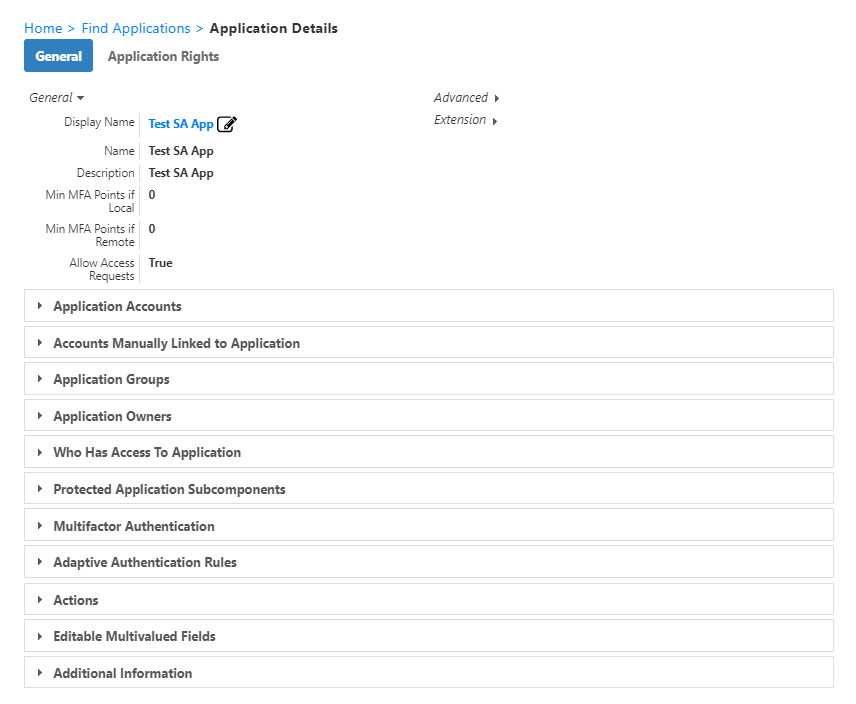
To register an application for use with EmpowerID, you must first create a record for the application in the EmpowerID Identity Warehouse and specify configuration settings for it. You do this on the Manage Applications page by clicking the Create Application action link. This opens the Create Application page, which contains tabs and fields where you can enter information about the application. This topic provides an overview of this page.
The following image shows part of the Create Application page that appears when you register an application in EmpowerID.
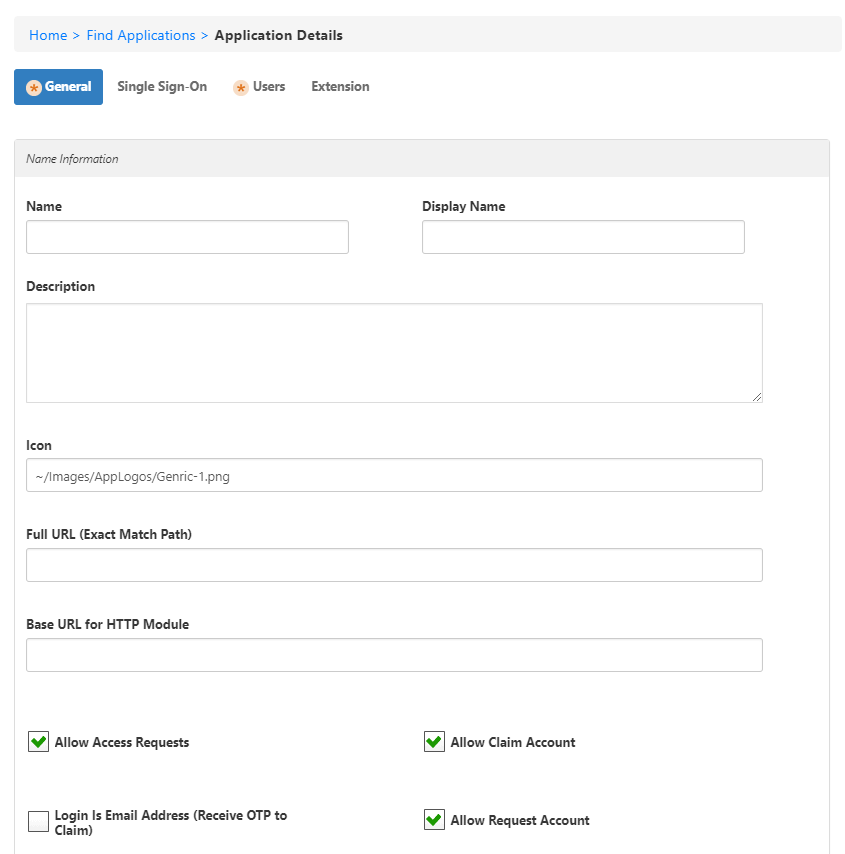
The page has four tabs:
General — This section provides fields for specifying general application settings common to most application types.
Single Sign-On — If the application is a service provider that requires users authenticate to access resources, you use this section to configure Single Sign— On (SSO) for the application.
Users — This section provides settings for linking the application with an account store.
Extension – This section provides space for up to fifteen additional custom attributes that are specific to your application.
General Tab
This section provides fields for specifying general application settings common to most application types.
- Name — This is the name of application.This field is required.
- Display Name — This is the name of the application that displays to users on the EmpowerID User Interfaces.This field is required.
- Description — This is a description of the application.This field is required.
- Icon — This is the icon associated with the application. EmpowerID links the icon to an application tile that users can click to access the application once they have been granted an account for the application. The URL specifies the specific tile that is displayed for the SSO application.
- Full URL (Exact Match Path) — When protecting Web-based resources, specify an exact URL to restrict. To restrict access to the specific page www.empowerid.com/customers/reports.aspx, type www.empowerid.com/customers/reports.aspx here.
- Base URL for HTTP Module — This specifies the URL the user types in their browser to go to the application.
- Allow Access Requests — Specifies whether the application appears in the IT Shop. Items in the IT Shop can be requested and/or claimed by users.
- Allow Claim Account — Specifies whether users can claim ownership of an application account from the IT Shop. Users who claim accounts, must provide their login from the SSO application as EmpowerID passes the login to the application as an assertion of the user's identity. If the login is incorrect, the assertion will be rejected by the application.
- Login Is Email Address — Specifies whether the application expects usernames to be formatted as email addresses.
- Allow Request Account — Specifies whether users can request an account in the application. All account requests route to the application owner and other delegated users with the authority to provision new accounts in the application.
- Make me the Application Owner — Specifies whether the person creating the application is the application owner. Application owners can grant or deny access requests.
- Configure Advanced Claim and Request Account Options — Specifies whether custom pages and workflows are to be used for claiming, requesting, editing and deleting application accounts. If this option is selected, the page displays additional settings that can be used for setting the custom pages and workflows to be used.
- Is Fulfillment Group Centric — With tracking-only applications, select this option to send a separate fulfillment request to each group owner. Clear this option to send just one request to the application owner.
Fulfillment Workflow — When you select Is Fulfillment Group Centric, click in this field and press Enter to select the ProcessGroupFulfillment workflow tile or any custom workflow you may have. Otherwise, it uses the default workflow and sends a single request to the application owner.
To have a custom workflow appear as an option here, add the word "fulfillment" to the custom workflow's Search Tags. |
Single Sign-On Tab
If the application is a service provider that requires users authenticate to access resources, you can configure Single Sign-On (SSO) for the application from this section of the form.
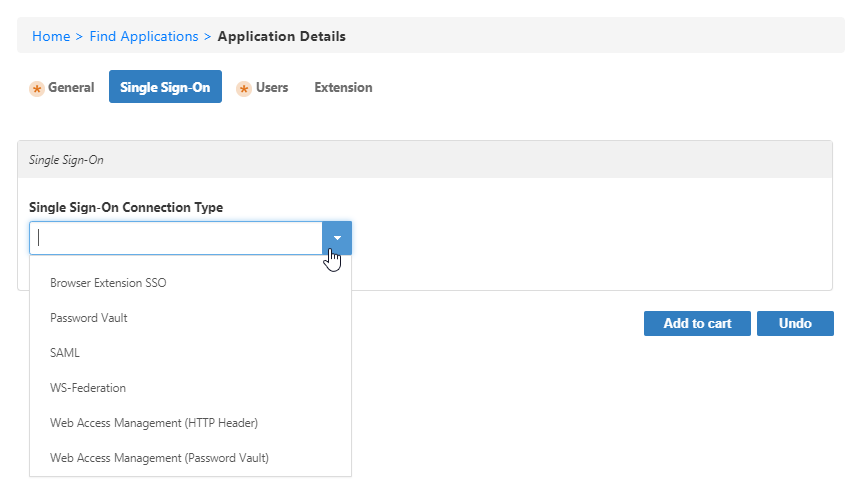
Single Sign-On Connection Type — Specifies the SSO connection type for the application, when applicable. Depending on the type selected, the form provides different options.

Allows users to SSO into their personal applications without requiring federation between those applications and EmpowerID. The Browser Extension SSO application "learns" the login screen for any Web application and allows users to vault their credentials for those applications for easy SSO. |
Used for applications that do not support the use of SAML or WS-Federation, but require users submit their credentials via a form on a Web site before access to the site is granted. For Password Vaulted applications, EmpowerID securely stores the usernames and passwords associated with each user's account in that application in the EmpowerID Identity Warehouse. When a user logs in to a Password Vault application from EmpowerID, EmpowerID submits the user's username and password to the application through HTTP Post. If users change the passwords associated with the application, they must change their Password Vault application passwords in EmpowerID to avoid login failures. |

- Password Vault Application Template — EmpowerID provides a number of Password Vault application templates out of the box that can be quickly configured for your specific implementations of each application. These templates include the following:
- Final Builder
- GoToMeeting
- Jira
- Jive Community Site
- Salesforce
- Certificate — This specifies the certificate used to sign the SAML assertion passed to EmpowerID.
- Application-Specific Config — This is XML-formatted text used to specify the unique logon page URL for the organization's application instance.
|
Used for integrating applications that accept SAML transactions for identity federation. In SAML transactions, identity providers make an assertion about an authenticated user's identity, encrypt and sign the assertion, and pass that data to a service provider, where access decisions are made. When registering SAML applications in EmpowerID, you can select an existing SAML connection for the application (if one exists in your environment) or you can create a new SAML connection for the application. If you opt to create a new SAML connection, the form presents you with additional configuration settings for the application. These settings include three sections: SAML Connection Information, Single Logout Configuration, and Certificates. 
- SAML Application Template — EmpowerID provides a number of SAML Connections pre-configured for specific SAML applications, as well as a default connection that can be used as a starting point for creating connections for any other SAML-based applications. The SAML templates provided out of the box by EmpowerID include the following:
- ADP — Allows you to quickly integrate your enterprise ADP application with EmpowerID.
- Box — Allows you to quickly integrate your enterprise Box application with EmpowerID.
- Concur — Allows you to quickly integrate your enterprise Concur application with EmpowerID.
- Default — Provides basic configuration settings that can be used for building new SAML connections not provided out of the box by EmpowerID. This template is applied to each SAML application, even when selecting an application— specific connection, such as Google or ADP.
- DropBox — Allows you to quickly integrate your enterprise DropBox application with EmpowerID.
- Google — Allows you to quickly integrate your enterprise Google application with EmpowerID.
- ReverseProxy — Allows you to quickly integrate a Reverse Proxy application with EmpowerID.
- Salesforce — Allows you to quickly integrate your enterprise Salesforce application with EmpowerID.
- SuccessFactors — Allows you to quickly integrate your enterprise SuccessFactors application with EmpowerID.
- UltiPro — Allows you to quickly integrate your enterprise UltiPro application with EmpowerID.
- Yammer — Allows you to quickly integrate your enterprise Yammer application with EmpowerID.
- Display Name — This is the name of the SAML connection that appears to users on EmpowerID User Interfaces.This field is required.
- Description — This is a description for the SAML connection.
SAML Submission Method — This specifies the method used by EmpowerID to submit SAML assertions to the application in accordance with the requirements of that application. Supported methods include the following: - HTTPArtifact
- HTTPPaos
- HTTPPost
- HTTPRedirect
- HTTPSoap
- Reserved4
SAML Name Identifier Format — This specifies the format of the SAML Name Identifier. The Name Identifier format depends on what the service provider expects and includes all possible SAML 1.1 and 2.0 options. - Assertion Consumer URL — This specifies the URL to which the SAML assertion needs to be submitted for the application to process it.
- Issuer — This value tells the SAML application where to direct the user's browser for an assertion of the user's identity.
- Tile Image URL — Specifies the URL with the image to use for the tile.
- Initiating URL — Specifies the URL to use in initiating
- Send Response as JWT? — Specifies whether to send the response as a JSON web token.
- Send RelayState to Provider? — Specifies whether the Relay State should be submitted to the application.
- RelayState — Specifies the Relay State to be sent if Send RelayState to Provider? is selected.

- Logout URL — This specifies the URL to direct the user's browser to on logout.
- Logout SAML Protocol — This specifies the protocol used by EmpowerID to log out of the application in accordance with the requirements of that application. Supported protocols include the following:
- HTTPArtifact
- HTTPPaos
- HTTPPost
- HTTPRedirect
- HTTPSoap
- Reserved4

|
Used for integrating applications that employ the Security Token Service (STS) model for facilitating identity transactions, such as Office 365 and SharePoint. When registering WS-Federation applications in EmpowerID, you can select an existing WS-Federation connection for the application (if one exists in your environment) or you can create a new WS-Federation connection for the application. If you opt to create a new connection, the form presents you with additional configuration settings for the application. These settings include four sections: WS-Federation Connection Information, Tile Information, Single Logout Configuration, and Relying Party Trust.



- Logout URL — This specifies the URL to direct the user's browser to on logout.

|
Used for integrating Web-based applications with EmpowerID in situations where you cannot alter the Web application with assemblies supplied by EmpowerID to process usernames inserted into HTTP headers. In situations like these, you can use password vaulting to pass the usernames and passwords directly to the Web application. Please note that using this option requires writing the process in Node.js and inserting the file in the EmpowerID Proxy Server folder on your EmpowerID server. It is recommended that you use EmpowerID Professional Services staff for this. |
When registering Web Access Management (Password Vault) applications in EmpowerID you are presented with the following configuration settings: 
Display Name — This is the name of the Web Access Management (WAM) connection that appears to users on EmpowerID User Interfaces.This field is required. Base URL for Reverse Proxy — This specifies the URL the user types in their browser to go to the application. Description — This is a description for the Web Access Management connection. Allow Anonymous Access to Unprotected Paths — This specifies whether anonymous users can access paths on the WAM application not specifically protected by EmpowerID. Use Target Hostname in Requests (Reverse Proxy Only) — This specifies the home realm of the IdP used for authentication. Certificate — This specifies the certificate used to sign SAML assertions.This field is required. Routes — This specifies the specific paths (URLs) on the application to be protected by EmpowerID.
To add a route - On the Routes grid, click the Add button.

This opens the Routes dialog where you specify information for each route to protect. A description of the fields follows the image.

Name — Specifies the name of the Route. Display Name — Specifies the name for the Route that you want to appear to users in the EmpowerID user interfaces. Description — Specifies a description for the Route. Source URL — Specifies the actual location on the Web application to which the Proxy Server is to fetch resources on behalf of clients. This value is a translation of the Target URL. Target URL — Specifies the URL to which you want users or clients to navigate via their browsers to access given resources on the Web application. Max Connections — For future implementation. Is Base URL — Specifies whether the route is the base URL of the Web application. At least one route must be a Base URL route and you can more than one route translate to the same Source URL. This is helpful for situations where load-balancing is needed. When this is the case, and more than one route is configured for a User Entered URL, the Reverse Proxy Server will service the requests in a round-robin fashion. Is Offline — Specifies whether the route is offline. If a route is offline, the Reverse Proxy Server will not service it. Use Sticky Sessions — For future implementation. The following image shows what the Base URL WAM Route for an application in our environment looks like. In the image, we have configured the route to translate the Source URL," http://www.andysbeans.com/andysbeans," typed by clients in their browsers to "http://sso.empowerid.com:8080/andysbeans", which is the real location of the application's base URL.

- After filling in the fields, click Save.
- The Added flag updates from 0 to 1. Click the flag to review the WAM route you are adding to the application.

- To remove a WAM Route, click the Undo button to the right of the route.

|
|
Used for securing access to Web applications when those applications have been configured with assemblies from EmpowerID allowing for user identities to be passed to the application via HTTP Headers.
When registering Web Access Management (Password Vault) applications in EmpowerID you are presented with the following configuration settings: 
Display Name — This is the name of the Web Access Management (WAM) connection that appears to users on EmpowerID User Interfaces.This field is required. Base URL for Reverse Proxy — This specifies the URL the user types in their browser to go to the application. Description — This is a description for the Web Access Management connection. Allow Anonymous Access to Unprotected Paths — This specifies whether anonymous users can access paths on the WAM application not specifically protected by EmpowerID. Use Target Hostname in Requests (Reverse Proxy Only) — This specifies the home realm of the IdP used for authentication. Certificate — This specifies the certificate used to sign SAML assertions.This field is required. Password Vault Login Page URL— This specifies the path to the login page of the Web application being protected by EmpowerID.This field is required. Password Vault Application Type— This specifies the JavaScript file used to duplicate the login requirements of the application.This field is required. Routes — This specifies the specific paths (URLs) on the application to be protected by EmpowerID.
To add a route - On the Routes grid, click the Add button.

This opens the Routes dialog where you specify information for each route to protect. A description of the fields follows the image.

Name — Specifies the name of the Route. Display Name — Specifies the name for the Route that you want to appear to users in the EmpowerID user interfaces. Description — Specifies a description for the Route. Source URL — Specifies the actual location on the Web application to which the Proxy Server is to fetch resources on behalf of clients. This value is a translation of the Target URL. Target URL — Specifies the URL to which you want users or clients to navigate via their browsers to access given resources on the Web application. Max Connections — For future implementation. Is Base URL — Specifies whether the route is the base URL of the Web application. At least one route must be a Base URL route and you can more than one route translate to the same Source URL. This is helpful for situations where load-balancing is needed. When this is the case, and more than one route is configured for a User Entered URL, the Reverse Proxy Server will service the requests in a round-robin fashion. Is Offline — Specifies whether the route is offline. If a route is offline, the Reverse Proxy Server will not service it. Use Sticky Sessions — For future implementation. The following image shows what the Base URL WAM Route for an application in our environment looks like. In the image, we have configured the route to translate the Source URL," http://www.andysbeans.com/andysbeans," typed by clients in their browsers to "http://sso.empowerid.com:8080/andysbeans", which is the real location of the application's base URL.

- After filling in the fields, click Save.
- The Added flag updates from 0 to 1. Click the flag to review the WAM route you are adding to the application.

- To remove a WAM Route, click the Undo button to the right of the route.

|
|
Users Tab
This section of the form provides settings for linking the application with an account directory.
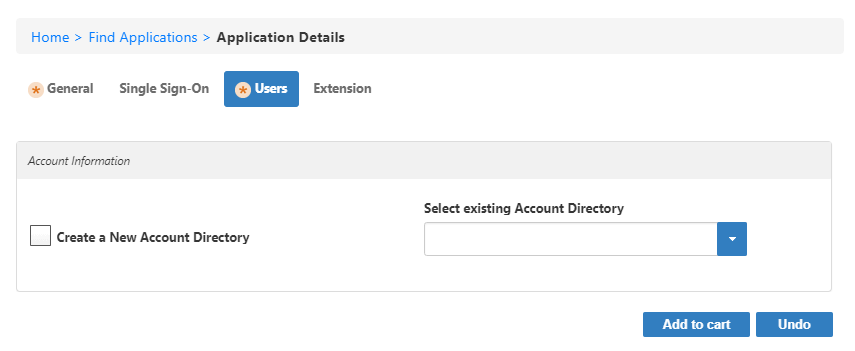
When registering applications in EmpowerID, you must link those applications to an account directory. This is necessary for EmpowerID to control access to the application as well as for providing you the means for attesting the accounts owned by users in registered applications during audits. When linking applications to account directories, you can choose to create a new account directory specifically for the application or select an existing account directory that has already been registered in EmpowerID. If you choose to create a new account directory, EmpowerID creates a special type of account store internal to EmpowerID, known as a "tracking-only" account store. A tracking-only account store account exists as a container within EmpowerID for storing user and group records for SSO or Attestation without making a connection to any external directory associated with the application. Opting to create a new account store when registering applications in EmpowerID is advantageous in that doing so creates a one-to-one correlation between the account store and the application, as well as the SSO connection for the application, if used. You simply add your existing users and groups to the account store in the same way you would with Active Directory users and groups.
Extension Tab
This section allows you to add up to fifteen custom attributes for your application.
Once you finish setting up the application, select it from the applications grid to see the Application Details Page where you can further configure it with groups, application subcomponents, MFA, etc.