EmpowerID 2020 R2 adds several major new product features and usability enhancements.
The reality for organizations today is that enterprise risks are scattered across many Cloud and on-premise systems and are often acquired by a risky combination of cross-system access. Given the growing number of enterprise level applications being made available to organizations, it is imperative organizations know the permissions models for each application they use. Otherwise, users may have more access than needed, resulting in unnecessary risks. To gain visibility and control over these risks, EmpowerID provides one of the largest IGA connector libraries available with the ability to connect and consume even the most idiosyncratic permissions models and inheritance used within your applications. In this way, the permissions in each system can be brought together into one comprehensive and business-friendly permissions model.
The goal of compliant risk management is to ensure that organizations deliver compliant access and that changes occurring in native system admin consoles do not create non-compliant access. To achieve this goal, current access assignments must be continually measured against a definition of non-compliant access. Therefore, to define compliant access, you must first define non-compliant access. Risks are a part of the business domain and must be defined and owned by business users as they relate to the organization’s specific industry and business processes. Defining an organization’s risk policies based on toxic combinations of technical entitlements such as application groups or roles is not a viable option. These technical objects have little meaning to business users and the activities they enable and the risks they pose are easily obscured and can change as underlying access shifts.
The new EmpowerID Compliant Access Solution simplifies risk management by giving organizations the ability to abstract technical access rights terminology from inventoried systems away from business users in favor of language more readily accessible to business users, their managers and those responsible for building effective risk management policy. Most IAM systems manage only the technical aspects of access control and, as such, fail to provide a comprehensive model that maps the entitlements in technical systems to clearly understood business processes. For example, consider the act of creating a purchase order in SAP. In that system, entitlements are designated by TCodes, and the TCode for creating a purchase order is ME21N. While application experts might instinctively know what the TCode means, most likely many business users will not. And that is one entitlement in one system. When one considers the many technical systems that could be used within the daily operations of a business — and the amount of entitlements available to users within each — it becomes easy to see how those responsible for managing access can spend an undue amount of time deciphering exactly “who can do what, where and when with their IT systems.”
Figure 1: Example of a native system entitlement
That is where EmpowerID’s Compliant Access Solution comes into the picture. EmpowerID understands that each organization has its own particular language for processes and policies and designed the solution with the flexibility to bring that process language into risk management as is. This model understands that to be truly effective, delivering compliant access requires more than just repeating “black box” speak. A system that simply repeats technical system language back to users does little to help businesses translate the technical rights in each IT system to the daily business activities necessary for accomplishing business goals.
The EmpowerID Compliant Access Solution starts with the premise that all businesses can be broken down into a series of business processes performed during the ongoing production and delivery of their goods or services. Each business process is itself, a series of tasks that can be performed by internal or external participants to complete that process. And each individual task in each process can be broken down into the functions that are executed in the process of completing that task. Simply put, EmpowerID defines functions as “business defined activities that a person can perform.” Using this approach, the technical term “ME21N” mentioned above could be translated simply as “Create Purchase Order.” The activities are the same, but the terminology for the latter is immediately clearer for business users.
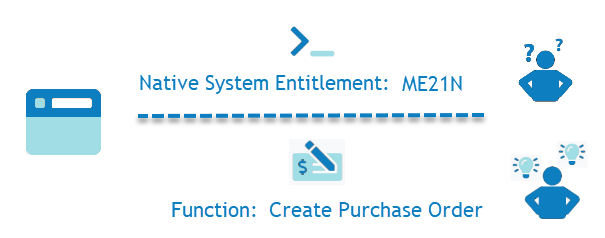
Figure 2: Native System Entitlements VS Functions
Using functions as the building blocks of what users can do in technical systems, organizations then build their risk policies around those functions using their own business language for those functions and policies. Once functions are named, business process specialists and technical application specialists map those functions to their representative entitlements in their respective applications. Once the mapping is complete, the risk management engine can be enabled to run on a scheduled basis to return users with functions. Using “Create Purchase Order” as an example, the end result is that those responsible for risk management can quickly see who in their organization can create a purchase order and where they can do it.
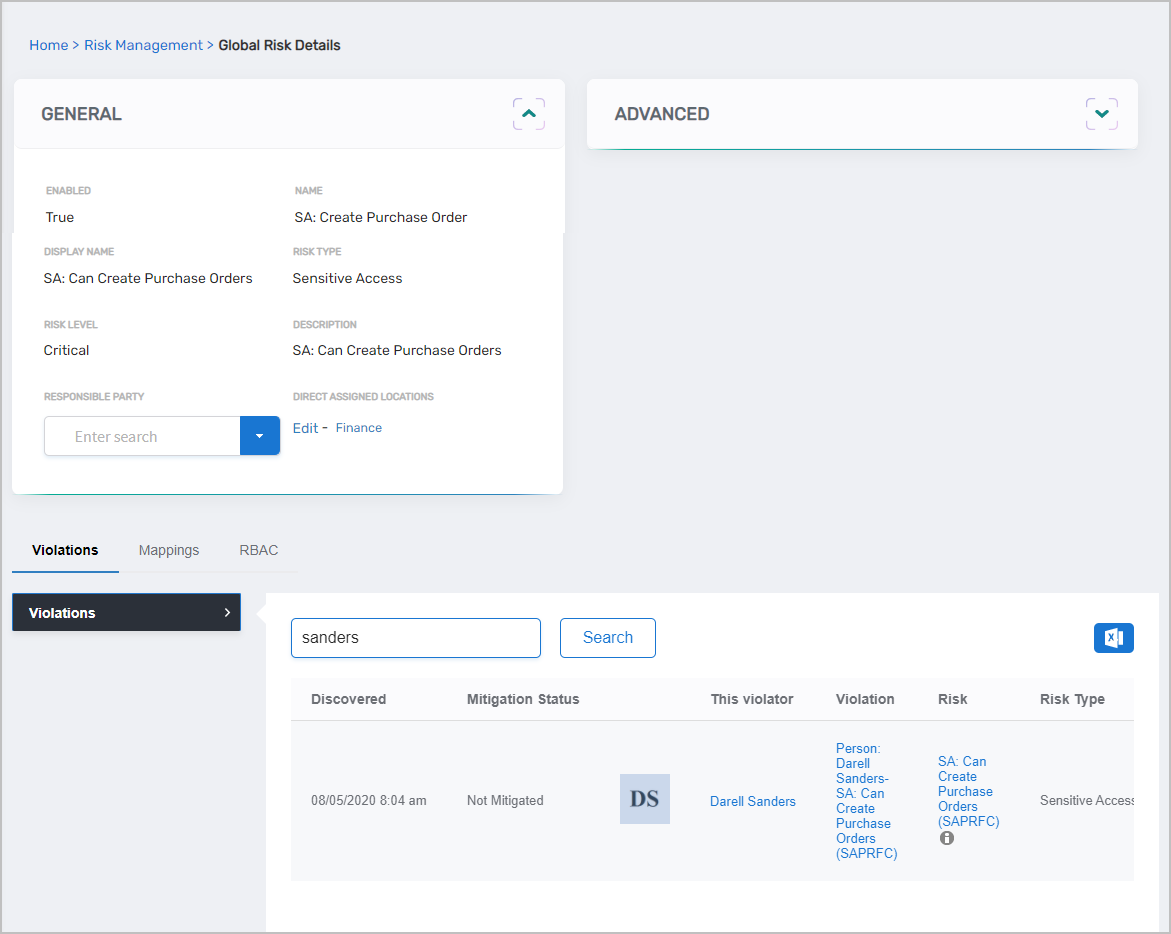
Figure 3: Risk Management User Interface
In today’s “work from anywhere” model, cloud-based identity management solutions are becoming the norm. Nowhere is this more evident than with Microsoft’s shift away from on-premise Active Directory federating with Office 365 to Azure Active Directory (AD) as the primary identity. De-emphasizing and even eliminating ADFS and federation are the future. Microsoft makes this even more apparent with its integration of the System for Cross Domain Identity Management (SCIM) protocol into Azure. SCIM was created as a powerful means of standardizing, simplifying, and automating identity management of users, groups, and devices across cloud-based applications and services and Microsoft is betting big on it. The problem with SCIM is that it has yet to become widely adopted and many applications simply do not support it. So, if you have custom applications with repositories of identity information or use an on-premise or cloud application like SAP S/4 HANA or SAP Ariba or even a major HR system like UltiPro, you are not going to be able to integrate those systems with Azure unless you or the vendor builds a SCIM interface for each. This is no small task because while the protocol is simple, building the interface is not. EmpowerID has stepped into the gap and built a Workflow-Driven SCIM Virtual Directory Server (VDS) that can sit between Azure and your non-SCIM applications. You simply connect those applications to EmpowerID and register the EmpowerID SCIM VDS in Azure. There is no need to wait for vendors or put in the time and effort needed to build a SCIM interface. EmpowerID takes care of everything for you.
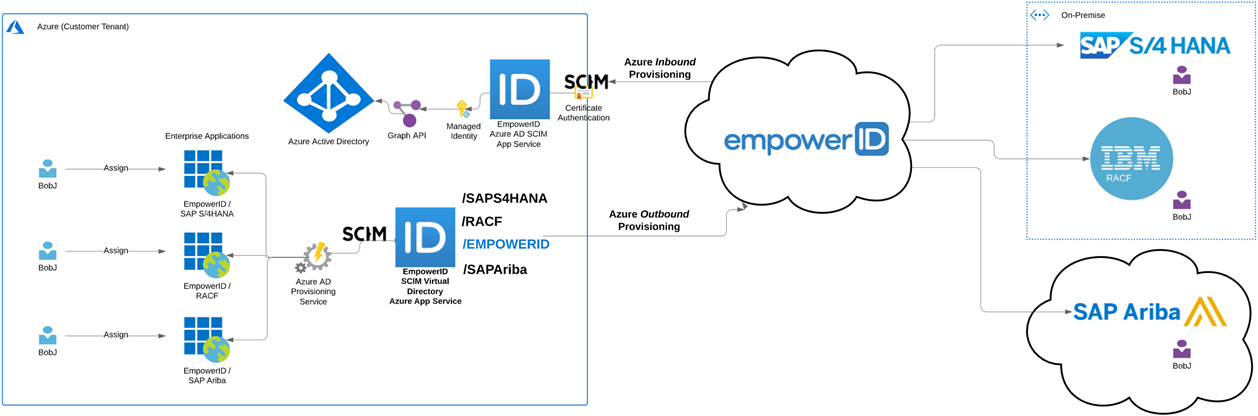
Figure 4: Solution Architecture
All the Advantages of SCIM without the effort — Created in 2011 as an open standard, lightweight provisioning protocol for the “Cloud age,” SCIM provides a uniform way for applications to communicate identity information to each other. Adoption of SCIM has been slow, but it is the way forward. With EmpowerID’s SCIM VDS, organizations can convert their applications to SCIM without waiting for vendors to come onboard or doing the heavy lifting of converting their legacy proprietary applications to SCIM.
Seamlessly Integrate All Your Applications with Azure Provisioning Services — The EmpowerID SCIM Virtual Directory is a microservice and a SCIM server that can be deployed as an App Service in any Azure tenant. Simply plug the VDS into any Azure environment, secure it with an Azure managed identity and then register as many of your enterprise applications as needed. If the VDS knows about these applications, it will pass Azure provisioning commands to that system, SCIM compliant or not.
Workflow-Driven Virtual Directory Services — More than just a “SCIM gateway,” that is, more than just an application that simply passes identity lifecycle commands like – “provision this user” or “add this user to that group” – from one system to another, the EmpowerID VDS treats everything as a workflow. This keeps your business logic in the process. Commands are evaluated by the VDS, which can trigger policies, invoke naming conventions, generate strong passwords and send policy violations for human approval before any final provisioning action occurs. You determine what needs to happen when Azure makes a provisioning call.
Fills in Azure AD Provisioning Gaps — Azure is here to stay and so is the shift away from on-premise user directories like Active Directory. Microsoft’s aim is to make Azure AD the central point for authentication, conditional access and MFA. They want you to use Azure AD for all your identity-aware applications. The idea is that you do identity in Azure and Azure then propagates that to your other systems. So, for example, if you provision new users in Azure AD, those users should be provisioned in a connected HR system and vice-versa. Well that sounds about right; however, there is a huge problem: The process is blind to your business logic. When you add EmpowerID to Azure, you fill in these gaps by bringing all the features of EmpowerID to your Azure subscription, including:
Cross-System Password Reset
Access Certification
Compliant Access
Role Mining Analytics
Delegated Identity Administration
End User Email Notifications
The EmpowerID SCIM microservice is designed to help you manage your Azure tenants and subscriptions to include licenses and roles. Beyond the licensing challenges associated with Azure subscriptions is the fluid nature of the Azure infrastructure and how quickly new services can be introduced and then decommissioned. This fluidity can make it difficult for security and audit teams to meet their regulatory obligations concerning asset management. The SCIM microservice helps you address both these issues by giving you full visibility and control over both Azure Roles and Azure licenses via Azure License Manager and Azure RBAC Manager. For more information setting up the EmpowerID SCIM microservice in Azure, see /wiki/spaces/CloudAdmin/pages/907509785.
The IT Shop brings a familiar shopping cart experience to the license access request process. Users simply search for the resources they need and add items to their cart. Managers may shop on behalf of their direct reports as part of the onboarding process. When the user is done shopping, they simply submit their request. The workflow engine determines from your organizational rules, what approvals are needed, if any policies would be violated, and who must approve each request or violation. All participants are kept informed by email notifications and all requests, decisions and associated fulfillment actions are recorded and integrated into the audit process.
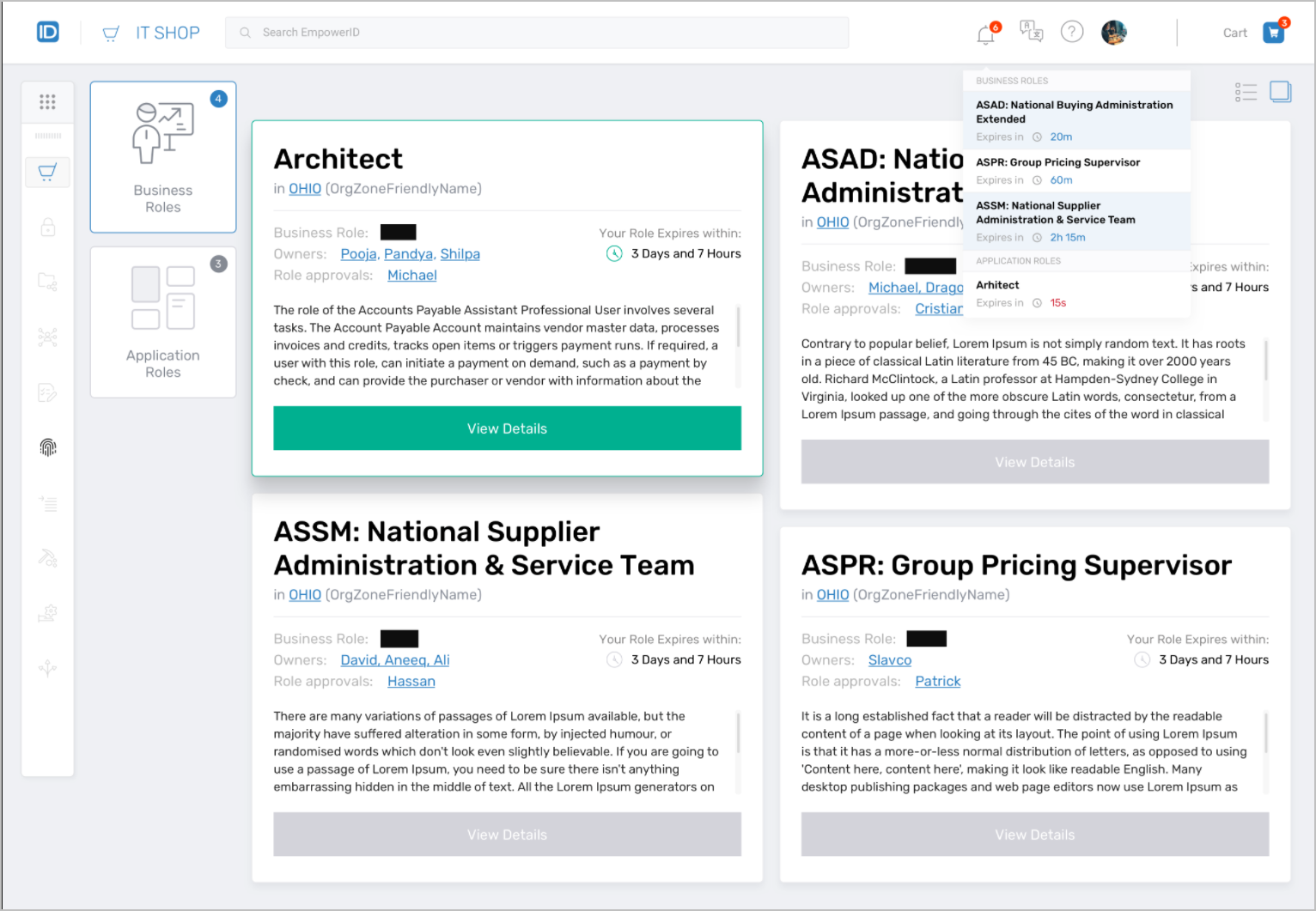
Figure 5: User Interface for the IT Shop Microservice
The Azure Analytic Microservice provides organizations with intelligent, real-time visual feedback on the drivers of their Azure expenses and the number of licenses being consumed by their organization at any given data point.
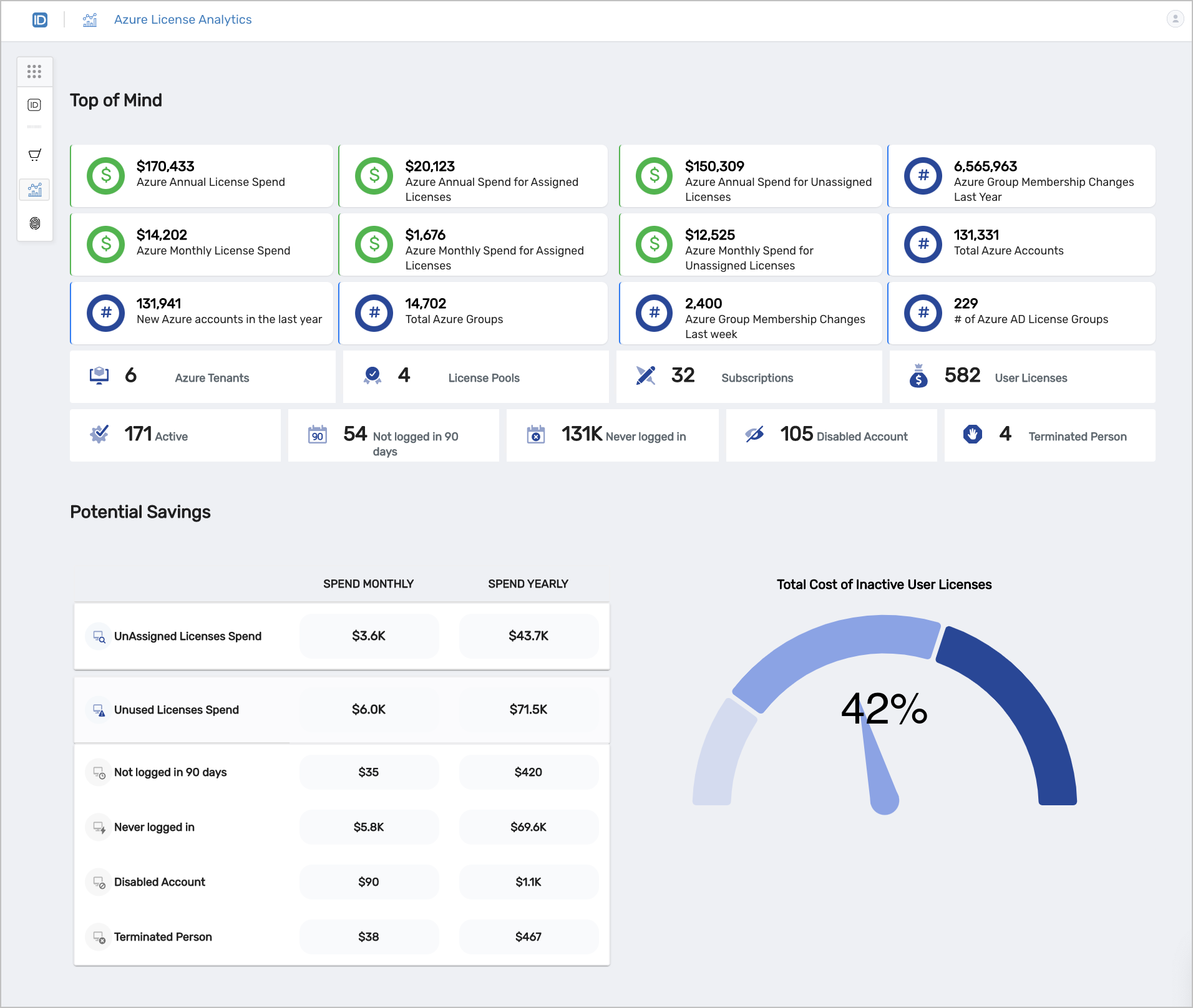
Figure 6: Azure License Analytics Dashboard
Azure License Manager is an licensable module in the EmpowerID Suite that is designed to help organizations inventory their Azure licenses and expenses across multiple Azure tenants for cost reporting and allocation of license expenses within their organization. According to research, of the 200 million Office 365 users Microsoft is reporting, 56% of licenses are inactive, underutilized, over-sized or unassigned. Azure License Manager can help you save up to 50% of your license costs by discovering licenses that fall into that category and automating Azure license management using flexible policies. How does Azure License Manager help with this?
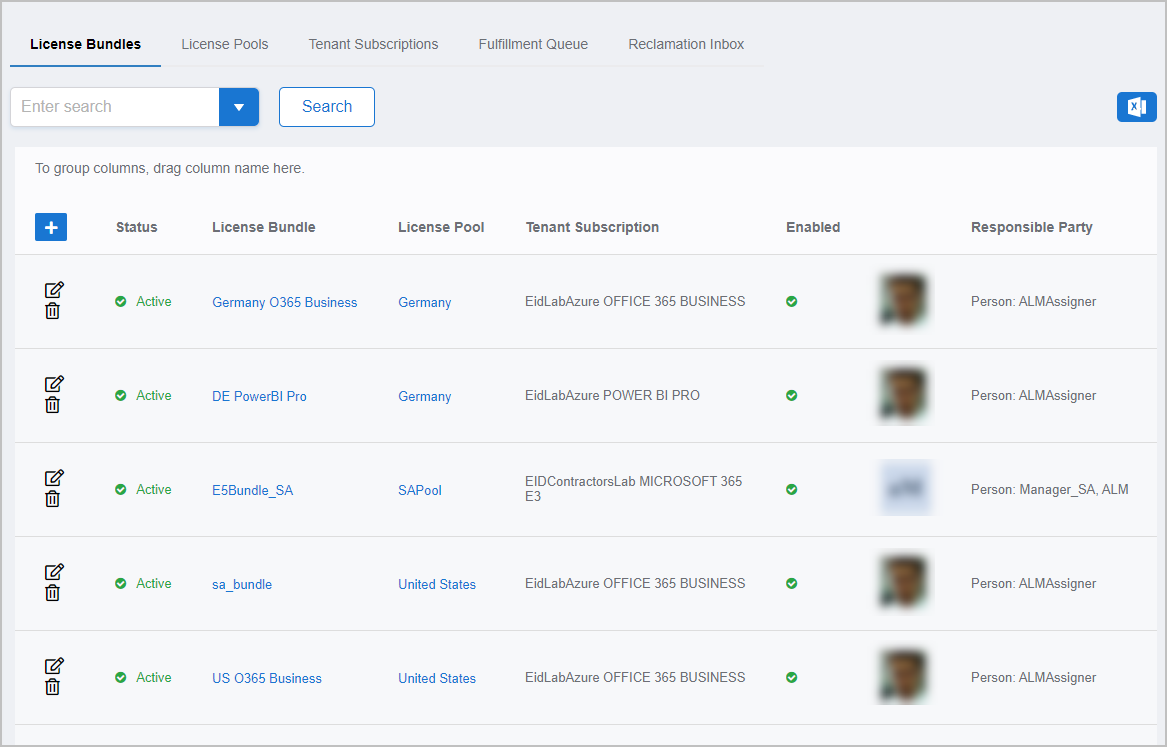
Figure 7: Azure License Manager User Interface
Gives you an accurate inventory of all your Azure Licenses — Azure License Manager can connect to all your Azure and Office 365 tenants to retrieve a detailed license inventory. You’ll immediate know all your organization’s subscriptions, license counts both allocated, activated, and disabled. You’ll also have an accurate picture of which service plans assigned within the subscriptions are enabled for different user populations. License Manager allows you to enter the negotiated costs for each of your SKUs to enable accurate reporting on actual cost allocations and to identify real savings from unused or nonoptimal license assignments.
Helps you allocate responsibility and track costs with License Pools — Azure License Manager can connect to all your Azure and Office 365 tenants to retrieve a detailed license inventory. You’ll immediate know all your organization’s subscriptions, license counts both allocated, activated, and disabled. You’ll also have an accurate picture of which service plans assigned within the subscriptions are enabled for different user populations. License Manager allows you to enter the negotiated costs for each of your SKUs to enable accurate reporting on actual cost allocations and to identify real savings from unused or nonoptimal license assignments.
Helps you allocate responsibility and track costs with License Pools — A key challenge in managing Office 365 licenses is the inability to partition a subscription into smaller units to allocate to different business units and geographies within the organization for delegated assignment and cost allocation and tracking. Azure License Manager introduces the concept of License Pools. License Pools are created to subdivide portions of the licenses within a subscription to allocate responsibility and for chargeback reporting. By segmenting your licenses into pools, you’ll be able to track usage and assign costs to each team.
Gives you the tools needed for license optimization — Azure License Manager can provide rapid ROI by identifying all your inactive, oversized and duplicated Office 365 licenses and allowing them to be reallocated easily. You’ll be able to see which inactive users are assigned licenses that could be reclaimed and used elsewhere. Azure License Manager also includes the ability to track service plan usage for products like Exchange, Teams, and Yammer. This data can spot users that are “over-licensed,” meaning the services they actually use could be delivered via a less expensive license bundle. Analysis of overspending can quickly save money or identify areas of the business with poor adoption of new technology.
Lets you create policies to automate license assignment — Azure License Manager supports the creation of flexible and dynamic policies to automate the lifecycle of license assignment. License bundles from pools can be assigned to users automatically based on almost any criteria such as company, department, location, group membership. As user’s join the organization and transition between departments and roles, Azure License Manager reevaluates assignment policies to always ensure each user has the correct licenses while eliminating costly manual license management tasks. All policy-based assignments provide a wealth of reporting so admins and auditors can see exactly why each user has the licenses they are assigned.
Lets users to directly request licenses — Azure License Manager brings a familiar shopping cart experience to the license access request process. Users simply search for the licenses they need and add items to their cart. Managers may shop on behalf of their direct reports as part of the onboarding process. When the user is done shopping, they simply submit their request. The workflow engine determines from your organizational rules, what approvals are needed, if any policies would be violated, and who must approve each request or violation. All participants are kept informed by email notifications and all requests, decisions and associated fulfillment actions are recorded and integrated into the audit process.
Secure Deployment Model — Azure License Manager leverages EmpowerID’s Azure AD SCIM Microservice Connector. This microservice is a fully compliant SCIM 2.0 Server to which EmpowerID communicates to inventory and manage your Azure tenant licenses and security. The microservice can be deployed to your tenant as a native Azure App Service. This deployment model enables secure fine-grained Graph API access managed by your security team. The microservice leverages an Azure Managed Identity which eliminates the need to share credentials.
Azure RBAC Manager provides auditing, Zero Trust delegated administration, policy-based access assignment, self-service shopping, and access recertification for Azure security. Azure RBAC Manager empowers organizations to maintain an accurate understanding of their Azure security landscape, to optimize its management, and to ensure compliance with an organization’s risk policies. How does Azure RBAC Manager help?
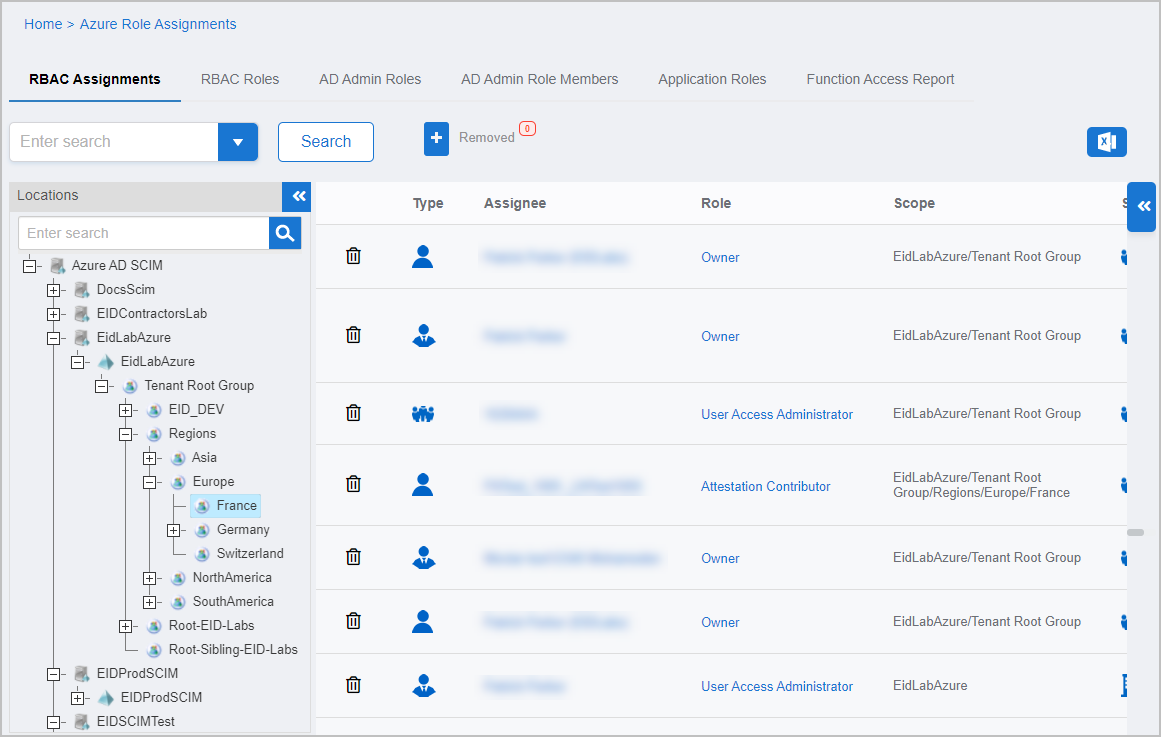
Figure 8: Azure RBAC Manager User Interface
Reduce risks through increased visibility — One of Azure’s key strengths is the ease with which new services and IT resources can be self-provisioned on the fly. Also, just as quickly these services can be decommissioned. The elastic nature of the Azure infrastructure and these rapid changes make it difficult for security and audit teams to meet their regulatory obligations concerning asset management. Azure RBAC Manager empowers organizations to maintain an accurate understanding of their Azure security landscape, to optimize its management, and to ensure compliance with an organization’s risk policies by continuously monitoring for changes. Azure RBAC Manager continuously inventories the RBAC structure of your Azure tenants including the tenant Root, Management Groups and subgroups, Subscriptions, and Resource Groups. This structure is key to understanding the scope of your Azure Role assignments and their impact. Azure includes 3 very different types of roles including Azure AD “Directory Roles”, Azure RBAC “Resource Roles”, and Azure “Application Roles”. Azure RBAC Manager handles all three types and even reports the individual fine-grained rights granted by each role. Azure Resource Roles can be assigned at any level or scope in the Azure hierarchy, even on individual resources. Azure RBAC Manager inventories even these individual resources like virtual machines, Kubernetes clusters, and SQL databases including any of their direct role assignments.
Access Intelligence — The greatest challenge in identifying and managing enterprise risk is understanding the actual business access that the technical entitlements granted to users enable. EmpowerID uncovers the real-world impact of Azure access assignments with a concept known as Business Functions. Business Functions are the business user recognizable terms for the activities performed by users with the access they are granted. EmpowerID ships with a large library of function definitions for Microsoft Azure. These functions add transparency to the fine-grained access assignments granted by out of the box and custom Azure Roles. Process owners and application owners may also use the Function mapping tools in EmpowerID to define additional Functions based on your Azure permissions.
Least Privilege Delegated Role Management — With Azure RBAC Manager you gain secure controlled delegation of access management for Azure roles and resources without being required to grant overly broad roles or to grant access to the Azure Portal or Office 365 Admin interfaces. Entitlement managers can see and manage access assignments in one place for all their Azure roles and resources across any number of tenants and environments. Entitlement managers can even delegate access management to non-technical owners to manage access using a non-technical interface. The EmpowerID risk engine ensures delegated admins grant only “Compliant Access” which is position appropriate and does not violate an organization’s risk policies.
Just in Time Temporary Privileged Access — A just in time and just enough administrative access infrastructure can dramatically increase an organization’s overall security by shrinking their attack surface and risk profile. Users require privileged access when performing administrative duties, but permanent access can invite misuse. A just in time privileged access system grants temporary access to decrease risk. With Azure RBAC Manager, business users and admins can request temporary elevation of their own privileges on demand. Azure Roles and entitlements can be shopped for using a shopping cart system to request access. The workflow engine determines from your organizational rules, what approvals are needed, if any policies would be violated, and who must approve each request or violation. All participants are kept informed by email notifications and all requests, decisions and associated fulfillment actions are recorded and integrated into the audit process.
Define and Manage Custom Granular Roles — Azure RBAC Manager supports managing and creating custom Azure Roles. Custom roles can be useful to define least privileged bundles of access whose scope is limited to specific resources or subscriptions. Azure RBAC Manager allows entitlement managers to request custom roles and be responsible for their assignment.
Role Ownership Management and Recertification — A security challenge that develops over time is understanding why roles and role assignments were initially created, by whom, and if they are still needed. Azure RBAC Manager provides automated processes to identify new roles and assignments, to assign ownership responsibility, to track their usage, and to allow periodic recertification. Recertification ensures that access which is no longer required is eliminated and least privilege principles are maintained.
Secure Deployment Model — Azure RBAC Manager leverages EmpowerID’s Azure AD SCIM Microservice Connector. This microservice is a fully compliant SCIM 2.0 Server to which EmpowerID communicates to inventory and manage your Azure tenant licenses and security. The microservice can be deployed to your tenant as a native Azure App Service. This deployment model enables secure fine-grained Graph API access managed by your security team. The microservice leverages an Azure Managed Identity which eliminates the need to share credentials.
EmpowerID can be configured to allow users to authenticate to EmpowerID and single sign-on (SSO) into other applications to which EmpowerID serves as an Identity Provider using their Azure credentials. Once a user authenticates and does SSO to other Service Provider applications such as Salesforce or ServiceNow, that user can seamlessly sign out of all applications simply by signing out of one. The flow for both of these scenarios looks as follows:
Login Scenario — The user goes to SP1 and lands on the EmpowerID Login page for authentication. The user selects Azure Native Auth. Subsequently, the user performs single sign-on into SP1, SP2 and SP3.
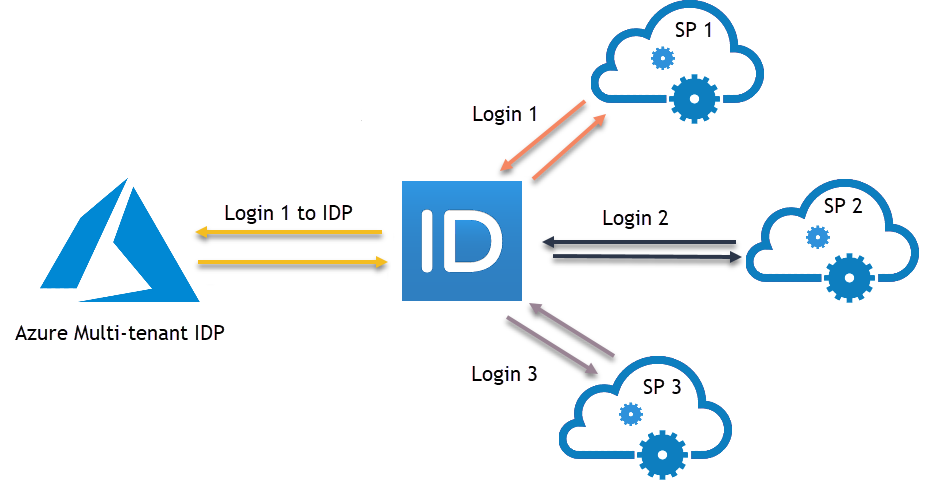
Figure 9: Azure Native Authentication Login Flow
Logout Scenario — The user logs out of SP1 and multiple logout requests/responses are exchanged between EmpowerID, Azure Mutli-tenant IDP and the service providers.
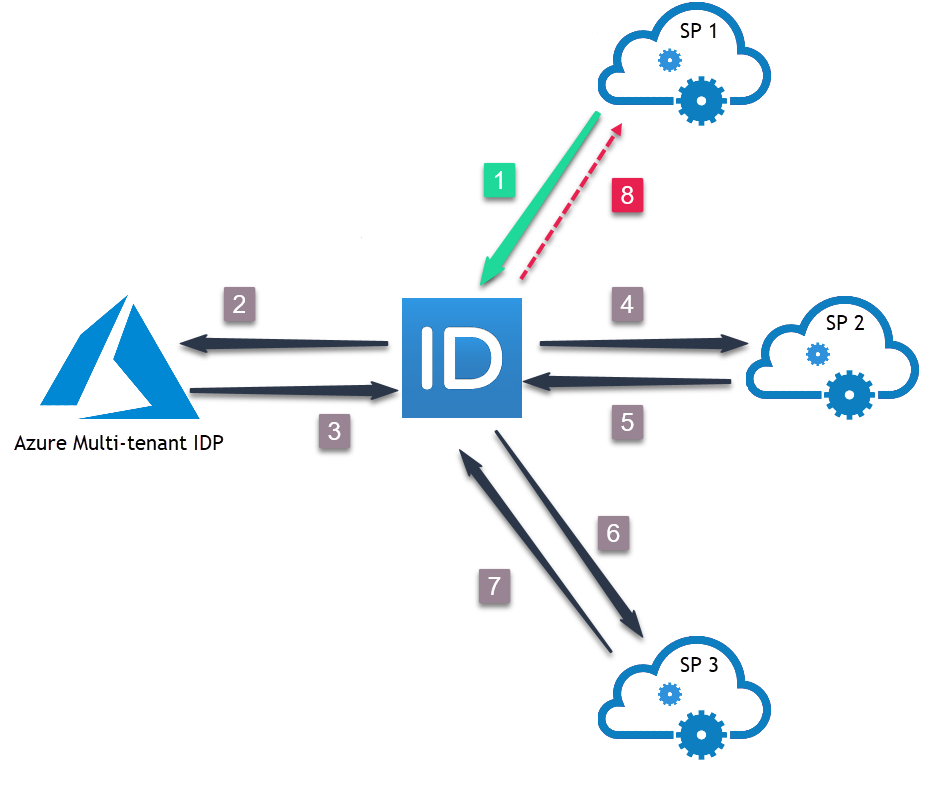
Figure 10: Azure Native Authentication Single Logout Flow
The single log out flow from the above image is as follows:
SP1 sends logout request to EmpowerID.
EmpowerID sends logout request to Azure.
Azure sends logout response to EmpowerID.
EmpowerID sends logout request to SP2.
SP2 sends logout response to EmpowerID.
EmpowerID sends logout request to SP2.
SP3 send logout response to EmpowerID.
EmpowerID sends logout response to SP1.
The View pages that users see when looking at the details for a given resource have been completely redesigned to present users with a more visually appealing and intuitive experience. Figure 14 below shows View page for a person that users see when viewing information about a person in EmpowerID.
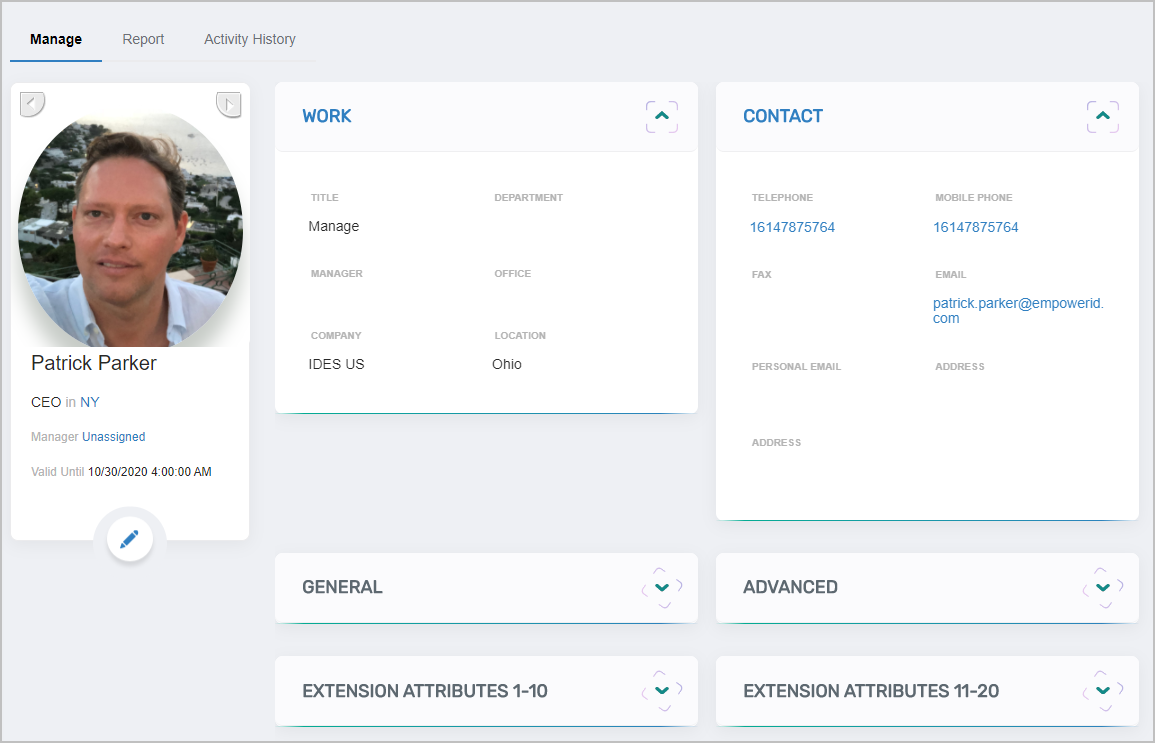
Figure 14: Person View Page
Feature | Description |
|---|---|
EmpowerID-3341 | Add standard More Info accordion to ORgRoleOrgZoneDetails page |
EmpowerID-3346 | Enable creation and deletion of ResourceSystemModule for applications |
EmpowerID-3357 | Add AccountExternalOrgRoleOrgZone grid to Lifecycle tab on Person Details and View Self pages |
EmpowerID-3352 | Make a mapped OrgRole grid |
EmpowerID-3356 | Add AccountInbox to Lifecycle tab on Person Details and View Self pages |
EmpowerID-3380 | Do not hide error when a workflow errors if Request.IsLocal = true |
EmpowerID-3142 | Refactor Audit View One page to allow for assigning to locations |
|