Versions Compared
| Version | Old Version 6 | New Version Current |
|---|---|---|
| Changes made by | ||
| Saved on |
Key
- This line was added.
- This line was removed.
- Formatting was changed.
| Insert excerpt | ||||||
|---|---|---|---|---|---|---|
|
EmpowerID Azure connector allows organizations to bring the instances in their Azure subscription to EmpowerID, where they can be managed as computer objects, giving authorized users the ability to start, stop and delete Azure instances from EmpowerID. To connect EmpowerID to Azure in this way involves doing the following procedures:
Creating a service management certificate for Azure
Uploading the service management certificate to Azure
Adding your Azure Certificate to the Personal Certificate Store on an EmpowerID Web server
Exporting the Azure Certificate from the Person Certificate Store to your EmpowerID Web server in Base-64 Encoded format
Adding the Azure certificate to the EmpowerID certificate store
Creating an EmpowerID Person as a service account for the Azure connection
Mapping the Azure certificate to the EmpowerID Person you create
Creating the Azure connection in EmpowerID
| Info |
|---|
In order to connect EmpowerID to Azure, you need to have an Azure subscription with a management certificate and provide to EmpowerID the following information
|
Create a service management certificate for Azure
| Tip |
|---|
For instructions on creating the management certificate for Azure, see Microsoft's article at https://docs.microsoft.com/en-us/azure/cloud-services/cloud-services-certs-create. |
Upload the service management certificate to Azure
| Tip |
|---|
For instructions on uploading the management certificate for Azure, see Microsoft's article at https://docs.microsoft.com/en-us/azure/azure-api-management-certs. |
Add your Azure certificate to the Personal certificate store
On your EmpowerID Web server, open MMC.
From MMC, add the Certificates snap-in for the local computer if needed.
Expand the Certificates node, right-click Personal, point to All Tasks and click Import.
In the Certificate Import Wizard that appears, click Next.
Click Browse and locate your certificate.
In the Open window that appears, select your certificate and click Open.
Continue through the Certificate Import Wizard until completed.
Next, export the certificate to a location on your server in base64-encoding format as demonstrated below. You will need this when creating the Azure connection in EmpowerID.
Export the Azure Certificate using Base-64 Encoding
From the Personal store, right-click the Azure certificate you just imported and select All Tasks > Export from the context menu.
In the Certificate Export Wizard that appears, click Next.
Select No, do not export the private key and click Next.
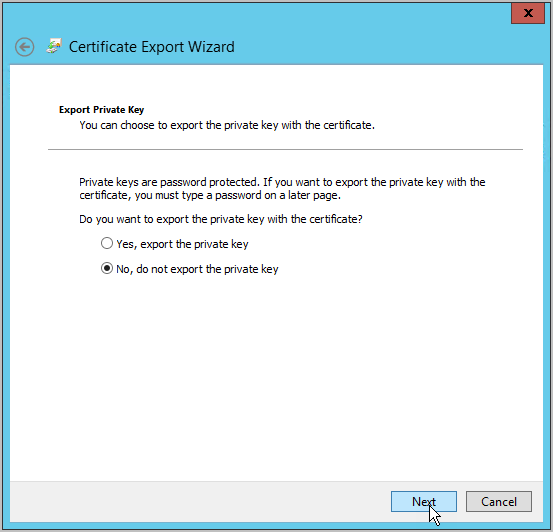
Select Base-64 encoded X.509 (.CER) and click Next.
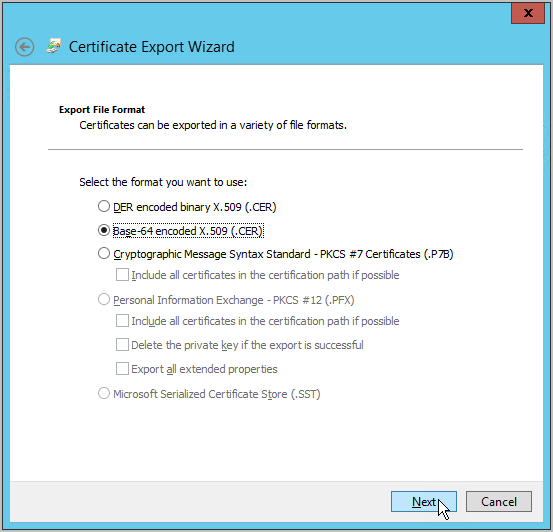
Select an export location, naming the exported certificate accordingly and click Next.
Click Finish to complete the export.
Open the exported certificate in a text editor and remove the first and last lines (----BEGIN CERTIFICATE---- and ----END CERTIFICATE----).
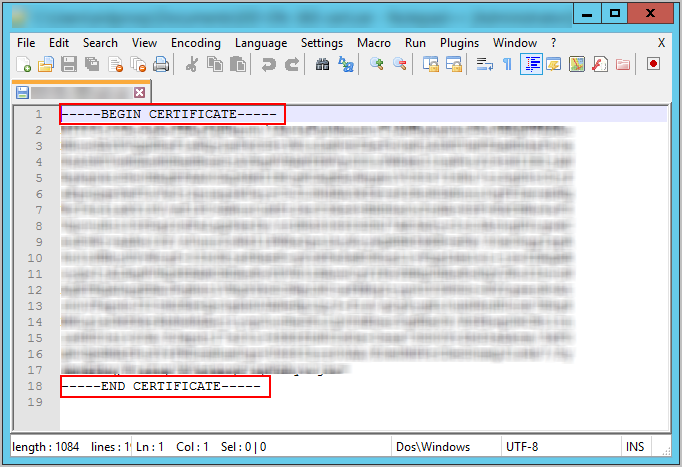
Save your changes.
Add the Azure certificate to the EmpowerID certificate store
Open the EmpowerID Certificate Manager utility. In a default installation of EmpowerID, the path to the executable is location at:
C:\Program Files\TheDotNetFactory\EmpowerID\Programs\EmpowerID.CertificateManager.exeFrom the Import tab of the EmpowerID Certificate Manager, select Upload from Certificate File.
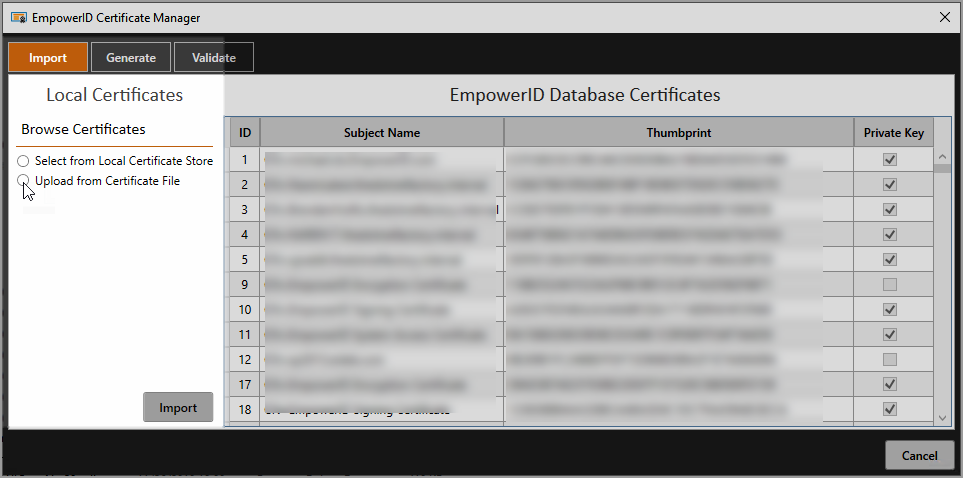
Browse for and select the Azure certificate (.cer file type) for your environment.
Click Import.
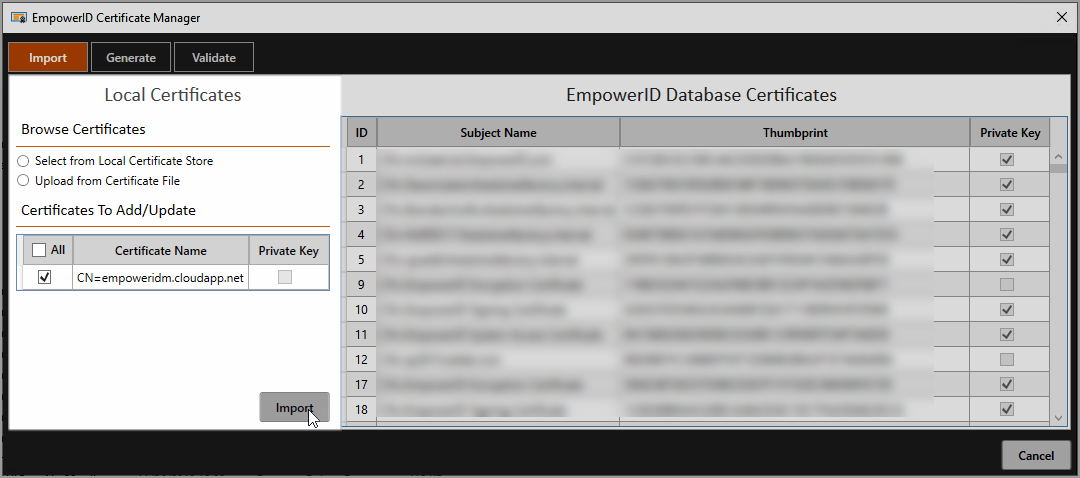
Click OK to close the success message box that appears.
Close the EmpowerID Certificate Manager.
Create an EmpowerID Person account for the Azure connection
Log in to the EmpowerID Web application as an administrator.
On the navbar, expand Identity Administration and click People.
On the Find Person page that appears, click the Create Person Simple Mode action link.
Insert excerpt IL:Create Person Simple Mode Action IL:Create Person Simple Mode Action nopanel true Enter a first name and a last name for the Person account in the First Name and Last Name fields, respectively. As this Person account serves as an identity for the Azure connection, you should name it accordingly. In our example, we are naming the Person "Azure Proxy."
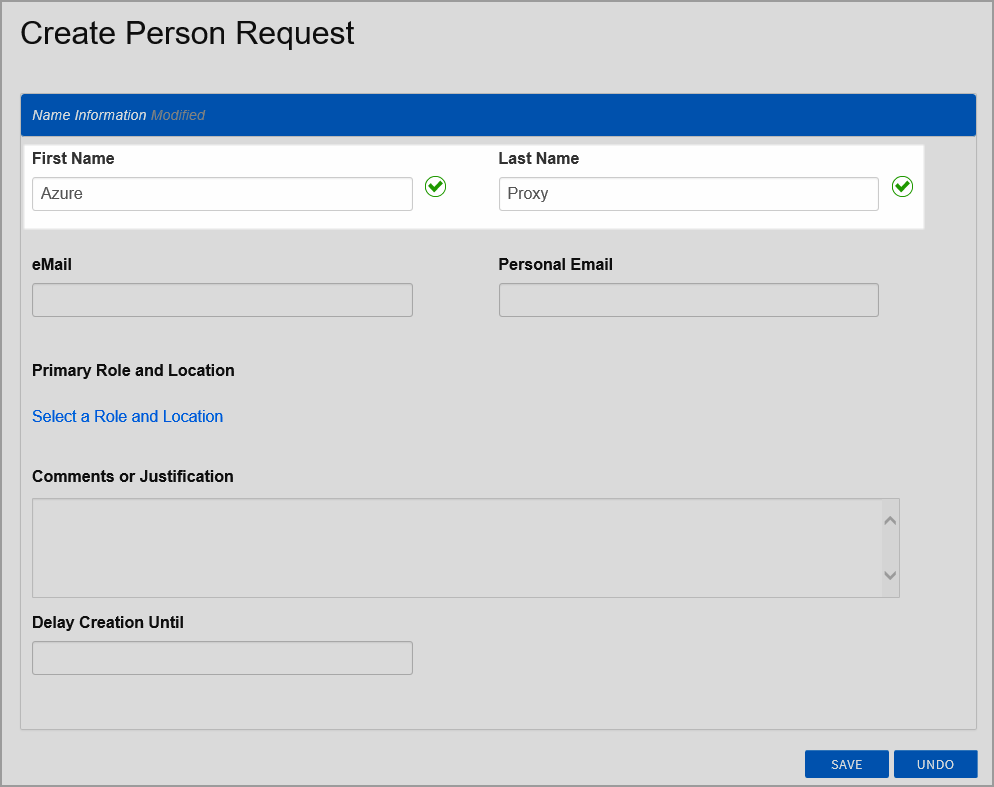
Underneath Primary Business Role and Location, click Select a Role and Location.
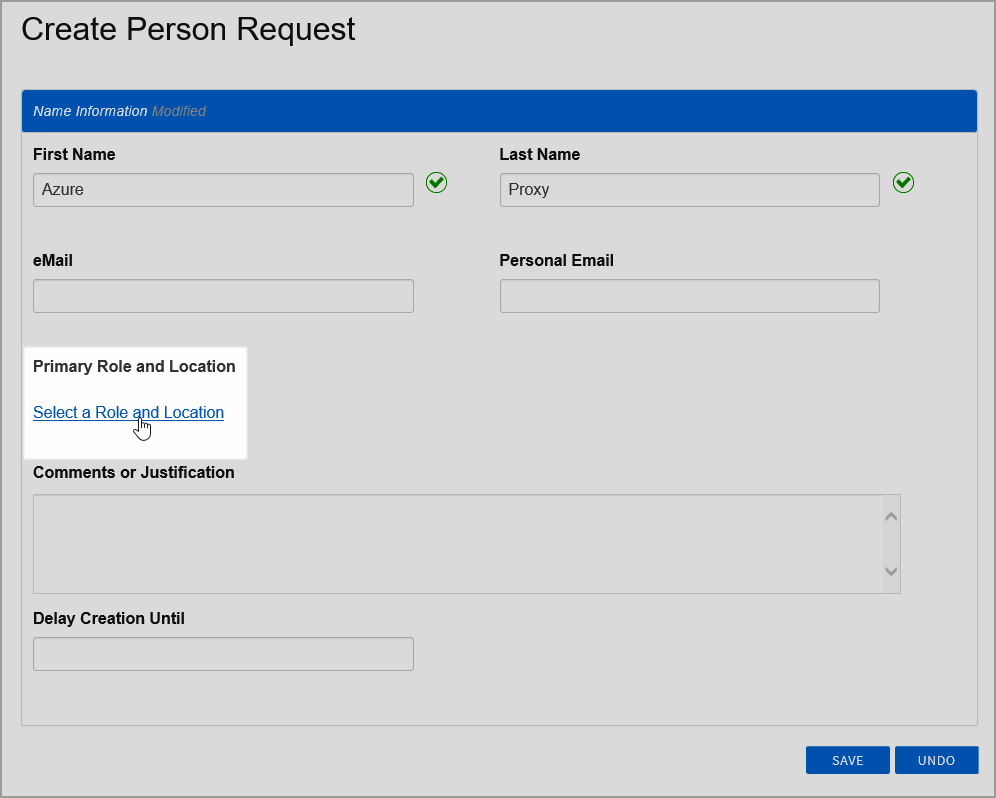
In the Business Role pane of the Business Role and Location selector that appears, type Temporary Role, press ENTER and then click Temporary Role to select it.
Click the Location tab to open the Location pane and then type Temporary Location, press ENTER and click Temporary Location to select it.
Click Select to select the Business Role and Location for the Person account and close the Business Role and Location.
Click Save to create the EmpowerID Person.
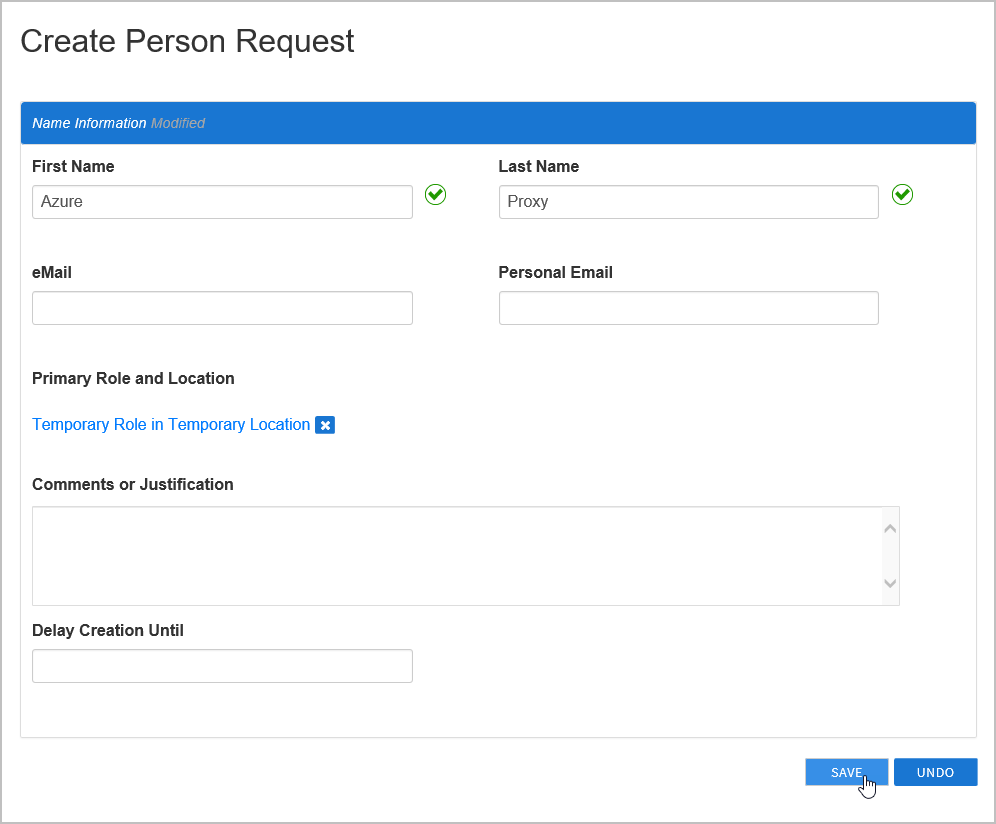
Next, map the Azure certificate to the Person you just created.
| Insert excerpt | ||||||
|---|---|---|---|---|---|---|
|
Create the Azure account store in EmpowerID
On the navbar, expand Admin > Applications and Directories and then click Account Stores and Systems.
On the Account Stores page, click Create Account Store.
Insert excerpt IL:Create Account Store Screen IL:Create Account Store Screen nopanel true Under System Types, search for Azure Subscription.
Click the record for Microsoft Azure Subscription to select it and then click Submit.
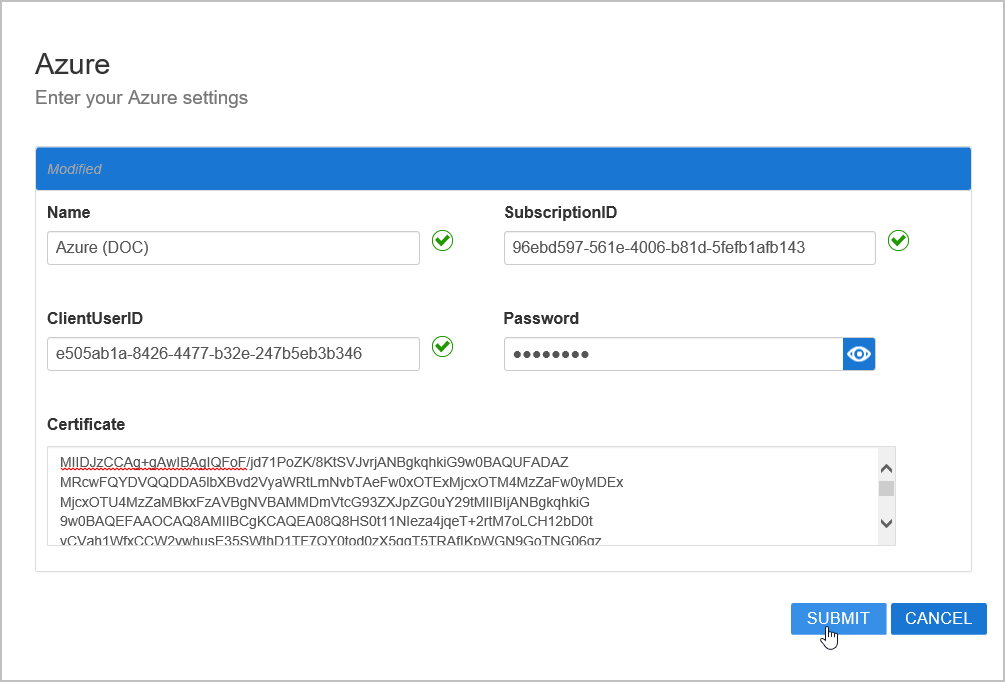
In the Azure Settings page that appears, fill in the following information:
Name — Name for the connector
SubscriptionID — Your Azure Subscription ID
Client User ID — The user id of an Azure administrator. This account is the proxy account that EmpowerID uses to inventory the Azure instances.
Password — Password for the above Azure administrator
Certificate — The Base-64 encoded format of your Azure certificate
Click Save.
EmpowerID creates the account store and the associated resource system. The next step is to configure the attribute flow between the account store and EmpowerID.
| Insert excerpt | ||||||
|---|---|---|---|---|---|---|
|
Now that the attribute flow has been set, the next steps include configuring the account store and enabling EmpowerID to inventory it.
To configure account store settings
On the Account Store and Resource System page, click the Account Store tab and then click the pencil icon to put the account store in edit mode.
This opens the edit page for the Box account store. This page allows you to specify the account proxy used to connect EmpowerID to your Box account as well as how you want EmpowerID to handle the user information it discovers in Box during inventory. Settings that can be edited are described in the below table.Insert excerpt IL:Account Store Settings IL:Account Store Settings nopanel true Edit the account store as needed and then click Save to save your changes.
Next, enable the Account Inbox permanent workflow to allow the Account Inbox to provision or join the user accounts in Box to EmpowerID Persons as demonstrated below.
| Tip |
|---|
EmpowerID recommends using the Account Inbox for provisioning and joining. |
| Insert excerpt | ||||||
|---|---|---|---|---|---|---|
|
| Insert excerpt | ||||||
|---|---|---|---|---|---|---|
|
| Insert excerpt | ||||||
|---|---|---|---|---|---|---|
|
| Div | ||||||||
|---|---|---|---|---|---|---|---|---|
| ||||||||
IN THIS ARTICLE
|