Active Directory
Before connecting EmpowerID to an external directory, please review the Getting Started with Directory Systems topic. The topic walks you through the prerequisites you need to complete before connecting to an external directory for the first time. These prerequisites include:
- Configuring the appropriate server roles for your EmpowerID servers
- Reviewing the Join and Provision Rules for your environment
- Reviewing the Join and Provision Filters for your environment
If you have already connected EmpowerID to another external directory, you can skip these prerequisites.
EmpowerID provides connectors for a wide range of user directories and resource systems. As an administrator, you can use these connectors to quickly connect EmpowerID to your organization's identity-aware systems and applications. When you do so, you create an account store for that application in the EmpowerID Identity Warehouse and use that account store to configure how you want EmpowerID to manage the identity information in that system. In this article, we demonstrate how to use the EmpowerID Active Directory connector to connect to Active Directory. After ensuring you have met the prerequisites specified in the Getting Started with Directory Systems topic, you connect EmpowerID to Active Directory by doing the following:
- Creating an account store in EmpowerID for Active Directory.
- Configuring EmpowerID settings for the account store connection, including whether to provision EmpowerID Persons during inventory or in batches using the Account Inbox permanent workflow.
- Mapping your external roles and locations to corresponding EmpowerID Business Roles and Locations.
- Reviewing and configuring the attribute flow rules for the account store.
- Turning on inventory.
- Enabling the Account Inbox Permanent Workflow when ready—if you are using batch processing to provision Person objects from the inventoried user accounts. This is the recommended method.
- Monitoring Inventory.
Before connecting EmpowerID to a directory system, you should determine whether you want EmpowerID to provision Person objects from the user accounts it discovers in the account store. If you do, then you should be able to answer the following questions before turning on inventory.
- When do you want EmpowerID to provision Person objects for those user accounts? At inventory or at a later point in time using the Account Inbox (recommended)?
- If inventory provisioning is desired, in what Business Role and Location should those Person objects be placed?
- How many user accounts can one Person have in the account store?
- If people can have more than one user account in the account store, do you want EmpowerID to attempt to automatically join any user accounts meeting the conditions of your Join rules to an existing Person during inventory?
- Do you want attribute flow to occur between EmpowerID and the account store? If so, what rules do you want to apply?
- If you have Resource Entitlement policies in place, do you want EmpowerID to apply them to the account store?
If you are connecting to an Active Directory Forest with multiple domains, you must first create an account store for the forest root domain before creating account stores for other domains in the forest. The proxy account used when adding your AD account store, must have read access to the AD Configuration Partition in order for topology discovery to succeed. Errors will occur if this process and its required access are not followed.
You do not need to enable inventory on the account store created for the forest root domain.
To create an account store for Active Directory via the web site
- From the Navigation Sidebar, expand Admin, then Applications and Directories, and click Account Stores and Systems.
- Click the Actions tab, and then click the Create Account Store action.
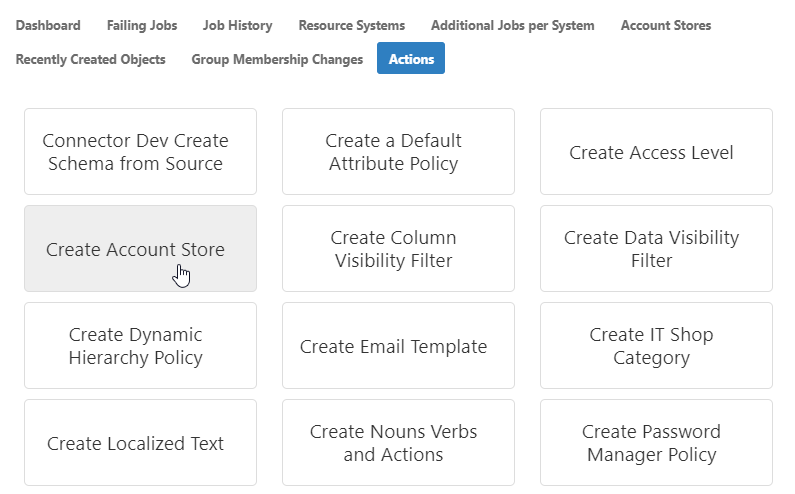
- Search for Active Directory and then click the record for Active Directory Domain Services to select that system type and click Submit.
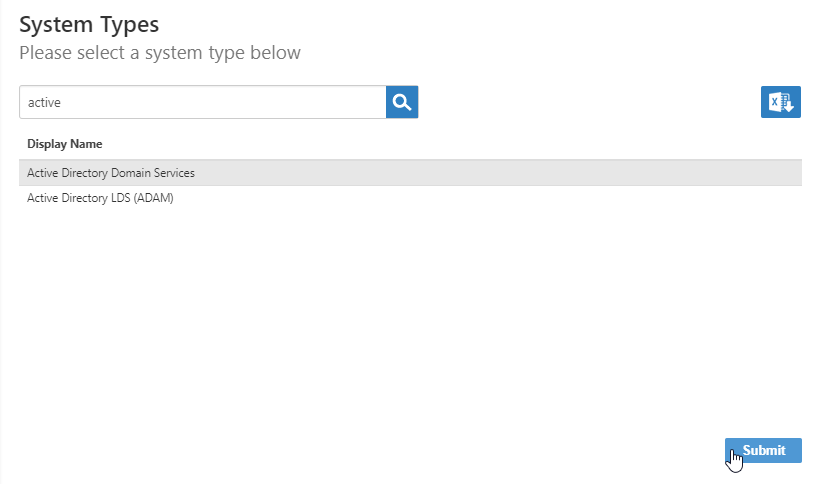
The Active Directory Settings page appears, where you enter settings to connect to your Active Directory to allow EmpowerID to discover and connect to it.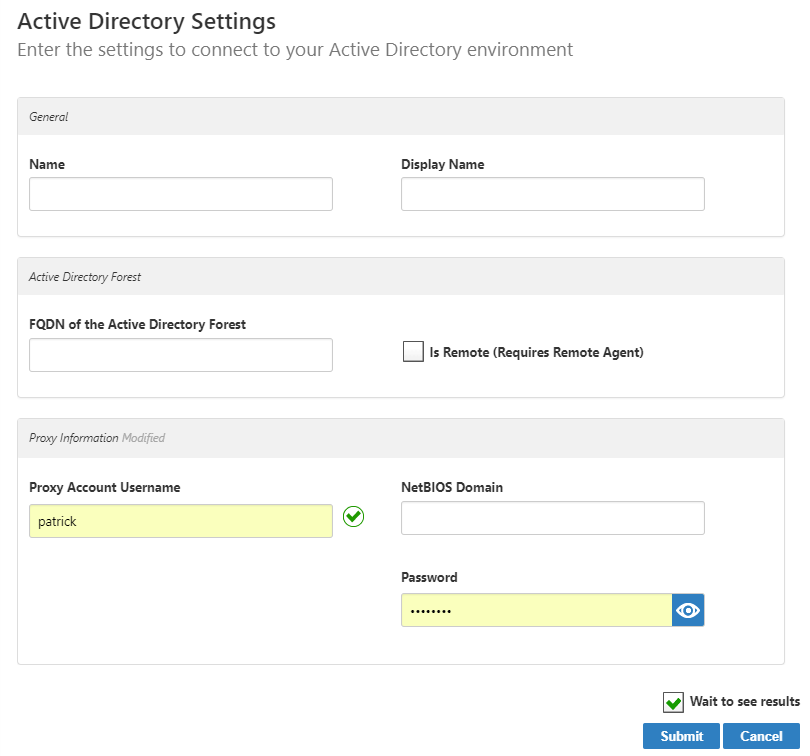
- On the Active Directory Settings page, do the following:
- In the Name and Display Name fields, enter a name for the Active Directory account store.
In the FQDN field, enter the fully qualified domain name of the AD forest.
If you are using LDAPS, enter the Subject name of the certificate for the domain controller to which you are connecting followed by port 636 in the FQDN of Forest field. Thus, if the Subject name is "dc01.eiddoc.com," you enter dc01.eiddoc.com:636.
In the Proxy Account Username field, enter a user account that has read access to the Active Directory configuration partition that holds the list of all of the domains in the forest (and to the Exchange Organization, if present).
In the Account Domain field, enter the NetBIOS name of the domain or child domain that hosts Active Directory.
- In the Password field, enter the password for the proxy account.
Click Submit.
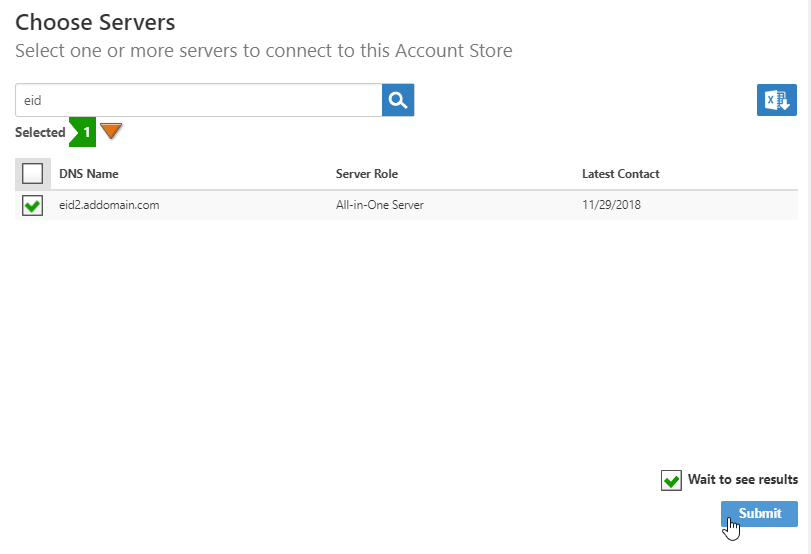
On the Choose Servers page that appears, select the appropriate EmpowerID server and click Submit.
The Choose Servers page displays only those servers where the EmpowerID Web Role service is running. If you do not see your server on the page, check the following:
- Ensure that the server has been assigned either the All-in-One Server or Web Front-End server role.
- Ensure that the EmpowerID Web Role service is running.
(The LDAP Management Host Web Service is responsible for LDAP communications and is enabled by default on each server running the EmpowerID Web Role service.)
Select the server or servers to register and click Submit.All selected servers must be in the same forest and able to communicate with the Active Directory over LDAP port TCP 389.
- On the Discover Active Directory Domains page that appears, select one or more domains to add to the account store and click Submit.
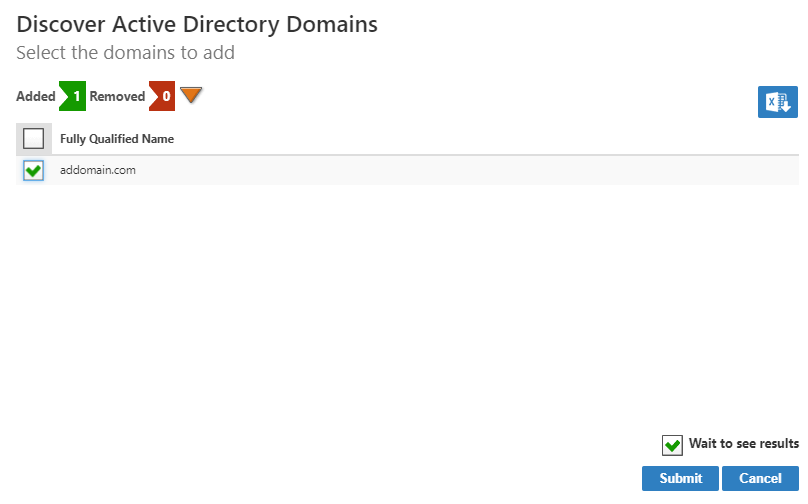
The Account Store is created and appears in the list of Account Stores in both the web application and the Management Console and a corresponding Resource System is created.
To edit account store settings on the web
- In the Navigation Sidebar, expand Admin, then Applications and Directories, and click Account Stores and Systems.
- On the Account Stores tab, search for the account store you just created and click the link to go to its details page.
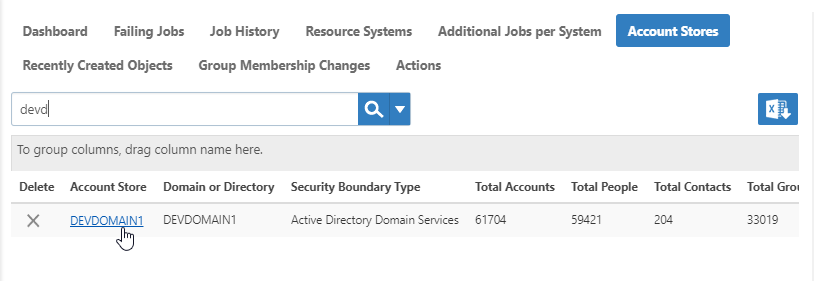
- On the Account Store Details page, click the Edit button or the name of the account store.
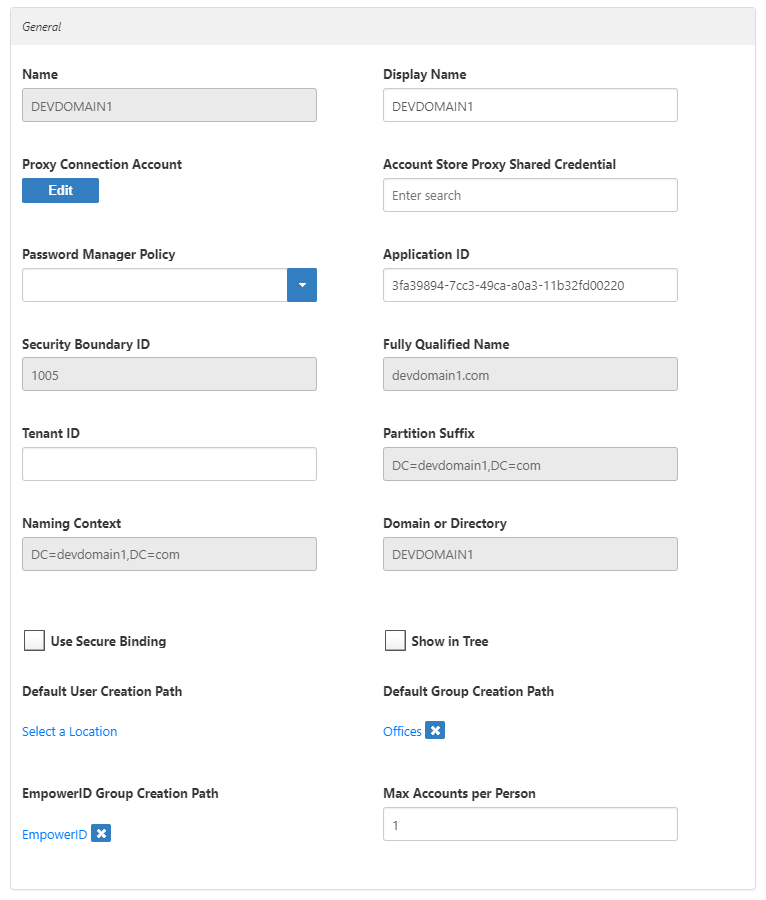
- In the edit view of the page, you can edit values in any of the enabled fields. In the General section, these are:
- Display Name — Edit the name of the account store as it appears in the list of account stores.
- Proxy Connection Account — Change the instance, user name, and password for the connection.
- Account Store Proxy Shared Credential — Click in this box and press Enter to see a list of shared credentials in your system to use for the proxy connection.
- Password Manager Policy — Select a password manager policy to use for the account. If not selected, it uses the Default Password Manager Policy.
- Application ID — If the account store is a one-to-one match with a Tracking Only application, enter the Application Resource GUID of the application. (This value is supplied automatically if you select the Create a New Account Directory option when creating a Tracking Only application.)
- Tenant ID — Enter the Tenant ID, if supplied by the connection account. (AWS uses this.)
- Use Secure Binding — Toggle to bind accounts with encryption.
- Show in Tree — Toggle to show the account store in the Locations tree.
- Default User Creation Path — Select a location in which to create users if none is specified.
- Default Group Creation Path — Select a location in which to create groups if none is specified.
- EmpowerID Group Creation Path — Select a location in which to create EmpowerID groups if none is specified.
- Max Accounts per Person — Enter the maximum number of user accounts from this domain that an EmpowerID Person can have linked to them. This prevents the possibility of a runaway error caused by a wrongly configured Join rule. We recommended setting this value to 1 unless users commonly have multiple accounts and you want them to be joined to the same person.
- In the Features section, you can select any of these values:
- Use for Authentication —
- Allow Search for User Name in Authentication —
- Allow Password Sync — Toggle to allow EmpowerID to sync password changes discovered during inventory.
- Queue Password Changes — Toggle to have EmpowerID send password changes to the Account Password Reset Inbox for batch processing.
- Queue Password Changes on Failure — Toggle to have EmpowerID send password changes to the Account Password Reset Inbox only when the change fails.
- Allow Account Creation on Membership Request — Toggle to allow users without accounts to request group membership and automatically have an account created.
- Batch Calls —
- Allow Attribute Flow — Toggle to allow attribute changes to flow between EmpowerID and the account store.
- Allow Person Provisioning — Toggle to allow EmpowerID to create Person objects from the user records discovered during inventory.
- Allow Provisioning — Toggle to allow EmpowerID to create new Groups in Active Directory from requests discovered during inventory.
- Allow Deprovisioning — Toggle to allow EmpowerID to delete Groups in Active Directory based on requests discovered during inventory.
- Automatic Person Join — Toggle to allow EmpowerID to join newly discovered accounts to people during the inventory process if they meet the Join Rule as specified by the Custom_Account_InventoryInboxJoinBulk SQL stored procedure.
- Automatic Person Provision — Toggle to allow EmpowerID to provision EmpowerID people for new accounts discovered during the inventory process if they meet the Provision Rule specified by theCustom_Account_InventoryInboxGetAccountsToProvision SQL stored procedure.
- Default Provision Business Role — Set a default Business Role to assign people if none is specified.
- Default Provision Location — Set a default Location to assign people if none is specified.
- Allow Business Role and Location Re-Evaluation — Toggle if you have multiple account stores to manage and want to specify a priority for each.
- Business Role and Location Re-Evaluation Order — Enter a number to specify the priority of the account store for determining the Business Roles and Locations to assign to a Person. Account Stores with a higher value take precedence.
- Recertify All Group Changes — Toggle to allow EmpowerID to generate recertification review tasks for all changes in account store groups.

- When you have finished editing, click Save.
To create an account store for Active Directory in EmpowerID Management Console
- Log in to the EmpowerID Management Console as an administrator.
- Click the application icon and select Configuration Manager from the menu.
- In Configuration Manager, select the Account Stores node and then click the Add New button above the grid.
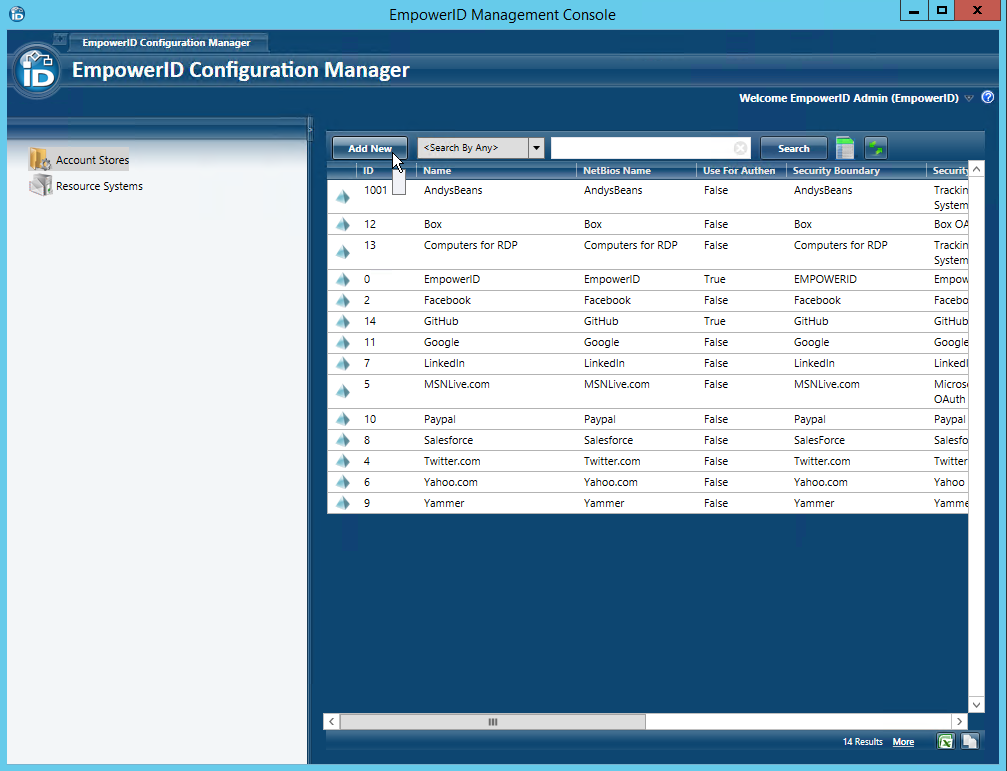
- Select Active Directory Domain Services from the Security Boundary Type drop-down and then click OK.
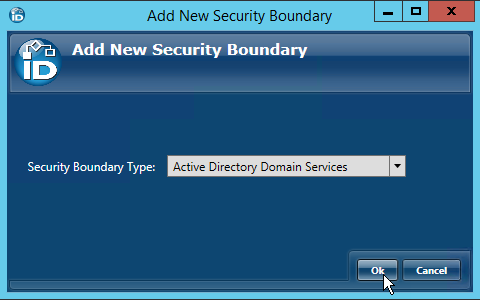
This opens the Discover AD Forest window, which is where you enter the identifying information about your Active Directory to allow EmpowerID to discover and connect to it.
- In the Discover AD Forest window, do the following:
Enter the fully qualified domain name of the AD forest in the FQDN of Forest field.
If you are using LDAPS, you type the Subject name of the certificate for the domain controller to which you are connecting followed by port 636 in the FQDN of Forest field. Thus, if the Subject name is "dc01.eiddoc.com," you enter dc01.eiddoc.com:636.
Enter the proxy information into the fields of the Proxy Information panel.
The user account entered here is saved as the default proxy account (connection credential) used when managing the selected domains; therefore this account must have read access to the Active Directory configuration partition that holds the list of all of the domains in the forest (and to the Exchange Organization, if present). You can change this at any time.
If you are connecting to a child domain, you type that domain in the NetBIOS Name field.
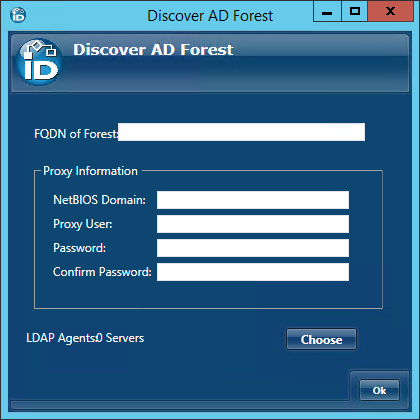
- Click the Choose button below the Proxy Information panel to open the Choose Servers window. This window provides the interface for selecting the server(s) with the EmpowerID Web Role service installed.
In the Choose Servers window, toggle the Server button from a red sphere to a green checkbox for one or more servers running the EmpowerID Web Role service, where the LDAP Management Host Web Service is enabled. (The LDAP Management Host Web Service is responsible for LDAP communications and is enabled by default on each server running the EmpowerID Web Role service.)
Each server selected must be in the same forest and able to communicate with the Active Directory over LDAP port TCP 389. Please note that the EmpowerID Web Role service must be started on a given server before that server will show in the Choose Servers window.

- Click OK to close the Choose Servers window and then click OK to close the Discover AD Forest window.
- In the Discover Active Directory Domains window that appears, select the AD domains you want EmpowerID to manage and then click OK to close the window.
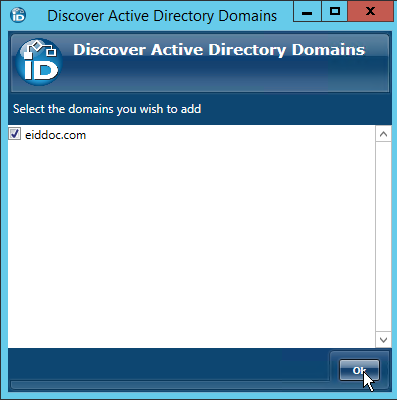
After several moments to perform the requested action, EmpowerID opens the Account Store Details screen for the new account store. This screen provides access to the configuration options for the various jobs that EmpowerID performs against managed domains and is divided into three tabs, the Details tab, the Directory Servers tab, and the UPN Suffixes tab. Of these three tabs, the Details tab is where the majority of the configuration occurs. A general overview of these settings is provided in the drop-downs below. Step-by-step guidance for configuring this screen during your initial configuration follows in the next section.
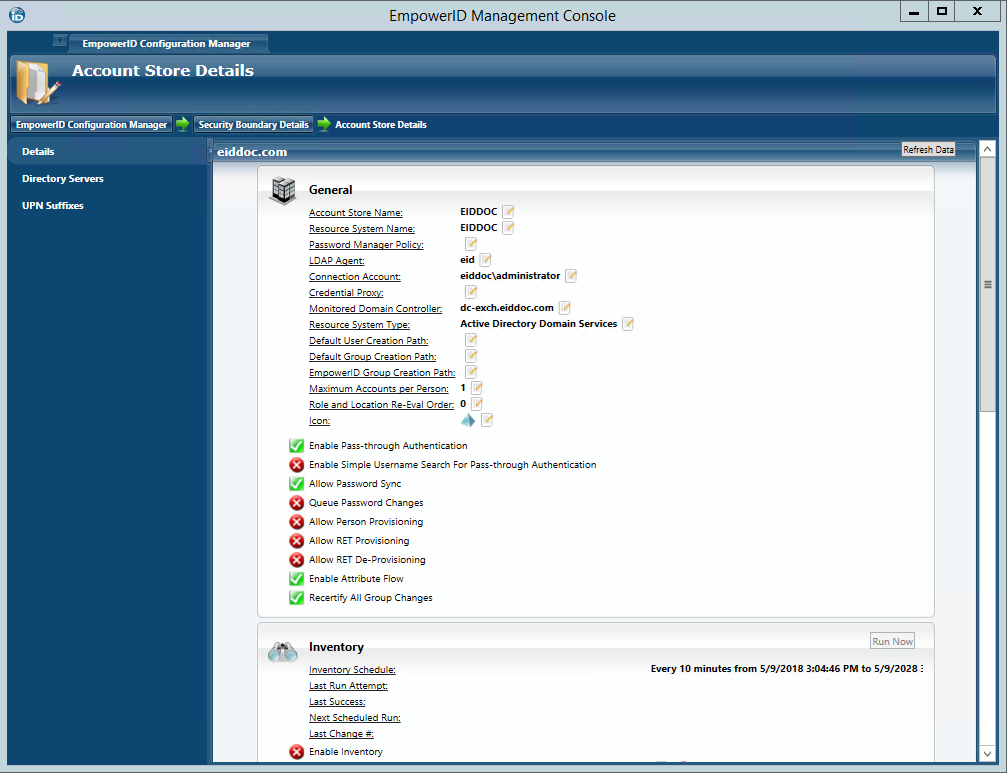
To configure EmpowerID settings for the account store
The Account Store Details screen is divided into three tabs, the Details tab, the Directory Servers tab, and the UPN Suffixes tab. Of these three tabs, the Details tab provides the functionality for configuring how you want EmpowerID to manage the account store and the user accounts it finds therein.
- From the General pane of the Details tab, do the following:
- Click the Edit
 button to the right of Default User Creation Path and select a default location within your directory where EmpowerID is to create users in the event that one is not selected in a workflow process.
button to the right of Default User Creation Path and select a default location within your directory where EmpowerID is to create users in the event that one is not selected in a workflow process. - Click the Edit
 button to the right of Default Group Creation Path and select a default location within your directory where EmpowerID is to create groups in the event that one is not selected in a workflow process.
button to the right of Default Group Creation Path and select a default location within your directory where EmpowerID is to create groups in the event that one is not selected in a workflow process. - Click the Edit
 button to the right of EmpowerID Group Creation Path and select a default location within your directory where EmpowerID is to create the Domain Local groups it uses for granting native AD permissions assignments.
button to the right of EmpowerID Group Creation Path and select a default location within your directory where EmpowerID is to create the Domain Local groups it uses for granting native AD permissions assignments. - Click the Edit
 button to the right of Maximum Accounts Per Person and specify that maximum number of accounts from the domain that a Person can have linked to them. Setting this prevents the possibility of a runaway error caused by a wrongly configured Join rule.
button to the right of Maximum Accounts Per Person and specify that maximum number of accounts from the domain that a Person can have linked to them. Setting this prevents the possibility of a runaway error caused by a wrongly configured Join rule. - If you are managing other account stores in addition to this one, click the Edit
 button to the right of Role and Location Re-Eval Order and enter a number to specify the priority of the account store for determining the Business Roles and Locations that should be assigned to a Person. Account Stores with a higher value take precedence.
button to the right of Role and Location Re-Eval Order and enter a number to specify the priority of the account store for determining the Business Roles and Locations that should be assigned to a Person. Account Stores with a higher value take precedence. - Toggle Enable Pass-Through Authentication to reflect your policy for the account store (red sphere for disable and green checkbox for enable). Pass-through Authentication allows domain authentication to be used for logging in to EmpowerID. Unless Simple Search is enabled, the domain\username format needs to be used.
- Toggle Enable Simple Username Search for Pass-Through Authentication to reflect your policy for the account store (red sphere for disable and green checkbox for enable). Simple search works in conjunction with pass-through authentication to allow users to log in without specifying a domain name. When this is enabled, EmpowerID first checks to see if the user name entered exists within its Identity Warehouse and if so attempts to authenticate as that user. If a matching logon name exists but the login fails, EmpowerID then searches through all account stores where simple search is enabled to find the correct user name and password combination.
- Toggle Allow Password Sync to reflect your policy for the account store (red sphere for disable and green checkbox for enable). When enabled, EmpowerID synchronizes password changes to user accounts in the domain based on password changes for the joined Person or changes on another account owned by the Person.
- Toggle Allow RET Provisioning to reflect your policy for the account store (red sphere for disable and green checkbox for enable). When enabled, EmpowerID auto-provisions accounts for users who receive RET policy-assigned user accounts, but have not yet had them provisioned.
- Toggle Allow RET De-Provisioning to reflect your policy for the account store (red sphere for disable and green checkbox for enable). When enabled, EmpowerID auto de-provisions accounts for users who have RET policy-assigned user accounts, but no longer receive a policy that grants them those user accounts in the domain.
- Toggle Enable Attribute Flow to reflect your policy for the account store (red sphere for disable and green checkbox for enable). When enabled, changes occurring to user attributes in the account store will occur in EmpowerID and vice-versa depending on how you have set up your attribute flow rules. The default flow for most user attributes for active directory is bi-directional. You can change these as needed.
- Click the Edit
- From the Inventory pane of the Account Store Details screen, do the following:
EmpowerID recommends using the Account Inbox to provision Person objects from user accounts. The below information is included to make you aware of the option to provision during inventory.
Toggle Allow Automatic Person Provision On Inventory to reflect your policy for the account store (red sphere for disable and green checkbox for enable). When enabled (and Allow Person Provisioning is enabled for the account store), EmpowerID will provision Person objects for all new accounts discovered during inventory in real-time, if they meet the conditions of your Provision rules.
When provisioning people during inventory, the following options can be set:
- Business Role for New Inventory Provision — This allows you to select an EmpowerID Business Role for all Persons provisioned during inventory. By default, EmpowerID assigns these people to the Temporary Business Role; however, you can pick others by clicking the Edit
 button to the right of the line and selecting the desired Business Role from the Business Role Selector window that appears. If you pick another and wish to remove it in favor of the default, you can do so by clicking the red sphere to the right of the Edit button.
button to the right of the line and selecting the desired Business Role from the Business Role Selector window that appears. If you pick another and wish to remove it in favor of the default, you can do so by clicking the red sphere to the right of the Edit button.
The following image shows the Business Role Selector window with Standard Employee selected. This means that each Person provisioned will given the Standard Employee Business Role rather than the default Temporary Role.
EmpowerID includes the Standard Employee and Temporary Role Business Roles out of the box; however, if you wish to assign new Persons to another Business Role before inventory occurs, you can easily do so. You simply need to create them first. Once created, those additional Business Roles will appear in the Business Role Selector.
For information on creating Business Roles see Creating Business Roles.
- Location for New Inventory Provision — This allows you to select the location that is to be the primary location for the each Person provisioned during inventory. By default, EmpowerID uses the Active Directory OU of the user object as the primary location. If you map these locations to EmpowerID locations before turning on inventory (recommended), the Person objects will be provisioned in the mapped locations. This makes it easier to manage users as the EmpowerID locations mirror your external locations. We discuss mapping locations in the next section below.
- Business Role for New Inventory Provision — This allows you to select an EmpowerID Business Role for all Persons provisioned during inventory. By default, EmpowerID assigns these people to the Temporary Business Role; however, you can pick others by clicking the Edit
- Toggle Allow Automatic Person Join On Inventory to reflect your policy for the account store (red sphere for disable and green checkbox for enable). When enabled (and Allow Person Provisioning is enabled for the account store), EmpowerID will attempt to join any new accounts discovered during inventory if it finds one that matches the conditions of the Join rules for the account store. If this setting is not enabled, EmpowerID will not join secondary accounts to an EmpowerID Person, but will instead provision new EmpowerID Persons for each of those additional accounts.
The last action to perform on this screen is to enable inventory. However, before doing so, it is important to review the attribute flow rules for the account store and to map your directory locations to corresponding EmpowerID locations as these will be used for initial Business Role and Location placement of all provisioned Person objects. We discuss these in the next two sections.
To configure Attribute Flow rules
Open a browser and log in to the EmpowerID Web application.
- From the Navigation Sidebar, expand Admin > Applications and Directories and click Attribute Flow Rules.
From the Attribute Flow Rules page, click the Advanced Search drop-down button, enter the name of the account store for which you want to configure the flow rules and then click Search to filter the rules shown in the grid.
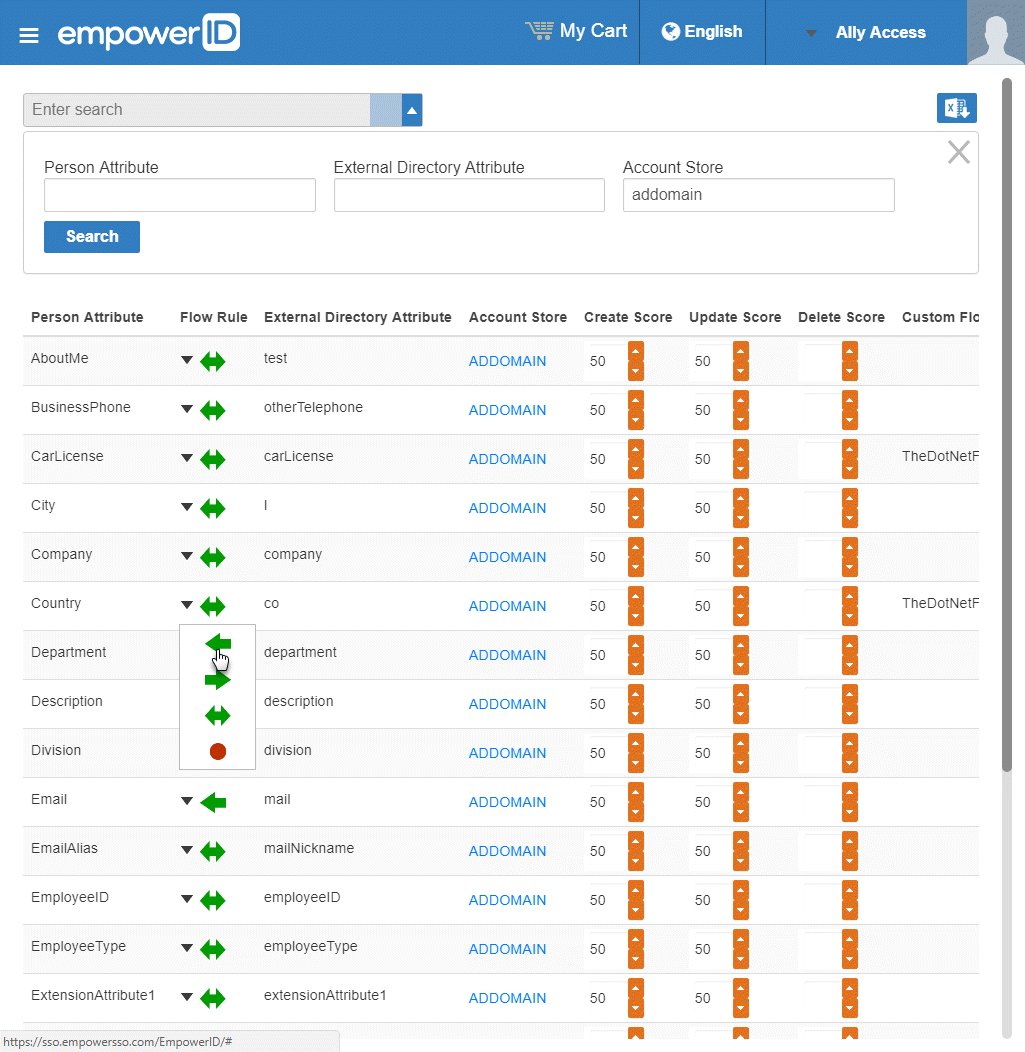
The attributes from the EmpowerID Person object are displayed in the left column with the corresponding attributes from the account store displayed in the right column.
To change the flow for an attribute, click the Attribute Flow drop-down located between the Person Attribute column and the External Directory Attribute column, and select the desired flow direction from the context menu.
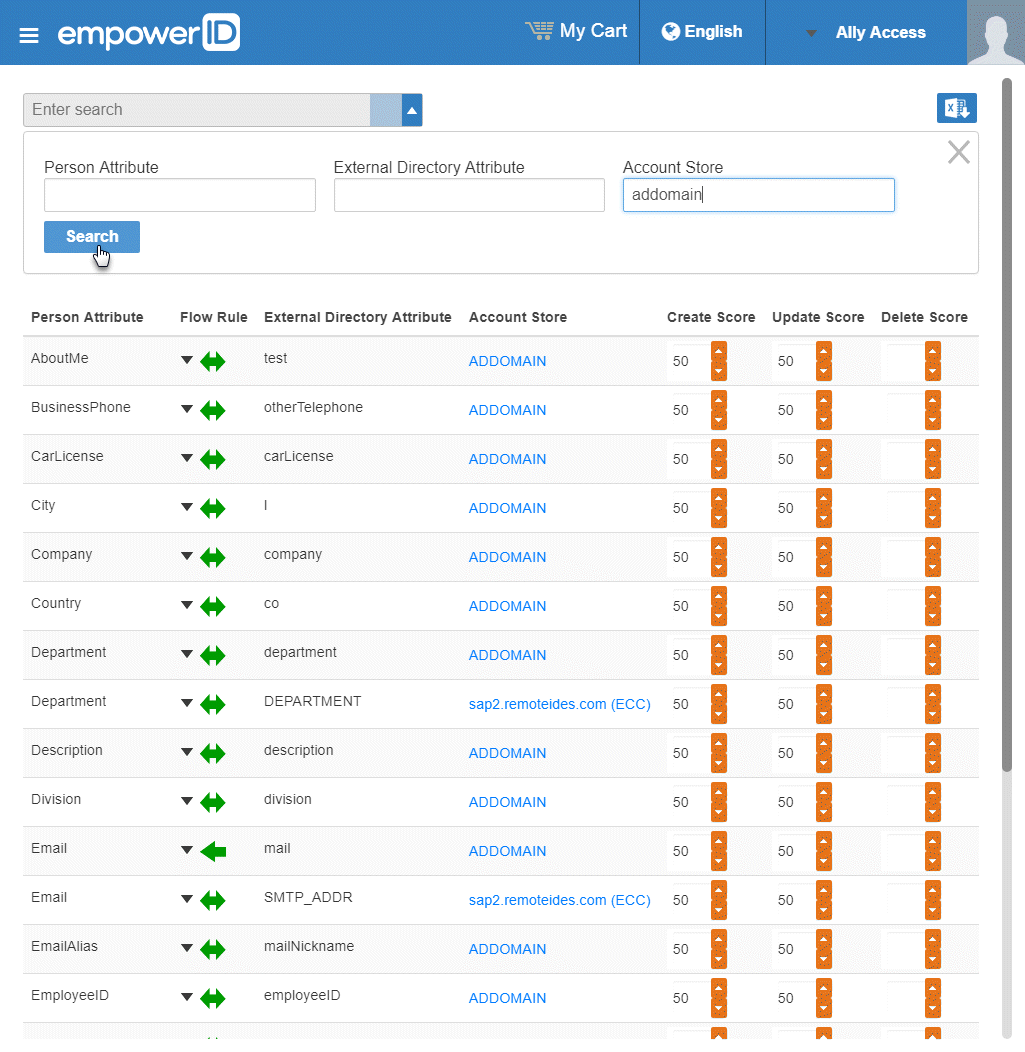
To change the score for any of the available CRUD operations (Create, Update and Delete), enter the new score in the appropriate field. By default, scores are weighted evenly, which means that a change to an attribute originating in one connected external directory has the same authority as a change to an attribute occuring in another connected external directory.
EmpowerID only considers scores for attribute CRUD operations when multiple account stores with the same user records are connected to EmpowerID, such as would be the case if an HR System and Active Directory were being inventoried by EmpowerID.
Next, map the OUs containing user accounts and other managed objects in your account store to corresponding EmpowerID locations as described in the next section. This ensures that the location of an object in EmpowerID reflects the location of the object in Active Directory. In environments with multiple directories or domains, location mapping allows administrators and business users to see one condensed view of the organizations and have policies applied in one spot.
To map locations
EmpowerID Role and Location mappings allow multiple AD, LDAP or other external directory containers to be visually mapped to one or more logical locations in EmpowerID for unified and easy management. When a mapping occurs, all the resources or objects located in the directory container are assigned to a corresponding EmpowerID location, allowing you to use those locations for delegating user access and setting default policy settings. If you create these mappings before your first inventory, all new people discovered by EmpowerID during the inventory process will be provisioned in EmpowerID locations (instead of directory locations), and those EmpowerID locations will be assigned to them as the "Location" portion of their Business Role and Location (BRL). For example, if you have a user named "Barney Smythe" in a London > Contractors OU and a user named "Chris Emerick" in a London > Employees OU and you map both of those London OUs to a single London location in EmpowerID, when you turn on your inventory the Location portion of the BRL for both Barney Smythe and Chris Emerick would be the EmpowerID location and not the external OUs.
To map external locations to EmpowerID locations in the Web interface, you need to create an EmpowerID location for each external location you want to map. For directions on creating EmpowerID locations, expand the the below drop-down.
From the Navigation Sidebar, expand Admin > Applications and Directories and click Role and Location Mapper.
- Select the Location Mapper tab.
From the Location pane of the Location Mapper tab, enter the name of the EmpowerID location you want to map and press ENTER to load the location.
- Select the location from the tree.
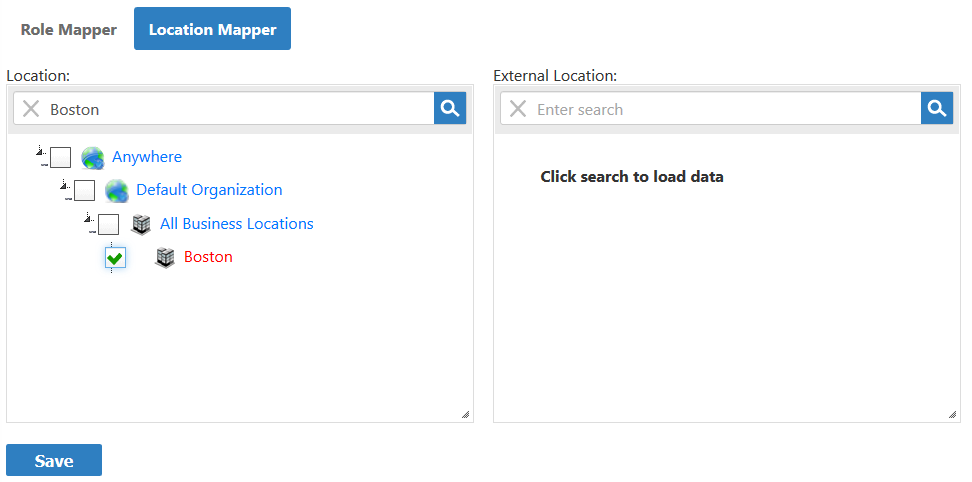
From the External Location pane, enter the name of the external directory location to which you want to map the EmpowerID location.
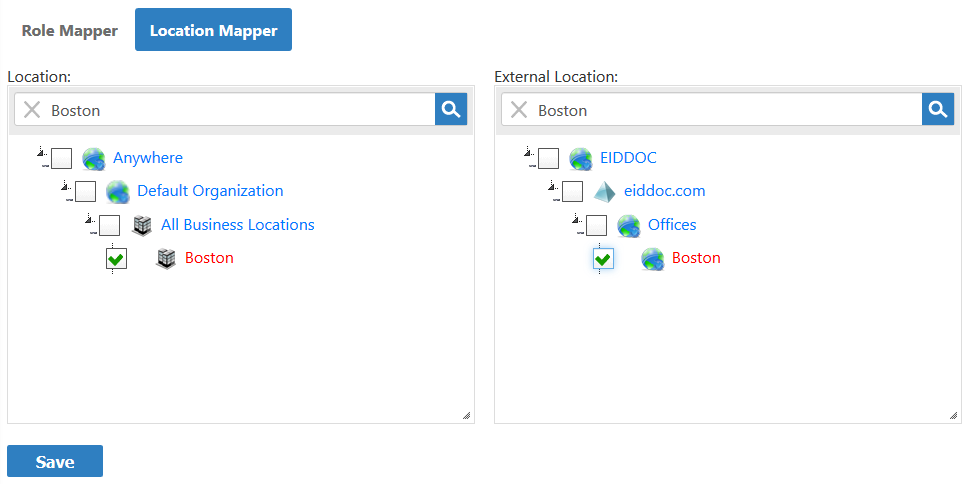
If you select an external location that is a parent location, the children of that location will be mapped to the selected EmpowerID location.
Click Save to save the mapping.
- Repeat for any other mappings you wish to create.
You can view the mapped external locations for any EmpowerID location by expanding the Mapped External Location from the View or View One pages for that location.
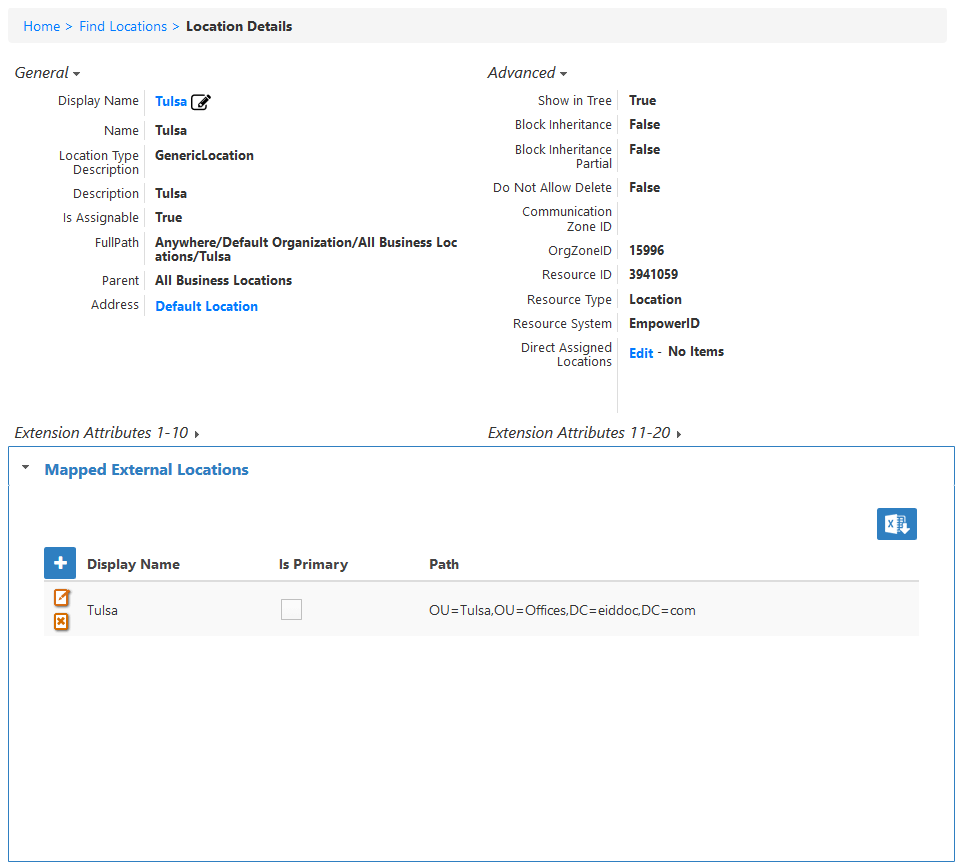
Now that the mappings and attribute flow have been configured, you can enable inventory for the account store as demonstrated below.
To turn on inventory
Return to the Account Store Details screen in Configuration Manager.
Look over your settings one last time and when satisfied, turn on inventory by toggling the Enable Inventory button from a red sphere to a green check box.
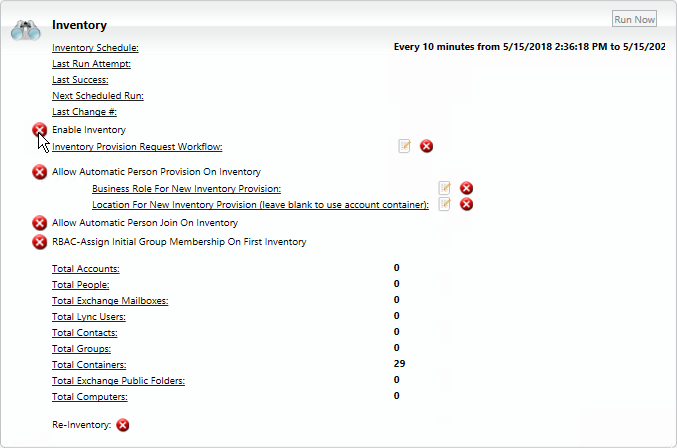
If you want EmpowerID to provision Persons from the user accounts in your Active Directory, you need to enable the Account Inbox permanent workflow. This is demonstrated below.
To enable the Account Inbox permanent workflow
- From the navigation sidebar of the EmpowerID Web interface, expand Admin > EmpowerID Servers and Settings and click Permanent Workflows.
- From the Permanent Workflows page, click the Display Name link for Account Inbox.
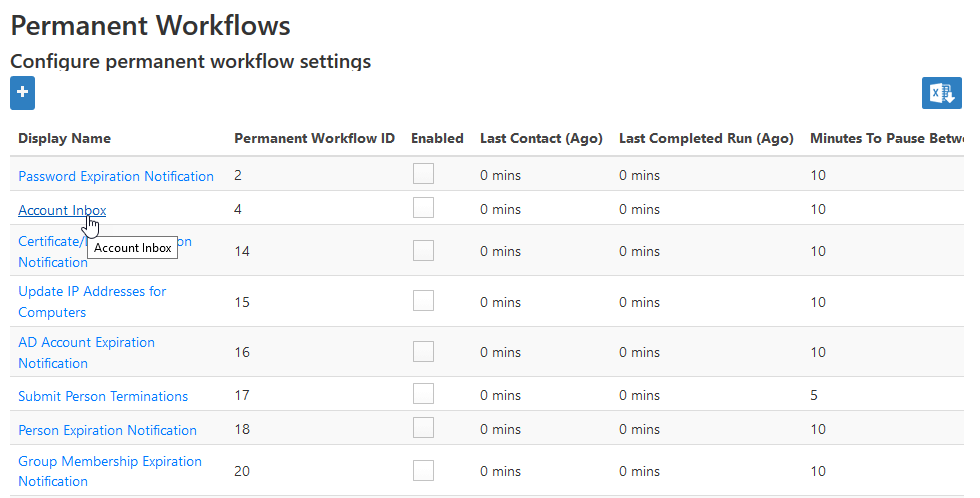
- From the View One page for the workflow that appears, click the edit link for the workflow.
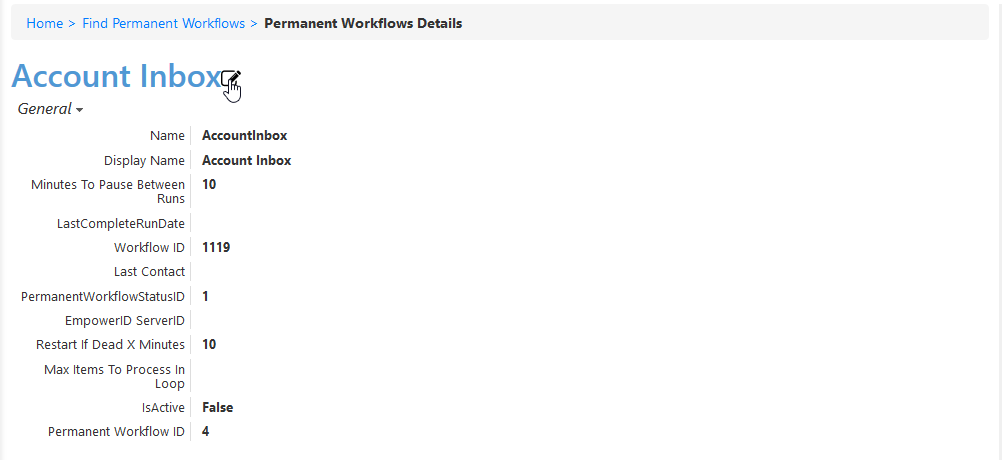
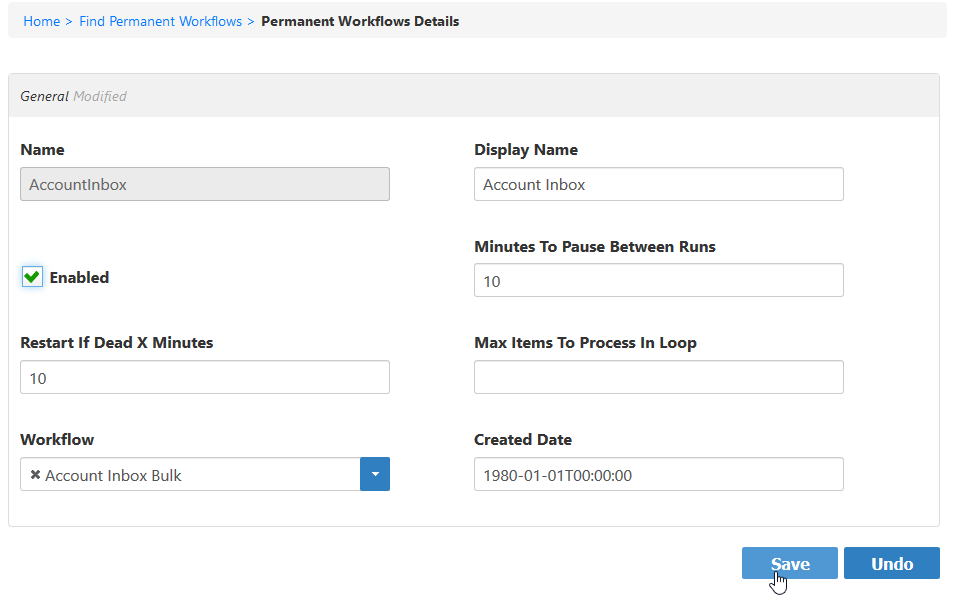
- From the Permanent Workflow Details form that appears, select Enabled and then click Save. Based on the default settings applied to the workflow, EmpowerID will process 1000 of the user accounts in the Account Inbox every ten minutes, provisioning Person objects from those user accounts and joining them together based on the Join and Provision rules applied to the account store.
To monitor inventory
- From Navigation Sidebar, expand System Logs > Policy Inbox Logs and click Account Inbox.
The Account Inbox page appears. This page provides tabbed views of all information related to processing new user accounts discovered in a connected account store during inventory. An explanation of these tabs follows.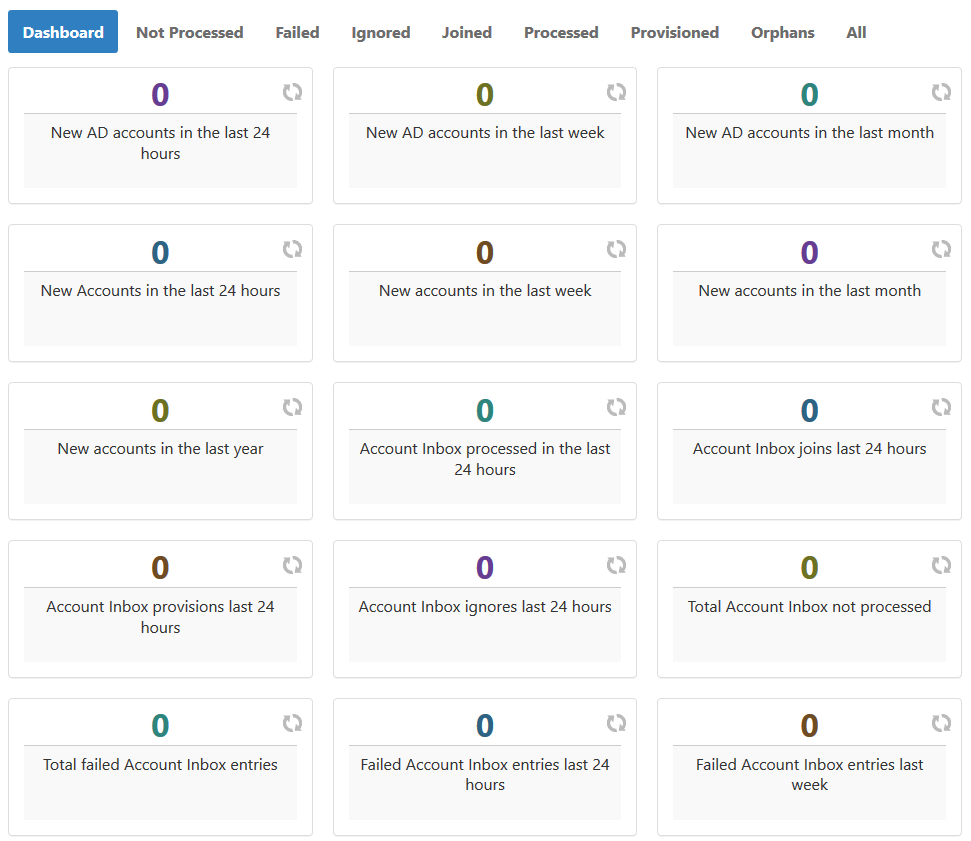
- Dashboard - This tab provides a quick summary of account inbox activity.
- Not Processed - This tab displays a grid view of all inventoried user accounts not yet used to provision a new EmpowerID Person or joined to an existing Person. Any accounts that fail to meet the Join and Provision rules are displayed here as well.
- Failed - This tab displays a grid view of any account joining or provisioning failures.
- Ignored - This tab displays a grid view of all accounts ignored by the account inbox. Accounts are ignored if they do not qualify as user accounts.
- Joined - This tab displays a grid view of all accounts joined to an EmpowerID Person. Joins occur based on the Join rules applied to the account store.
- Processed - This tab displays a grid view of all accounts that have been used to either provision a new EmpowerID Person or joined to an existing EmpowerID Person.
- Provisioned - This tab displays a grid view of all accounts that have been used to provision an EmpowerID Person. Provisioning occurs based on the Provision rules applied to the account store.
- Orphans - This tab displays a grid view of all user accounts without an EmpowerID Person.
- All - This tab displays a grid view of all user accounts and the status of those accounts in relation to the Account Inbox.