EmpowerID maintains permanent logs of all activity and transactions that occur in the system. These All User logins as well as all activity within the EmpowerID system that impacts any protected resource object in the Identity Warehouse is logged in detail with date, time, initiator, approver, target, and other ancillary information regarding the transaction. You can view these by expanding System Logs in the EmpowerID Web interface. Log events are categorized by type and include the following:
Audit Log
You can view these logs in the Web interface by expanding System Logs and clicking Audit Log.
Operation Audit Log — All activity within the EmpowerID system that impacts any protected resource object
...
, such as user accounts, person objects and groups, is logged in detail with date, time, initiator, approver, target, and other ancillary information regarding the transaction.
Attribute Changes
...
— EmpowerID monitors any changes currently taking place within your directories and between EmpowerID and those external directories. Changes detected in external systems can be viewed under Inbound Attribute Changes while any changes occurring within EmpowerID that are being passed to another system can be viewed under Outbound Attribute Changes. Outbound changes are processed by the Directory Change Processor job.
...
New Objects
...
— The EmpowerID inventory engine monitors all connected systems for changes. One primary type of change detected is the creation of
...
new
...
objects within managed systems, such as Azure Active Directory or SharePoint online.
...
Membership Changes
...
— EmpowerID's inventory process detects all changes to group membership and logs these changes for reporting and enforcement purposes. Both changes made via EmpowerID workflows as well as changes to group memberships made outside of EmpowerID with native tools are captured and classified by the change source
...
Policy Inbox Logs
- Account Inbox — The Account Inbox provides views can be accessed from the Web interface by expanding System Logs > Policy Inbox Logs and clicking Account Inbox.
- Dynamic Hierarchy Inbox —
- Provisioning (RET) Inbox —
- Account Password Reset Inbox —
- System Change Outbox —
Login History
RDP/SSH Sessions
Delayed Tasks
All Business Processes
Reports
...
.
Reports
EmpowerID provides over 75 reports out of the box to allow you to view information about the current status of your environment. Each report provides information pertinent to the resource type associated with the report, is searchable and provides links to initiate related workflows or view a specific resource contained in the report. Additionally, each grid in the user interfaces provides an Export button that allows you to download grid information as an Excel sheet.
Reports can be accessed by clicking Reports under System Logs.
| Rw ui expands macro | ||||
|---|---|---|---|---|
|
System Change Outbox
The system change outbox detects changes
Inbox Logs
Account Inbox
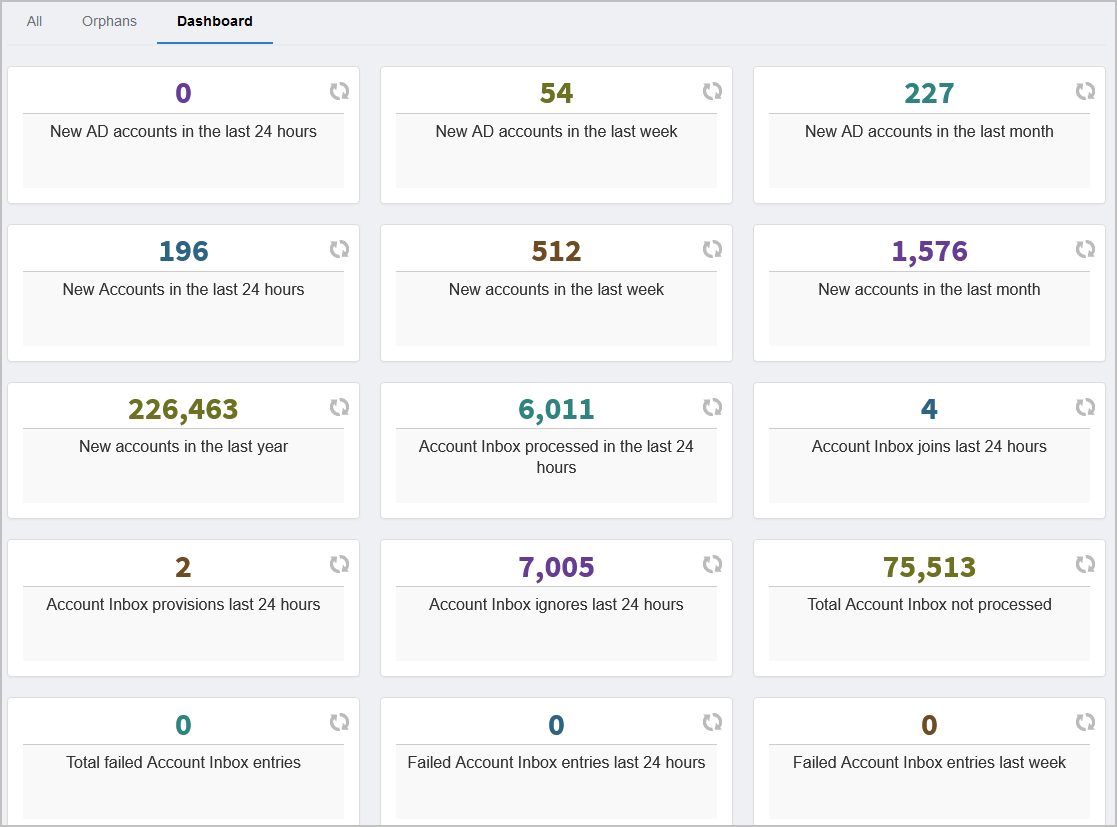
EmpowerID flows all new accounts though the Account Inbox, which determines — based on configurable join and provision rules — whether the new account is an account that should be joined to an existing person, an account that needs to have a new person provisioned for it, or an account that should be ignored. The Account Inbox can be accessed by expanding Identity Lifecycle and clicking Account Inbox.
...
The Account Inbox provides three log views.
All — Displays all external accounts that have been processed by the Account Inbox and their status within the system.
Processed (Ago) — The time and date the external account was processed by the inbox
Result — The processing result for the account
No result — The account has not been processed
Ignored — The account does not meet the conditions specified by the Join and Provision Rules, i.e., it is not a user account
Provisioned — The account does not meet the condition of the Join rule, but it is a user account. An new EmpowerID Person has been provisioned and joined to the account
Joined — The account meets the conditions of the Join rule and has been joined to an existing EmpowerID Person
Logon Name — The logon name of the account
Domain or Directory — The domain from where the account was inventoried
Login — The login of the EmpowerID Person that was provisioned or joined to the account, if any.
Process Status — Displays whether the account was processed by the Account Inbox.
0 — Unprocessed
1 — Ignored
2 — Processed
Display Name — The name for the user account in the EmpowerID user interfaces
Deleted — Displays whether the account has been deleted in EmpowerID
Distinguished Name — Distinguished name of the account in EmpowerID
Person Deleted — Displays whether the Person linked to the account has been deleted in EmpowerID
Created Date — Date and time the account was created in EmpowerID
Processed By Server — The server that processed the account entry
Orphans — Displays all user accounts not linked to an EmpowerID Person.
Logon Name — The logon name of the account
Domain or Directory — The domain from where the account was inventoried
Usage Type — The type of account
Display Name — The name for the account in the EmpowerID user interfaces
Description — Description of the account
Disabled — Whether the account is disabled
Distinguished Name — Distinguished name of the account in EmpowerID
First Name — First name, if any
Last Name — Last name, if any
Dashboard — Provides a visual summary of Account Inbox information.
Provisioning (RET) Inbox
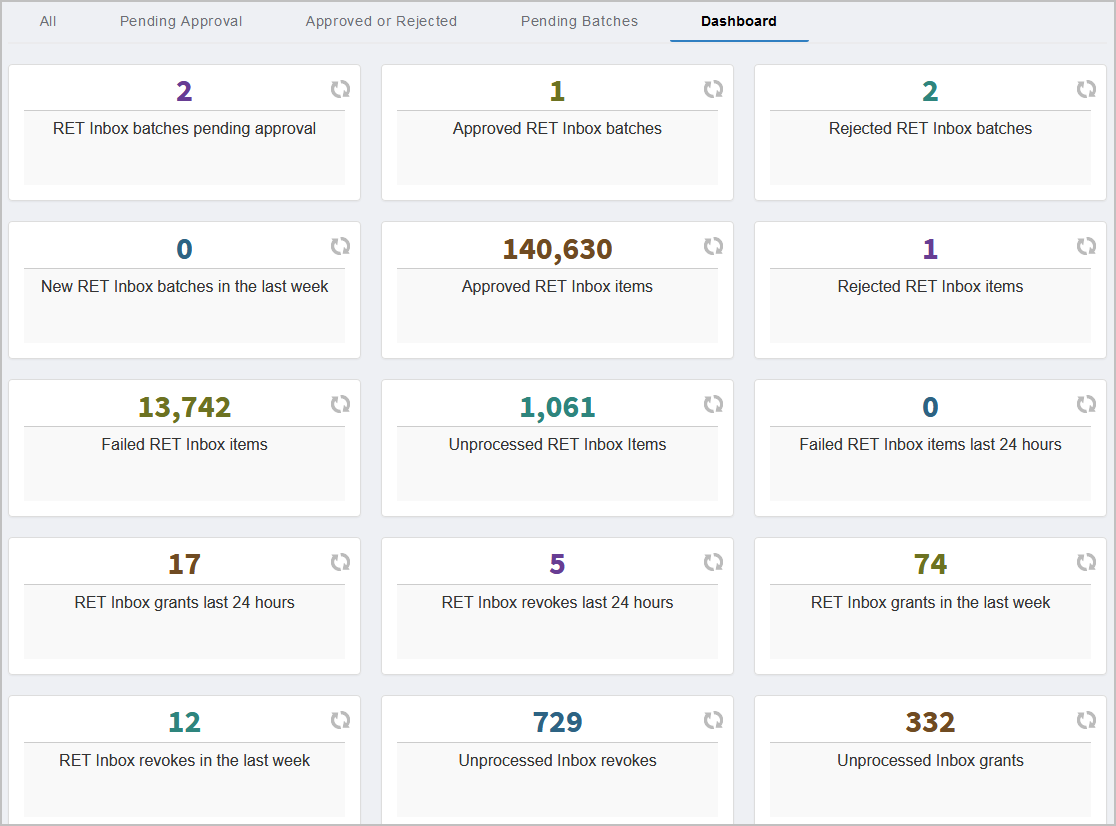
The Provisioning (RET) Inbox continuously evaluates Provisioning (RET) policies, comparing those policies to information obtained from connected directories and resource systems. The inbox process determines mismatches between the resources (user accounts, mailboxes, etc.) a person should have (according to the RET policies they receive) and the resources they actually have. If mismatches are present, entries are created in the RET Inbox to record what provisions, de-provisions, or moves are required to rectify these differences. EmpowerID then processes those changes to perform the recommended actions. The RET Inbox can be accessed by expanding Identity Lifecycle and clicking Provisioning (RET) Inbox.
...
The Provisioning (RET) Inbox provides the below log views.
All — Displays all resource entitlement entries in the Provisioning (RET) Inbox.
ID — Unique identifier for the entry
Processed (Ago) — Hours and minutes from the current time that the entry was processed
RET Action — Displays the action to be taken by the system for the entry
Grant
Revoke
Entitlement Type — The resource to be granted or revoked, i.e., Azure AD User Account
Processed By Server — The server that processed the entry
Resource — Provides a link to the View page for the specific resource processed for the entry
Resource System — The resource system, i.e., Azure tenant, where the entitlement was granted or revoked
EmpowerID Login — The login of the EmpowerID Person receiving the resource entitlement action
Resource Entitlement (Provisioning Policy) — The Provisioning policy linked to the resource entitlement
Process Status — Displays the process status of resource entitlement entry
Not processed
In Progress
Processed
Error
Ignored
Pending Reprocessing
Failed Count — The number of times processing the resource entitlement failed, if any.
Last Failed — The date and time of the last failure to process the resource entitlement, if any.
Person Display Name — Display name of the Person receiving the resource entitlement
Created (Ago) — The time and date the resource entitlement was processed by the system
Priority (Lower is Higher Priority) — Priority of the resource entitlement as set by the policy
Display Name — Display name, if any
Object Class — Object class of the provisioned resource
Path — Path of the provisioned resource, if any
Processed By Server — Server that processed the inbox entry
Approved — Displays whether the resource entitlement was approved by a person
Auto Process — Displays whether the resource entitlement was auto-processed by the system
Reviewer — The person who reviewed the resource entitlement, if any
Reviewed Date — The date the resource entitlement was reviewed, if any
Pending Approval — Displays all resource entitlements that need to be approved before the system provisions those entitlements.
ID — Unique identifier for the entry
Batch ID — N/A
Processed By Server — N/A
Approve — Provides a drop-down of approval actions visible to delegated users
Approve
Reject
Processed (Ago) — Value should be 0 mins
RET Action — Displays the action (grant or revoke) for the resource entitlement entry as specified by the RET policy
Entitlement Type — The type of resource to be provisioned or revoked for the entry, i.e., Windows Home Folder
Resource System — The system where the entitlement is to be provisioned or revoked
EmpowerID Login — The login for the EmpowerID Person receiving the entitlement
Resource Entitlement (Provisioning Policy) — The Provisioning policy linked to the resource entitlement
Process Status — Not Processed
Person Display Name — Display name of the EmpowerID Person targeted by the
Created (Ago) — Number of days from the current day that the entry was created
Priority (Lower is Higher Priority) — Priority of the resource entitlement as set by the policy
Display Name — N/A
Object Class — N/A
Path — N/A
Processed By Server —N/A
Auto Matched — N/A
Approved or Rejected — Displays all resource entitlements that have been approved or rejected by status.
Approved — True or false
Reviewer — PersonID link of the person who approved or rejected the resource entitlement. Clicking the link opens the Person View page in another tab
Reviewed Date — The number of days, hours and minutes from current that the entry was reviewed by the reviewer, if any
ID — Unique identifier for the entry
Batch ID — Unique identifier of the batch containing the entry
Processed (Ago) — The number of days, hours and minutes from current that the entry was processed by the system
Processed By Server — The server that processed the entry, if any
RET Action — Displays the action ( grant or revoke) for the resource entitlement entry as specified by the RET policy
Entitlement Type — Type of resource for the entry, i.e., Azure AD User Account
Resource — The person to whom the resource would be granted or revoked
Resource System — The system where the entitlement is to be provisioned or revoked once approved
EmpowerID Login — The login of the EmpowerID Person receiving the resource entitlement action
Resource Entitlement (Provisioning Policy) — The Provisioning policy linked to the resource entitlement
Process Status — Displays the process status of resource entitlement entry
Person Display Name — Display name of the EmpowerID Person targeted by the
Created (Ago) — Number of days, hours and minutes from the current that the entry was created
Priority (Lower is Higher Priority) — Priority of the resource entitlement as set by the policy
Display Name — Display name, if any
Object Class — Object class of the resource
Path — Path of the provisioned resource, if any
Processed By Server — Server that processed the inbox entry
Auto Process — Displays whether the resource entitlement was auto-processed by the system
Pending Batches — Displays all resource entitlement batches pending approval in the system.
Approve — Provides a drop-down of approval actions visible to delegated users
Approve
Reject
Batch ID — Unique identifier of the batch containing the entry
Batch Count — Number of entries in the batch
Processed By Server — N/A
Resource Type — Type of resource in the batch, i.e., User Account
Resource System — The system where the entitlements are to be provisioned or revoked once approved
Resource Entitlement (Provisioning Policy) — The Provisioning policy linked to the resource entitlement
Created (Ago) — Number of days, hours and minutes from the current that the entry was created
Dashboard — Provides a visual summary of Provisioning (RET) Inbox information.
Login History
EmpowerID automatically logs all login attempts to EmpowerID or to any system using EmpowerID for login authentication. The Login History log provides a convenient searchable view of these login events. The log can be viewed by expanding Single Sign-On and clicking Login History.
...
The Login History provides the below logging views.
Login History — Displays all logins for all users.
When (Ago) — The number of days, hours and minutes from current that the login attempt occurred
Message — Displays details about the login attempt and the reason for failure, if any
Who — The person who attempted to log in; could be anonymous
Successful — Displays whether the login attempt succeeded
Message — Displays details about the login attempt and the reason for failure, if any
Level of Assurance (LoA) — Number of points required for the login, if any. This is derived from the Password Manager Policy of the person.
Speed (Miles per Hour) — Speed traveled for login, if any
EmpowerID Login — The EmpowerID login of the person
Identity Provider — The IdP used to authenticate the person
Service Provider — The SP
Device — Device used to login
Method — Login method, i.e., WEB
IP — IP recorded for the login attempt
City — City from where the login attempt originated
State — State from where the login attempt originated
Country — Country from where the login attempt originated
Organization — Organization of the person attempting to log in
User Name — User name of the person
Failure Reason — Reason for login failure, if any
Date — Date and time of the login attempt
Browser Technical Details — Browser used
My Reports Logins — Displays all logins for the direct reports of the current user
When (Ago) — The number of days, hours and minutes from current that the login occurred
Person — Person who attempted to log in
Method — Login method, i.e., WEB
Successful — Displays whether the login attempt succeeded
EmpowerID Login — The EmpowerID login of the person
Identity Provider — The IdP used to authenticate the person
Service Provider — The SP
Device — Device used to login
Level of Assurance (LoA) — Number of points required for the login, if any. This is derived from the Password Manager Policy of the person.
IP — IP recorded for the login attempt
Speed (Miles per Hour) — Speed traveled for login, if any
City — City from where the login attempt originated
State — State from where the login attempt originated
Country — Country from where the login attempt originated
Organization — Organization of the person attempting to log in
Message — Displays details about the login attempt and the reason for failure, if any
Failure Reason — Reason for login failure, if any
When — Date and time login attempt occurred
Recent Login Sessions — Displays all login sessions occurring within the last 48 hours
When (Ago) — Displays the number of days, hours and minutes from now that the login session occurred within the last 48 hours
Person Display Name — Display Name of the Person who logged in
User Name — User name of the person
Identity Provider — The IdP used to authenticate the person
Service Provider — The SP
IP Address — IP address recorded for the login session
Device — Device used to login
Level of Assurance (LoA) — Number of points required for the login, if any. This is derived from the Password Manager Policy of the person.
Workflow Errors
The Workflow Error Log captures any exceptions thrown by EmpowerID during a workflow execution which and provides a convenient way to locate problems when troubleshooting. The log displays fields that allow you to view where the error occurred, what account and which person was executing the workflow, the severity of the error, and other values. The Workflow Error log can be viewed by expanding Infrastructure Admin > EmpowerID Servers and Settings and clicking Workflow Errors.
...
| Insert excerpt | ||||||
|---|---|---|---|---|---|---|
|