would like to watch and monitor a live PSM session | Viewing Privileged Session Details |
| EMPOWERID-81 | As a security admin, I would like to watch a recorded PSM session | Viewing Privileged Session Details |
| EMPOWERID-82 | As a security admin, I would like to terminate a live PSM session | Terminating a Privileged Session |
| EMPOWERID-86 | As an EmpowerID admin, I would like to create an AD LDS ADAM Account Store connection in the web | AD LDS (ADAM) |
| EMPOWERID-88 | As an EmpowerID admin, I would like to create an SAP ECC Account Store connection in the web | SAP |
| EMPOWERID-89 | As an EmpowerID admin, I would like to create an SAP HCM Account Store connection in the web | SAP |
| EMPOWERID-90 | As an EmpowerID admin, I would like to create an Office 365 Account Store connection in the web | Office 365 |
| EMPOWERID-92 | As an EmpowerID admin, I would like to create a ServiceNow Account Store connection in the web | ServiceNow |
| EMPOWERID-98 | As a security admin, I want to report on all user accounts that do not have a valid owner or responsible Person | Administering Account Responsibility |
| EMPOWERID-99 | As a security admin, I want to transfer all owned user accounts (ownerassigneeid) from one person to another | Transferring Responsibility for Accounts |
| EMPOWERID-100 | As a security admin, I want all owned resources of any type (ownerassigneeid) to automatically transfer to a new person in the automated Leaver process | Automating Responsibility Transfer |
| EMPOWERID-104 | As a security admin, I want to report on all sensitive groups that do not have a valid owner or responsible Person | Administering Group Responsibility |
| EMPOWERID-105 | As a security admin, I want to transfer all owned groups (ownerassigneeid) from one person to another | Transferring Responsibility for Groups |
| EMPOWERID-107 | As an EmpowerID developer, I want all requests to my customer REST endpoint to be signed and encrypted. | Overview of JSON Signing and Encryption |
| EMPOWERID-108 | As an EmpowerID developer, I want to leverage an existing documented sample app to learn how to send signed and/or encrypted requests to an EmpowerID REST endpoint. | JSON Signing and Encryption Walkthrough |
| EMPOWERID-112 | As an EmpowerID system admin, I would like to easily deploy my NGINX Reverse Proxy as a set of Docker containers | Configuring the Reverse Proxy for the Web Application |
| EMPOWERID-114 | As a security admin, I would like to enforce authentication and MFA for a simple web site or application that does not require it | |
| EMPOWERID-118 | As a security admin, I would like to control access to specific pages in a SAML application and only allow users assigned access in EmpowerID to view them | |
| EMPOWERID-119 | As a security admin, I would like to control access to a specific page in a SAML application using an attribute-based rule where the Person is Tagged "Trusted" | |
| EMPOWERID-122 | As a system administrator, I want to easily install and configure the Privileged Application Launcher software | Installing the Privileged Application Launcher |
| EMPOWERID-123 | As an end user, I want to browse a list of privileged credentials and request to check one out for use | Installing the Privileged Application Launcher |
| EMPOWERID-124 | As an end user, I want to right-click on an application shortcut and launch an application using a checked out privileged credential | Installing the Privileged Application Launcher |
| EMPOWERID-125 | As an end user, I want to browse the list of applications displayed in the PAL and launch one using a checked out privileged credential | Installing the Privileged Application Launcher |
| EMPOWERID-137 | As a security admin, I want to easily bulk assign a person as an owner for accounts that do not have a valid owner or responsible Person (ownerassigneeid) | Transferring Responsibility for Accounts |
| EMPOWERID-138 | As a security admin, I want to easily bulk assign a person as an owner for groups that do not have a valid owner or responsible Person (ownerassigneeID) | |
| EMPOWERID-209 | As an end user, I want to see applications that I have granted OAuth access and have the ability to revoke their access | Managing Access Tokens |
| EMPOWERID-257 | As a security admin, I want to report on all management roles that do not have a valid owner or responsible Person | Administering Management Role Responsibility |
| EMPOWERID-258 | As a security admin, I want to report on all computers that do not have a valid owner or responsible Person | Administering Computer Responsibility |
| EMPOWERID-259 | As a security admin, I want to easily bulk assign a person as an owner for computers that do not have a valid owner or responsible Person (ownerassigneeID) | Administering Computer Responsibility |
| EMPOWERID-260 | As a security admin, I want to easily bulk assign a person as an owner for management roles that do not have a valid owner or responsible Person (ownerassigneeID) | Administering Management Role Responsibility |
| EMPOWERID-297 | As an EmpowerID admin, I would like accounts to be created automatically for users requesting group membership in a system for which they do not yet have an account | |
| EMPOWERID-383 | As an end-user, I would like to be able to switch between my various types of EmpowerID person identities without being forced to log in again | Enabling Persona Switching |
| EMPOWERID-437 | As an EmpowerID consultant, I would like to easily and simply configure my customer's EmpowerID instance to federate with Microsoft ADFS | |
| EMPOWERID-547 | As a security admin, I want to view a Person and see all of the Resources (Accounts, Groups, Management Roles, Shared Credentials, Computers) for which they are the responsible person (OwnerAssigneeID Direct) | Viewing a Person's Responsibilities |
| EMPOWERID-642 | As a visitor to the EmpowerID website, I would like to be informed about the use of cookies on the site | |
| EMPOWERID-671 | As an EmpowerID admin, I want to be able to create a tracking-only account store in the web | Tracking-Only Account Store |
| EMPOWERID-693 | As a security architect, I want my EmpowerID environment to be protected from attacks by hardening the EmpowerID servers to the best degree possible | |
| EMPOWERID-705 | As an administrator, I want to be able to configure CORS | Software Requirements |
| EMPOWERID-767 | Security enhancement | |
| EMPOWERID-770 | Security enhancement | |
| EMPOWERID-778 | Security enhancement | |
| EMPOWERID-783 | Security enhancement | |
| EMPOWERID-787 | Security enhancement | |
| EMPOWERID-792 | As an EmpowerID admin, I want to create an AWS account store in the web | Amazon Web Services |
| EMPOWERID-798 | Security enhancement | |
| EMPOWERID-799 | Security enhancement | |
| EMPOWERID-823 | As an EmpowerID admin, I want to create a Windows Local account store | Adding Local Windows Servers |
| EMPOWERID-827 | As an EmpowerID admin, I would like to create an UltiPro account store | UltiPro |
| EMPOWERID-846 | As an EmpowerID executive, I would like to ensure that Person passwords are encrypted using the most secure encryption feasible | |
| EMPOWERID-851 | As a compliance officer, I would like an attractively styled Usage Agreement | Setting Up Password Manager Policies |
| EMPOWERID-852 | As a compliance officer, I would like to have two possible user agreements during login for tracking | Setting Up Password Manager Policies |
| EMPOWERID-853 | As a product manager, I would like to have user friendly trees with styles to match the ASP.NET Zero template | |
| EMPOWERID-893 | As an EmpowerID admin, I would like to localize the extension attribute values for a person with different translations than extension attribute values for other object types | |
| EMPOWERID-989 | As a security admin, I would like to see all of the Resources for which a specified person or any person linked to their core identity is the responsible party | |
| EMPOWERID-991 | As an end user or admin, I would like to see all of the accounts owned by any of my Person objects linked to my core identity from the person view one page | |
| EMPOWERID-995 | As a product manager, I would like a more attractive and intuitive "Choose An Authentication Method" screen | |
| EMPOWERID-1166 | As an end user, on the Applications > Login page, if I have no applications, I would like a button that takes me to the IT Shop to find applications | |
| EMPOWERID-1177 | As a security admin, I would like to remove the EmpowerID product name from the default SAML connection | |
| EMPOWERID-1217 | As a user, when I click the login button, I want to see a loading spinner in the button | |
| EMPOWERID-1229 | As a user, I would like a loading spinner to appear when I click the login button | |
| EMPOWERID-1274 | As a workflow developer, I would like as much detailed information as possible when an error occurs in a workflow |
Fixed Issues
| Fixed Issues | Fixed Issues |
|---|---|
| EID-14819 | Removing a Management Role from a Person Workflow does not run - the user is not removed from the Management Role through the IT shop |
| EID-14762 | EID 6.0.78.0 Workflow Studio - Unable to add a new package |
| EID-13586 | Delegate Workflow task causes a "Request workflow 0 not found" error with SetBusinessProcessTaskDelegate |
| EID-13255 | The Visibility Filters find grid shows some pages with no data |
| EID-14807 | EID 6.0.83.0 UI Discrepancy - Default Attribute Policy has a different option name in the grid than in the creation page |
| EID-14977 | EID - Request Description does not match the activity (Edit Value Attribute) |
| EMPOWERID-228 | EMPOWERID-98 Error displayed when we try to click on any Logon Name on the Reports page |
| EMPOWERID-788 | EMPOWERID-766 Security update |
| EMPOWERID-800 | Security update |
| EMPOWERID-802 | Security update |
| EMPOWERID-809 | Enable CORS for Web CDN |
| EMPOWERID-811 | Security update |
| EMPOWERID-812 | Security update |
| EMPOWERID-813 | Security update |
| EMPOWERID-915 | EMPOWERID-567 EID 6.0.83.0 - Password manager policy applying incorrectly for account password reset |
Upgrading EmpowerID
EmpowerID freely provides hotfixes to address known issues. We also offer upgrades with new functionality in the form of new builds. When installing a hotfix or a newer version of EmpowerID, you can add the enhancements to your environment without losing preexisting data and configuration models.
| Warning |
|---|
Save any customizations to EmpowerID workflows in a custom package to avoid having the restoration process overwrite your custom workflows. |
When upgrading EmpowerID, you must be logged in as a user with rights to alter the EmpowerID database on the target SQL server.
You can upgrade to the latest build using the steps in the /wiki/spaces/E2D/pages/293306612 (opting NOT to delete the database) and Installing and Licensing EmpowerID topics. The only new prerequisites are the following.
- Install .NET Framework 4.7 on each server.
- Install Microsoft IIS CORS and URL Rewrite modules on each server. (Detailed in the installation topic.)
Product Support
EmpowerID provides support to all customers who have a trial version of an EmpowerID product or who have purchased a commercial version with a valid Software and Maintenance support contract. By purchasing Software Maintenance and Support, you have access to any upgrades that are released within a 12-month period and have email access to our product team to resolve any issues that may arise.
For further information on Software Maintenance and Support, please contact us by email at sales@empowerID.com.
Online Support
Registered users may submit cases online and track their status. If you are a registered user, you may submit and view the status of cases at any time.
Contacting Support
To contact a support representative, you may send an email to support@empowerID.com or contact us by phone at +1 (877) 996-4276.
EmpowerID offers support for the most recently released version of the Software Program and one version prior. This means that with the release of EmpowerID 2018, support is offered for EmpowerID 2016 and EmpowerID 2018.
| Div | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| |||||||||||
|