- Created by Universal Importer for Confluence, last modified by Kim Landis on Sept 14, 2018
You are viewing an old version of this page. View the current version.
Compare with Current View Page History
« Previous Version 7 Next »
EmpowerID provides connectors for a wide range of user directories and resource systems. As an administrator, you can use these connectors to quickly connect EmpowerID to your organization's identity-aware systems and applications. When you do so, you create an account store for that application in the EmpowerID Identity Warehouse and use that account store to configure how you want EmpowerID to manage the identity information in that system.
If you have Windows servers with local users and groups, you can add those servers to EmpowerID as managed account stores. This allows you to inventory local users and groups and manage those objects from EmpowerID, providing you with automated role-based access control, delegated permissions administration, and provisioning policy capabilities with a full audit trail of any actions involving those objects.
EmpowerID uses WinNT directory entry calls to get the objects on local Windows servers and WMI to get the group membership. As WMI is used, the Remote Procedure Call (RPC) Service on the local server must be enabled. For information on configuring WMI, see Configuring WMI. You should ensure WMI is configured correctly before proceeding to add your local Windows servers to EmpowerID.
Adding Windows Local Servers to EmpowerID involves the following tasks:
- Adding Local Windows Servers to EmpowerID as an account store
- Configuring EmpowerID options for managing the Local Windows Server account store and turning on inventory
To create an account store for a local Windows users via the web site
- From the Navigation Sidebar, expand Admin, then Applications and Directories, and click Account Stores and Systems.
- Click the Actions tab, and then click the Create Account Store action.
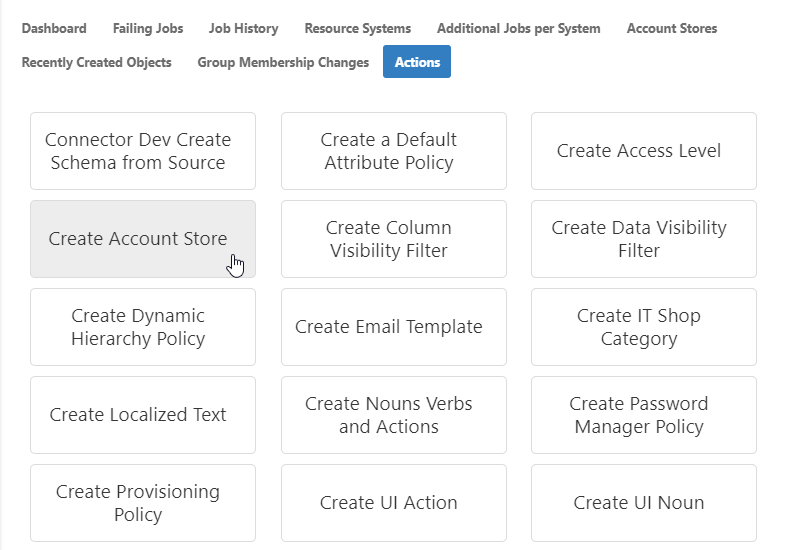
- Select Local Windows Users from the list of Security Boundary types and click Submit.
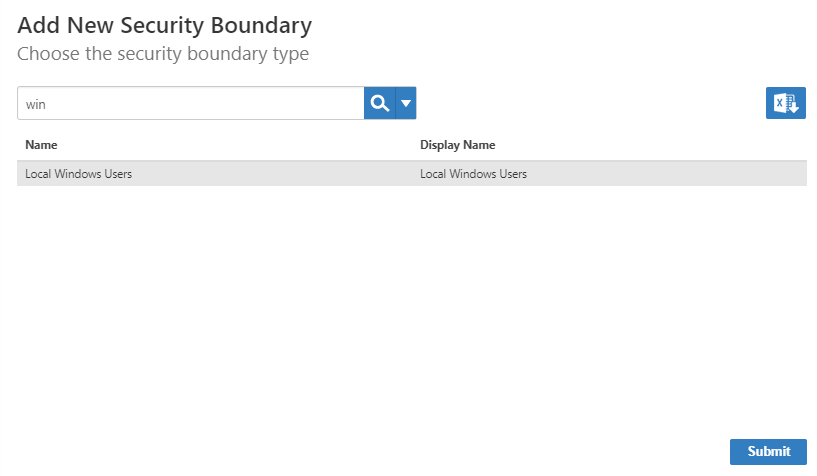
The Local Windows Server Settings page appears, where you enter settings to connect to your local server to allow EmpowerID to discover and connect to it. - On the Local Windows Server Settings page, do the following:
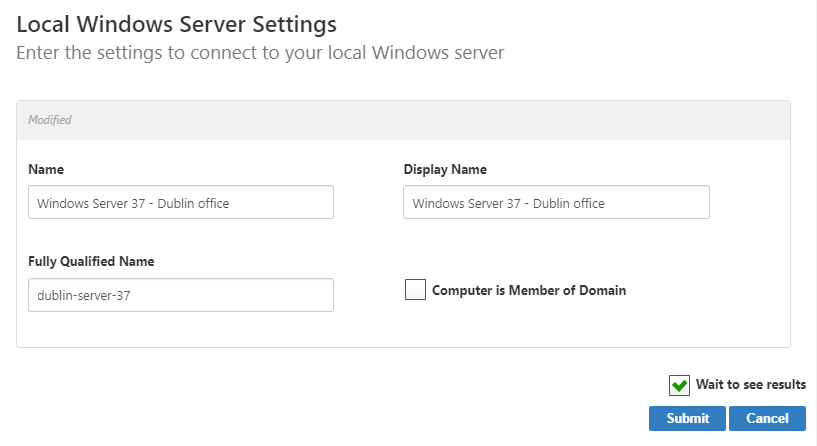
- In the Name and Display Name fields, enter a name for the server account store.
- Fully Qualified Name - Your server's fully-resolvable DNS
Computer is Member of Domain - Select only if your server belongs to a domain that is already inventoried by EmpowerID.
Selecting this option tells EmpowerID not to create a new computer object for the server and to link it to the already-inventoried domain computer.
Leaving it cleared tells EmpowerID to create a new computer object for the server so that the server is visible in EmpowerID.
- Click Submit.
- The Account Store and associated Resource System are created and appear in both the web application and in the Management Console.
To edit account store settings on the web
- In the Navigation Sidebar, expand Admin, then Applications and Directories, and click Account Stores and Systems.
- On the Account Stores tab, search for the account store you just created and click the link to go to its details page.
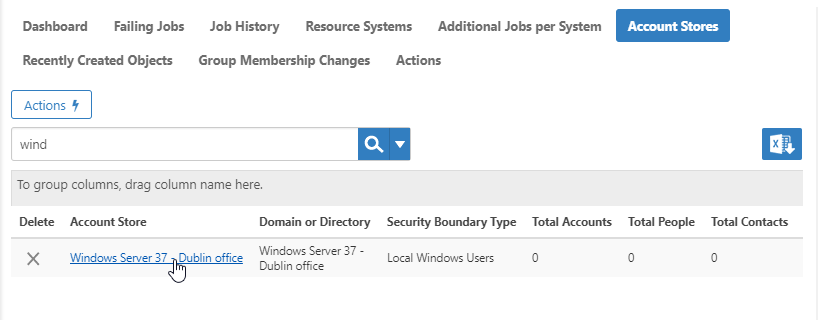
- On the Account Store Details page, click the Edit button or the name of the account store.
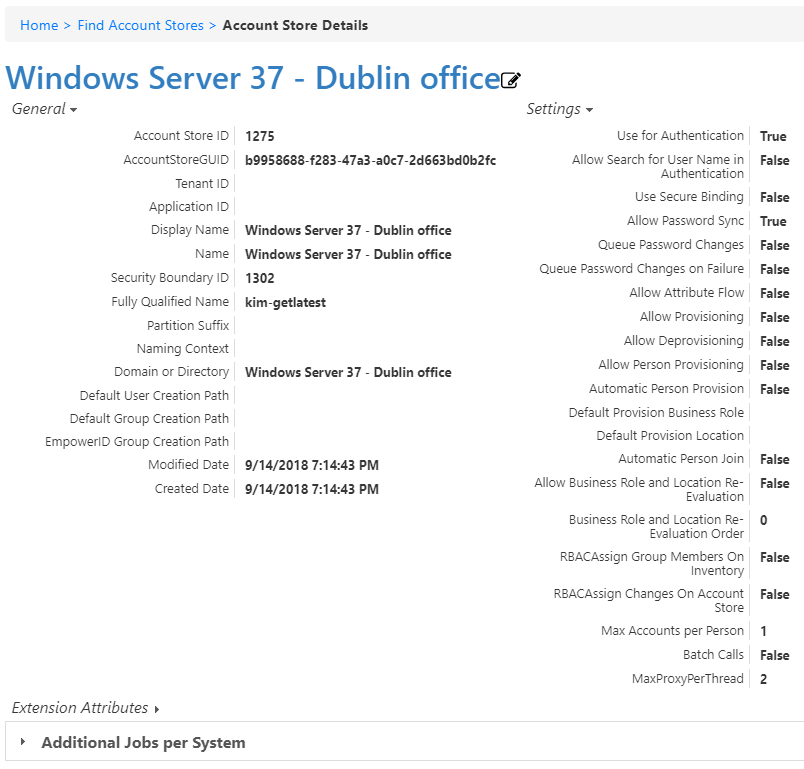
- In the edit view of the page, you can edit values in any of the enabled fields. In the General section, these are:
- Display Name – Edit the name of the account store as it appears in the list of account stores.
- Proxy Connection Account – Change the instance, user name, and password for the ServiceNow connection.
- Account Store Proxy Shared Credential – Click in this box and press Enter to see a list of shared credentials in your system to use for the proxy connection.
- Password Manager Policy – Select a password manager policy to use for the account. If not selected, it uses the Default Password Manager Policy.
- Application ID –
- Tenant ID –
- Use Secure Binding – Toggle to bind accounts with encryption.
- Show in Tree – Toggle to show the account store in the Locations tree.
- Default User Creation Path – Select a location in which to create users if none is specified.
- Default Group Creation Path – Select a location in which to create groups if none is specified.
- EmpowerID Group Creation Path – Select a location in which to create EmpowerID groups if none is specified.
- Max Accounts per Person – Enter the maximum number of user accounts from this domain that an EmpowerID Person can have linked to them. This prevents the possibility of a runaway error caused by a wrongly configured Join rule. We recommended setting this value to 1 unless users commonly have multiple accounts and you want them to be joined to the same person.
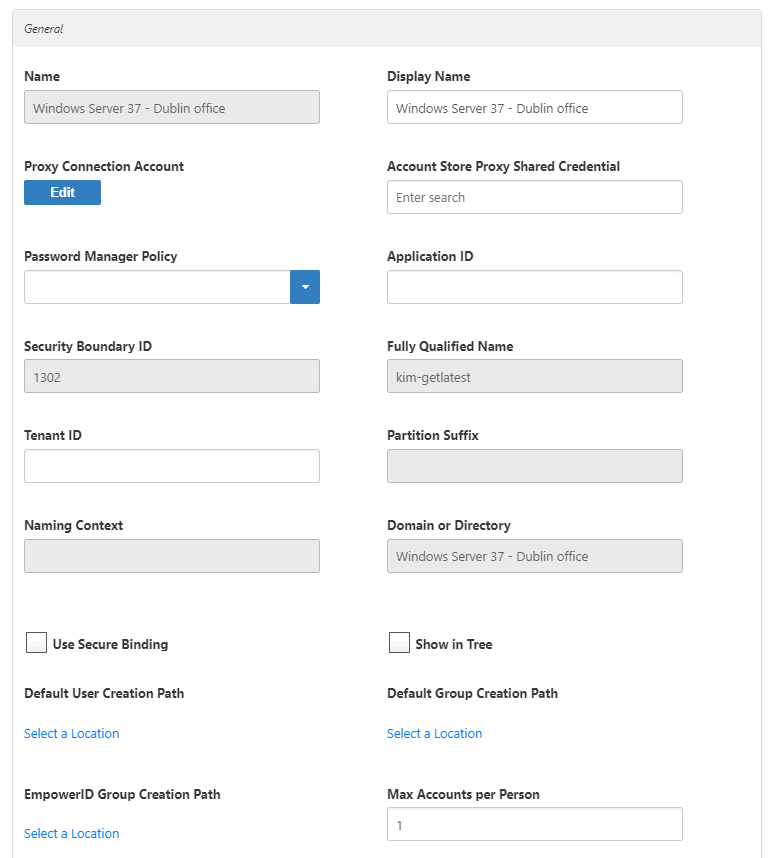
- In the Features section, you can select any of these values:
- Use for Authentication –
- Allow Search for User Name in Authentication –
- Allow Password Sync – Toggle to allow EmpowerID to sync password changes discovered during inventory.
- Queue Password Changes – Toggle to have EmpowerID send password changes to the Account Password Reset Inbox for batch processing.
- Queue Password Changes on Failure – Toggle to have EmpowerID send password changes to the Account Password Reset Inbox only when the change fails.
- Allow Account Creation on Membership Request – Toggle to allow users without accounts to request group membership and automatically have an account created.
- Batch Calls –
- Allow Attribute Flow – Toggle to allow attribute changes to flow between EmpowerID and the account store.
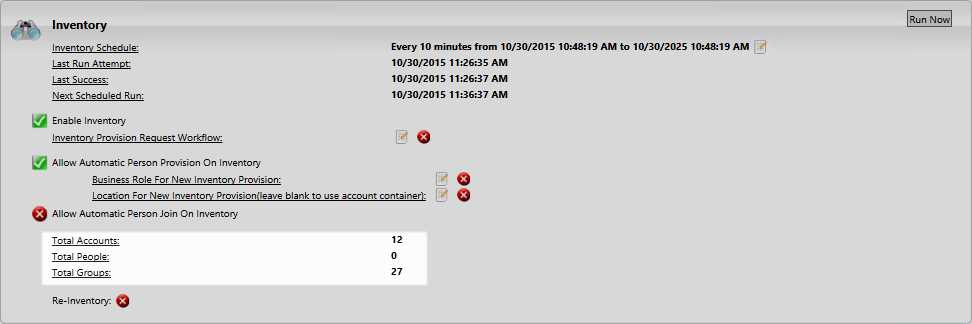
- Allow Person Provisioning – Toggle to allow EmpowerID to create Person objects from the user records discovered during inventory.
- Allow Provisioning – Toggle to allow EmpowerID to create new Groups in ServiceNow from requests discovered during inventory.
- Allow Deprovisioning – Toggle to allow EmpowerID to delete Groups in ServiceNow based on requests discovered during inventory.
- Automatic Person Join – Toggle to allow EmpowerID to join newly discovered accounts to people during the inventory process if they meet the Join Rule as specified by the Custom_Account_InventoryInboxJoinBulk SQL stored procedure.
- Automatic Person Provision – Toggle to allow EmpowerID to provision EmpowerID people for new accounts discovered during the inventory process if they meet the Provision Rule specified by theCustom_Account_InventoryInboxGetAccountsToProvision SQL stored procedure.
- Default Provision Business Role – Set a default Business Role to assign people if none is specified.
- Default Provision Location – Set a default Location to assign people if none is specified.
- Allow Business Role and Location Re-Evaluation – Toggle if you have multiple account stores to manage and want to specify a priority for each.
- Business Role and Location Re-Evaluation Order – Enter a number to specify the priority of the account store for determining the Business Roles and Locations to assign to a Person. Account Stores with a higher value take precedence.
- Recertify All Group Changes – Toggle to allow EmpowerID to generate recertification review tasks for all changes in ServiceNow Groups.
- When you have finished editing, click Save.
To add local Windows servers via the Management Console
- Log in to the EmpowerID Management Console as an administrator.
- Click the application icon and select Configuration Manager from the menu.
- In Configuration Manager, select the Account Stores node and then click the Add New button above the grid.
- Click the Add New button above the grid.
- In the Add New Security Boundary window that opens, select the Local Windows Users Security Boundary type from the drop-down list and then click OK.
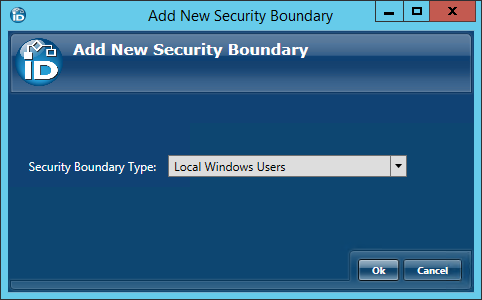
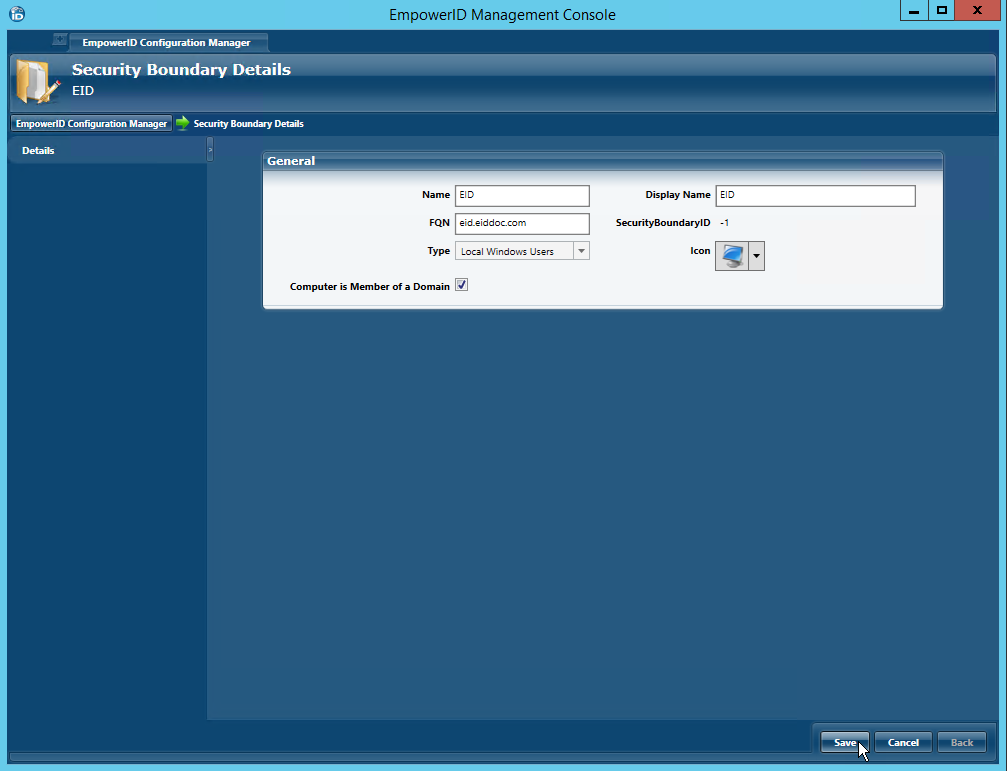
- In the Security Boundary Details window that opens, do the following:
- Type a name and display name for the local Windows server in the Name and Display Name fields, respectively.
- Type the fully-resolvable DNS for the server in the FQN field.
- Select Local Windows Users from the Type drop-down. This is the default selection.
If the server is a member of a domain to which EmpowerID has inventoried, select Computer is Member of a Domain. This tells EmpowerID to not create a new computer object for the local users server, but to link it to the inventoried domain computer.
If the server does not belong to an inventoried domain, leave Computer is Member of a Domain deselected. This tells EmpowerID to create a new computer object for the server, which allows the server to be visible in the EmpowerID user interfaces.
- Click Save.
- Back in the main Configuration Manager screen, locate the Local Windows account store you just created and double-click it or right-click it and select Edit from the context menu.
This opens the Account Store Details screen for the local Windows users server. You use this screen to configure EmpowerID settings for account store.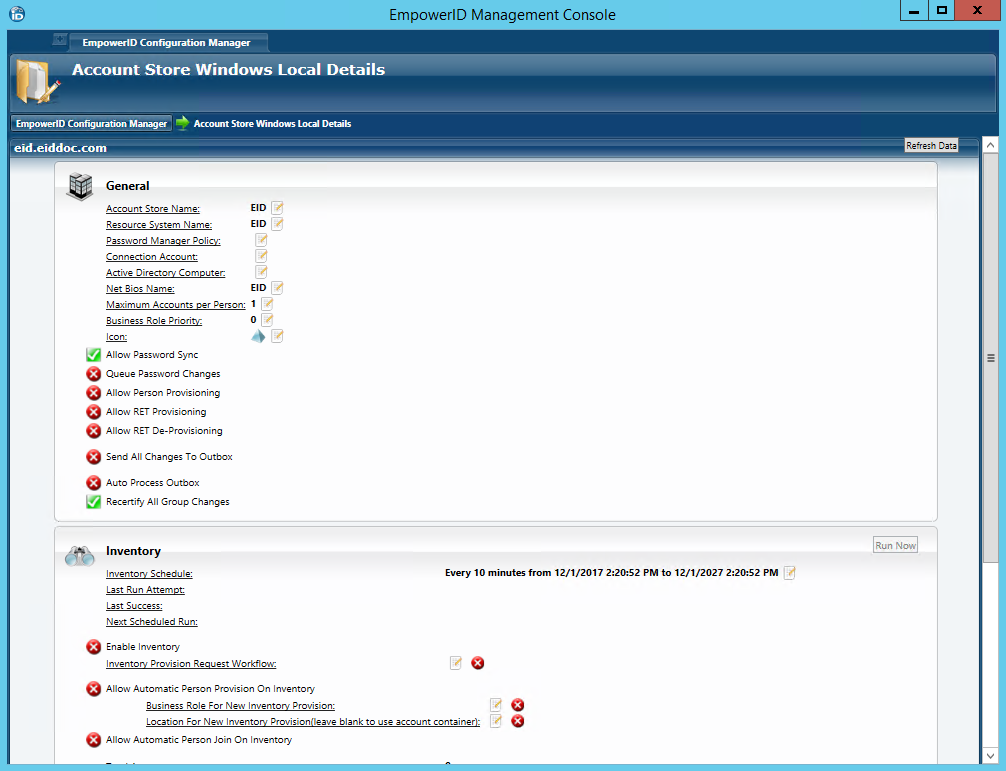
- The Net Bios Name configured should match with that of the local Windows server.
To configure the Local Windows server account store via the Management Console
Before configuring EmpowerID to manage the account store, you should determine whether you want to apply any provisioning policies to be applied to the local users inventoried from the server. If you do, as a best practice you should create those policies before inventorying the server. For more information on provisioning policies, see Overview of Resource Entitlements.
- In the General pane of the Account Store Details tab, click the Edit
 button to the right of Connection Account.
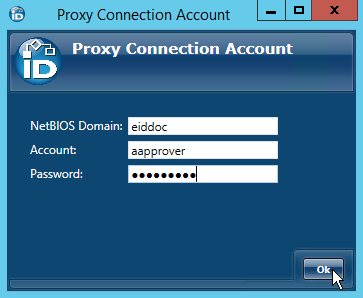
button to the right of Connection Account. - In the Proxy Connection Account window that appears, do the following:
- Type the net bios for the server in the NetBios Domain field.
- Type name of a user account with local admin privileges on the server. This user account can be either a domain user account or a local user account.
- Type the password for the account in the Password field.
- Click Ok to close the Proxy Connection Account window.
If you selected Computer is Member of Domain when you created the connection earlier, you will see a field for Active Directory Computer. If this is the case, click the Edit
 button to the right of Active Directory Computer.
button to the right of Active Directory Computer. If the computer does not belong to an inventoried domain, skip to step 5.
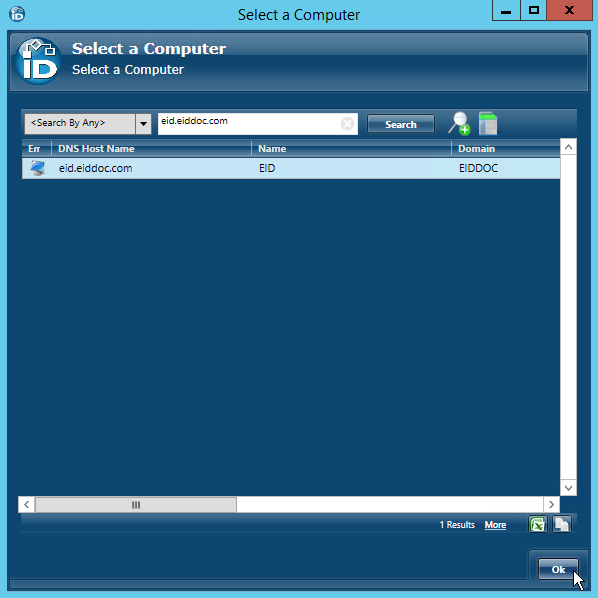
In the Select a Computer window that appears, search for and select the appropriate domain computer and then click OK. This tells EmpowerID that the domain computer has local users and groups that need to be inventoried as well as the domain users and groups.
Please note that the selected computer must belong to an Active Directory domain that EmpowerID is already inventorying or an error will occur when you turn on inventory. For information on connecting to Active Directory, see Connecting EmpowerID to Active Directory.
- Back in the General pane of the Account Store Details screen, leave Allow Person Provisioning set to false (red sphere). This is a recommended setting that keeps Person objects from being provisioned for any user accounts discovered during inventory.

- Select or deselect Allow RET Provisioning and Allow RET Deprovisioning based on whether you want any provisioning policies to be applied to the local users inventoried from the server.

- In the Inventory pane of the Account Store Details screen, toggle Enable Inventory from a red sphere to a green check to turn on inventory.
- No labels