You are viewing an earlier version of the admin guide. For the latest version, please visit EmpowerID Admin Guide v7.211.0.0.
Overview of EmpowerID Web Access Management
Phillip Hanegan
Patrick Parker
- Anonymous
Web Access Management (WAM) is a web-centric Identity Management strategy that focuses on securing enterprise resources accessible to Internet users. The key principles of WAM include:
- enforcement of corporate security policies,
- prevention of unauthorized access to enterprise resources, and
- the enablement of Web single sign-on (SSO) for simpler access to cross-domain resources.
WAM implementations typically realize these by enacting authentication and access control policies that funnel all Web application users through a single security gate that makes decisions about the users and enforces those decisions. In WAM terminology, this security gate is the Policy Decision Point (PDP). The PDP decides what users can or cannot do based on the information it reads from a Policy Information Point (PIP). Administrators and other delegated users write and manage the PIP through a console known as a Policy Administration Point (PAP). A Policy Enforcement Point (PEP) enforces PDP decisions.
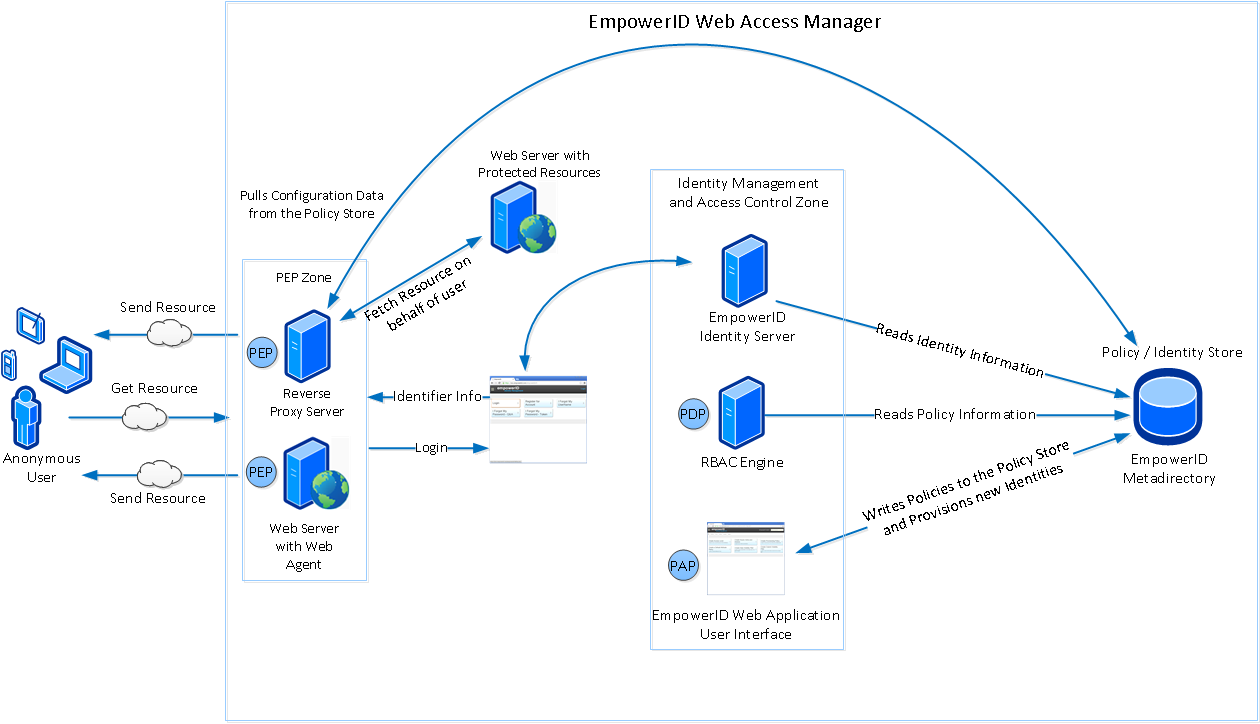
Components of the EmpowerID Web Access Management Platform
The EmpowerID Web Access Management system is an extension of EmpowerID that integrates seamlessly with all EmpowerID facilities, including:
- the Identity Warehouse,
- RBAC Engine,
- SSO Connection framework, and
- workflow automation services.
All of these work together to enable organizations with Web-based resources to leverage EmpowerID for the same end-to-end level of security they rely on for their directory-based resources. Everything from password management to on-demand identity provisioning to tight access controls and SSO capabilities for WAM users is included with EmpowerID. There is no need for separate plug-ins or other applications.
EmpowerID Web Interface
The interface of the EmpowerID Web Application serves as the Policy Administrative Point for EmpowerID Web Access Manager, providing functionality to configure and manage the policies and identities within your infrastructure. From here, administrators, managers, and other delegated people can provision and terminate users, create policies, assign roles and define who can do what with a resource.
Identity and Authentication Services
In Web Access Management, EmpowerID serves as an Identity Provider on behalf of a protected Web application. This means that users must have an identity that EmpowerID can vouch for before they can access a protected resource. At the most basic level, users must have an EmpowerID Person, as it is the object used in conjunction with policy to determine what a person can or cannot do with a resource.
EmpowerID's Identity Services are extremely flexible. You can configure them as an authentication hub that supports trusted relationships with all major Identity Providers using industry-standard protocols like SAML, WS-Federation, OpenID Connect, and OAuth. In this way organizations can allow users with oft-used identities supplied by entities outside of their realm, such as Google, Facebook, or Twitter, among others, to access resources using a familiar login. The only prerequisite is those outside entities must be trusted by EmpowerID and those identities must be linked to an EmpowerID Person. Web applications themselves only need to trust EmpowerID; EmpowerID takes care of the rest.
In addition, EmpowerID allows organizations to step up their authentication requirements by providing the facilities for multi-factor authentication to support scenarios where more stringent security requirements must be met. For example, if certain pages contain material that is more sensitive than others, organizations can require users accessing those pages to verify their identities with another set of proofs. Multi-factor authentication options include device authentication, one-time passwords sent to mobile phones, knowledge-based authentication (Q&A), and a standards-compliant OAuth server for issuing hardware or software one-time password tokens.
EmpowerID Identity Warehouse
The EmpowerID Identity Warehouse serves as the Policy Information Point for EmpowerID Web Access Manager. It is a multi-tenanted directory service that stores the relationship of a Person to the accounts they own for both traditional identity management and single sign-on.The EmpowerID Identity Warehouse stores each identity, role, policy, and resource that comprises an EmpowerID deployment as an managed object within a corresponding table in the Identity Warehouse.
The Identity Warehouse is a key component in any SSO solution architecture, enabling organizations to house external identities without compromising internal AD security. External users can securely authenticate against the EmpowerID Identity Warehouse using single or multi-factor authentication and gain access to only the applications you want to grant to them. The Identity Warehouse provides full self-service and delegated administration capabilities that allow end users to manage their passwords and identity associations from the EmpowerID Web application user interface.
EmpowerID RBAC /ABAC Engine
The EmpowerID RBAC / ABAC engine serves as the Policy Decision Point (PDP) for EmpowerID Web Access Manager, providing real-time services for evaluating and enforcing security policies for all resources protected by EmpowerID. The engine uses a number of EmpowerID Jobs and processes to continuously monitor an environment, tracking resources, identities, and policies to ensure users access only those resources to which they are entitled. The RBAC /ABAC engine constantly evaluates this "resultant access" information so that user access levels always match policy requirements. If a user is placed in a role that no longer qualifies that user for access to a given protected resource, the RBAC engine pulls that information from the Identity Warehouse and removes the access right from the user the next time RBAC recalculation occurs
EmpowerID Application Gateway
A proxy server is a machine that sits between clients and servers, intercepting traffic between the two. Proxies are generally categorized as forward proxies and reverse proxies. A forward proxy sits closer to the client, intercepting outbound traffic, and usually requires some type of configuration on the client side to work. A reverse proxy is a proxy that sits closer to the server and acts on behalf of that server, often assuming its name and IP address in order to intercept HTTP requests directed toward that server. Clients have no direct knowledge of reverse proxies. When a transaction occurs between the two, the client thinks it is interacting directly with the server itself, not the proxy.
The EmpowerID Application Gateway is EmpowerID's implementation of a reverse proxy. Built as KONG plug-ins, the EmpowerID Application Gateway is the perfect solution for enterprises needing access control for highly visited sites. The EmpowerID Application Gateway sits in the DMZ between clients and servers, acting as the Policy Enforcement Point (PEP), intercepting all HTTP traffic directed toward those servers. It may also act as a key component of a containerized infrastructure running as a "side car" Docker container. If the HTTP request represents a request for a protected resource (in the form of a URL), the EmpowerID Application Gateway redirects the user to the EmpowerID Login page, where users must authenticate themselves before receiving authorization to access the requested resource. If users successfully authenticate and have the delegations for the resource, the EmpowerID Application Gateway retrieves the resource on their behalf and serves it to them. In this case, users never interact directly with the server. Users who fail to authenticate, or users who have authenticated but do not have the necessary delegations for the requested resource, are denied access. If the HTTP request does not represent a request for a protected resource, the EmpowerID Application Gateway fetches the resource and delivers it to the user without requiring authentication.
EmpowerID Web Agent
The EmpowerID Web Agent is used in systems where resources need to be protected, but exposing the Web server that serves up those resources to HTTP traffic from external users is not an issue. In this case, the EmpowerID Web Agent is deployed against that server instead of the EmpowerID Application Gateway.
The Web Agent is an HTTP module that you can plug into the authentication pipeline in IIS for a .NET application. This allows organizations to load the agent in their Web applications so that each request for authentication against those Web applications calls the code within the EmpowerID Agent to determine whether the user is authenticated to EmpowerID. If the user is not authenticated, the user is directed to the EmpowerID Login page where she must provide her credentials and be authenticated by the EmpowerID IdP to access the application serviced by the EmpowerID Web Agent. After the user successfully authenticates, EmpowerID passes the credentials for that user to the application. The EmpowerID Web Agent does not determine what the user can or cannot do in the application; that is determined by the application itself.
You can configure the Web Agent for two different authentication modes: Reverse Proxy mode and SAML mode. Depending on which mode is used, the mechanism for retrieving the identity of users differs. In Reverse Proxy mode, identity information is passed to the application via an HTTP variable set in the HTTP header, eid_user. This variable contains the user's EmpowerID login name. When configured for Reverse Proxy mode, the agent assumes that a trusted reverse proxy is making the request to the Web application and has set the identity in the HTTP header variable. In SAML mode, the agent reads the SAML assertion generated by the EmpowerID IdP and pulls out the Name Identifier from that assertion and passes it to the application.
The Web Agent can be set for either forms-based or claims-based authentication. These modes determine the identity type used by the .NET Web application being protected, enabling EmpowerID to run the appropriate code to set the identity of the user. Once users authenticate, the next time they try to access the application within the same session, the agent passes the identity information to the application. There is no need to authenticate a second time.
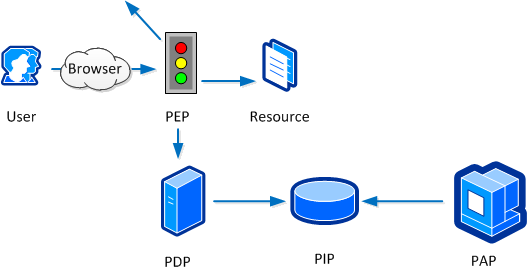
WAM Process Flow
The following image provides an overview of the flow that occurs in EmpowerID's Web Access Management system. In the image, an anonymous user attempts to access a protected Web resource. Because this resource is protected by EmpowerID and the current user is anonymous, the EmpowerID Application Gateway or EmpowerID Web agent (depending on the method used for the resource) intercepts the request to enforce the security policy for the resource. The user's browser redirects to the EmpowerID Login page, where the user must submit credentials for the process to continue.
Depending on how your SSO Connector framework is setup, users can choose to authenticate with credentials from any accepted third-party identity providers (IdP), such as Google, Facebook, or Twitter. (The user must have an EmpowerID Person with an account linked to the third-party IdP being used.) EmpowerID then checks those credentials against the EmpowerID Identity Warehouse to verify the identity of the user. If authentication is successful, identifier information for the user is returned to the calling application (EmpowerID Application Gateway or EmpowerID Web Agent), where it is processed and used to either allow or deny access based on the delegations associated with the user.