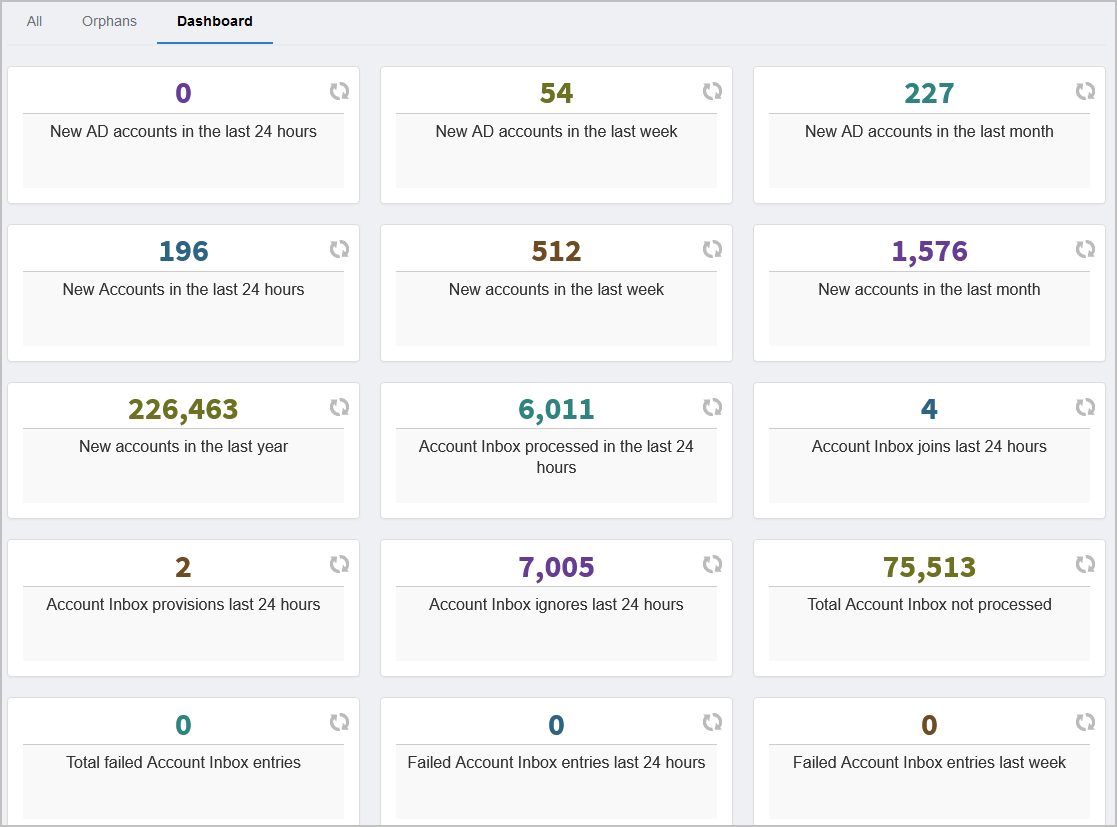
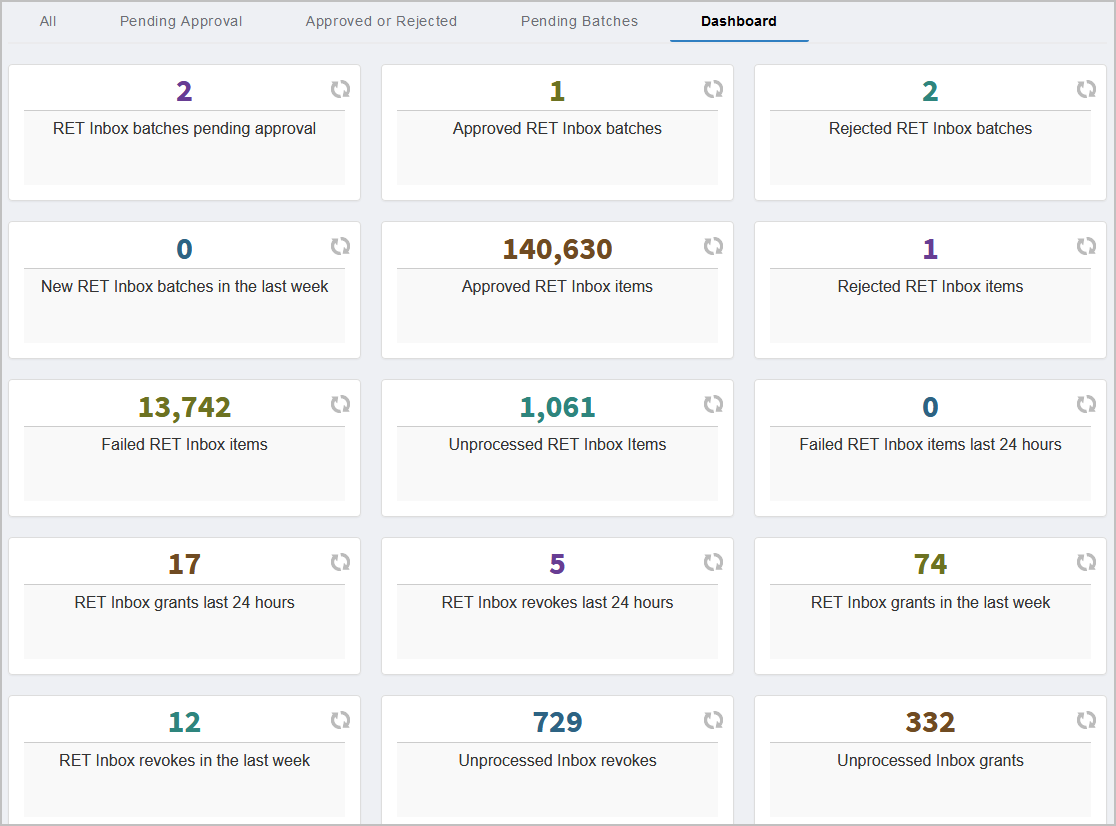
Access Assignments to Person Direct — This report displays all access assignments made directly to a person.
Account Service Identities — This report displays all accounts used as service or app pool identities.
Accounts - Computer Local Admins — This report displays all users that are local computer administrators.
Accounts - High Security — This report displays all accounts that are members of any high security group.
Accounts - Local Computer Accounts — This report displays all local computer accounts.
Accounts - Privileged Accounts — This report displays all accounts flagged as a privileged account usage type.
Accounts - Shared Credentials — This report displays all accounts used as shared credentials.
Accounts Created in the Last 30 Days — This report displays all accounts created in EmpowerID within the last 30 days.
Accounts No Login 90 Days — This report displays all AD accounts that have not logged in during the last 90 days.
Accounts Password Never Expires — This report displays all AD accounts where the password is set to never expire.
Accounts Password Older 120 Days — This report displays all account with password older than 120 days.
Accounts with Deleted Owners — This report displays all accounts owned by people who have been deleted from EmpowerID.
Accounts with Manager Expiring in 60 Days — This report displays all accounts where the manager of that user is expiring in 60 days.
Accounts without a Responsible Party — This report displays all accounts without a responsible party; to meet this qualification, the account in question must have no PersonID or OwnerAssigneeID.
Accounts without Managers — This report displays accounts without managers assigned in AD.
AD Accounts Expiring 60 Days — This report displays account in AD expiring within the next 60 days.
AD Accounts that Never Logged In — This report displays AD accounts that have never logged in.
All Access Assignments in the System — This report displays all access assignments in the system.
All High Security Groups — This report displays all groups flagged as high security groups in EmpowerID.
Audit Log Report — This report displays the audit log.
Computers without a Responsible Party — This report displays all computer that do not have a valid owner or a responsible person.
Core Identities Created Last 30 Days — This report displays all core identities created in the last 30 days.
Core Identity Without a Person — This report displays all cored identities without a person assigned to them.
Empty Groups — This report displays all groups that do not contain any members.
Enforcement Groups — This report displays all EID groups used by EmpowerID for permissions enforcement.
Expired Accounts — This report displays all accounts that have expired in AD.
Expired Groups — This report displays all groups where the ValidUntil date has passed.
Group Membership High Security — This report displays all groups memberships for high security groups.
Group Membership Not People — This report displays all group memberships for accounts that aren’t people.
Group Membership Not RBAC Assigned — This report displays all groups memberships where account is a member of a group not by RBAC policy.
Groups - Possible Stale Disabled Members — This report displays all groups that may be stale because all members of the group are disabled or expired.
Groups and their Native AD Managed By — This report displays all groups and their native AD managers.
Groups Expiring 30 Days — This report displays all groups expiring in the next 30 days.
Groups O365 Type — This report displays all Office 365 groups.
Groups without a Responsible Party — This report displays all sensitive groups that do not have a valid owner or responsible party.
High Security People — This report displays all high security people - where they have at least one high security group membership.
Locked Out Accounts — This report displays all AD accounts that were locked out as of the last inventory.
Mailboxes Owned by Deleted People — This report displays all mailboxes owned by people that have been terminated.
Management Roles without a Responsible Party — This report displays all Management Roles that do not have a valid owner or responsible Person.
Orphan Accounts — This report displays all accounts that do not belong to a person.
Password Manager Enrollments — This report displays all people who have enrolled for password management.
People Created in Last 30 Days — This report displays all people created in the last 30 days.
People Logged In Last 1 Day — This report displays all people who have logged in to the system during the previous day.
People Not Enrolled — This report displays all people who have not enrolled for password self-service reset.
People Not Logged In 30 Days — This report displays all people who have not logged in to the system within the last 30 days.
People That Have Ever Logged In — This report displays all people that ever logged in to the system.
People with Invalid Managers — This report displays all people with disabled or terminated managers.
People without Accounts — This report displays all people that do not own any user accounts.
Person Duplicate Email — This report displays all people with duplicate email addresses.
Person Duplicate Phone Number — This report displays people with the same phone number.
Person Logged In 30 Days — This report displays all people that have logged in to the system at least once during the last 30 days.
Person Verified Addresses — This report displays all verified person communication channels to include verified emails, SMS and voice call numbers.
Possible Stale Groups — This report displays all groups that have not had a change in membership within the last 180 days.
Recertification Fulfillment Report — This report displays all fulfillment actions.
Recertification Revokes All — This report displays recertification revokes.
Recertification revokes Completed — This report displays all recertification revokes that are flagged as completed.
Recertification Revokes Failed — This report displays all recertification revokes that are flagged as failed.
Recertification Revokes Ignored — This report displays all recertification revokes that are flagged as ignored.
Recertification Revokes In Progress — This report displays all recertification revokes that are still in progress.
SAP Role and Profile Membership Changes — This report displays any change history for SAP Roles and Profiles.
Status by Location — This report displays all recertification stats by location.
Too 100 High Security Groups — This report displays the top 100 high security groups with the most members.
Top 100 Riskiest Groups — This report displays the top 100 groups with the highest risk scores. Risk scores are calculated by what members of the group can do in the system.
Top 100 Riskiest People — This report displays the top 100 people with the highest risk scores. Risk scores are calculated by what people can do in the system.
Your Access Assignments — This report displays all of the access assignments granted to the currently logged in user.
Your Expiring Access Assignments — This report displays all of the access assignments granted to the currently logged in user that are due to expire.
Your Reports Access — This report displays all of the access assignments of the directs reports assigned to the currently logged in user.
Your Reports Expiring Assignments — This report displays all of the access assignments granted to the direct reports of the currently logged in user that are due to expire.