| Div | ||
|---|---|---|
| ||
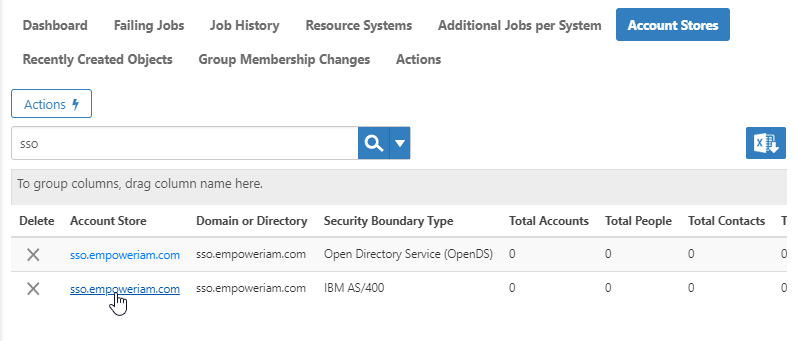
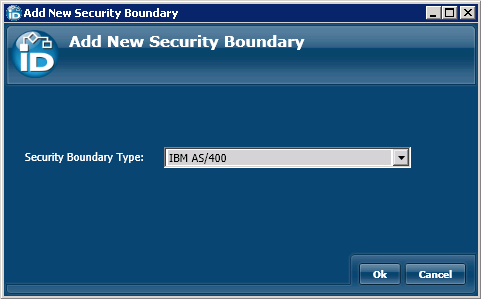
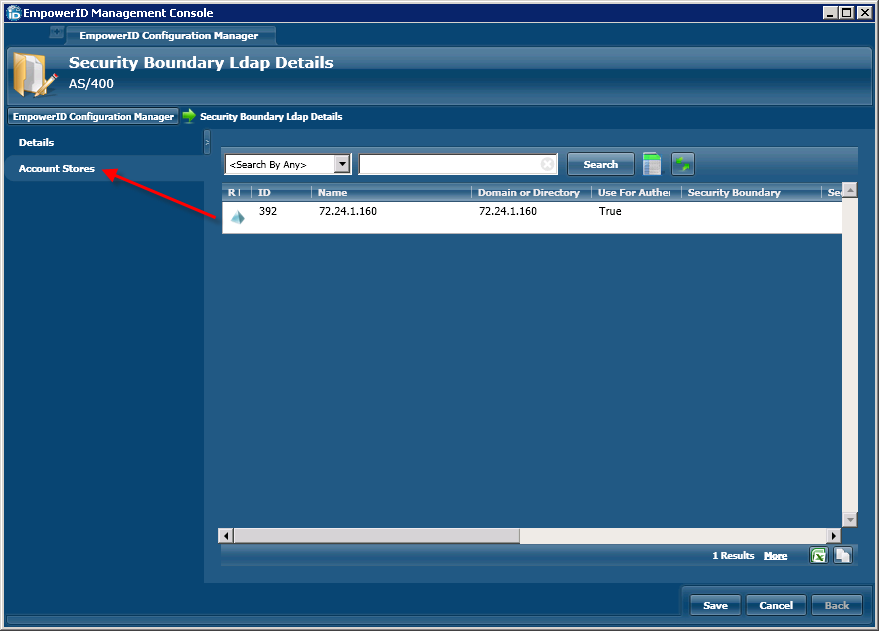
/wiki/spaces/E2D/pages/29982926 / Installation and Configuration / Connecting to Directory Systems / Current: Connecting to IBM AS/400 |
...
...
...
Selection of a specific location overrides the default logic that assigns the AS/400 OU of the user object as the primary location for the new person.
...
Enabling this function is not recommended in most cases as it removes the ability to manage groups in the directory. A consequence of this is that if a user account is removed from a directory group, EmpowerID puts the account back in the group.
...
| Wiki Markup |
|---|
\\ |
...
| title | Group Membership Reconciliation Pane |
|---|
Use this pane to enable or disable and schedule group membership reconciliation for the domain. This process ensures that the domain local groups used to grant native AS/400 permissions, such as read or write access for the group member attribute, are created in EmpowerID and granted the proper native permissions.
Among the available Resource Enforcement Types are the following:
- No Action - No rights enforcement action occurs.
- Projection with No Enforcement - Changes to rights within EmpowerID occur only within EmpowerID; they are not passed on to the native environment.
- Projection with Enforcement - Changes to rights within EmpowerID occur within EmpowerID and are enforced within the native environment.
- Projection with Strict Enforcement - EmpowerID overrides any changes made in the native environment. All changes made must occur within EmpowerID to be accepted. Strict Enforcement only applies to Groups.
To set Rights Enforcement for Resource Role Groups, do the following:
...
Clicking the Run Now button immediately runs the Resource Role Group Membership Reconciliation process and adjusts the next run time to the Enforcement Schedule setting. You should not run the process until you have completed all configuration steps.
...
Once you have completed the configuration of your Account Store, you should:
...
...
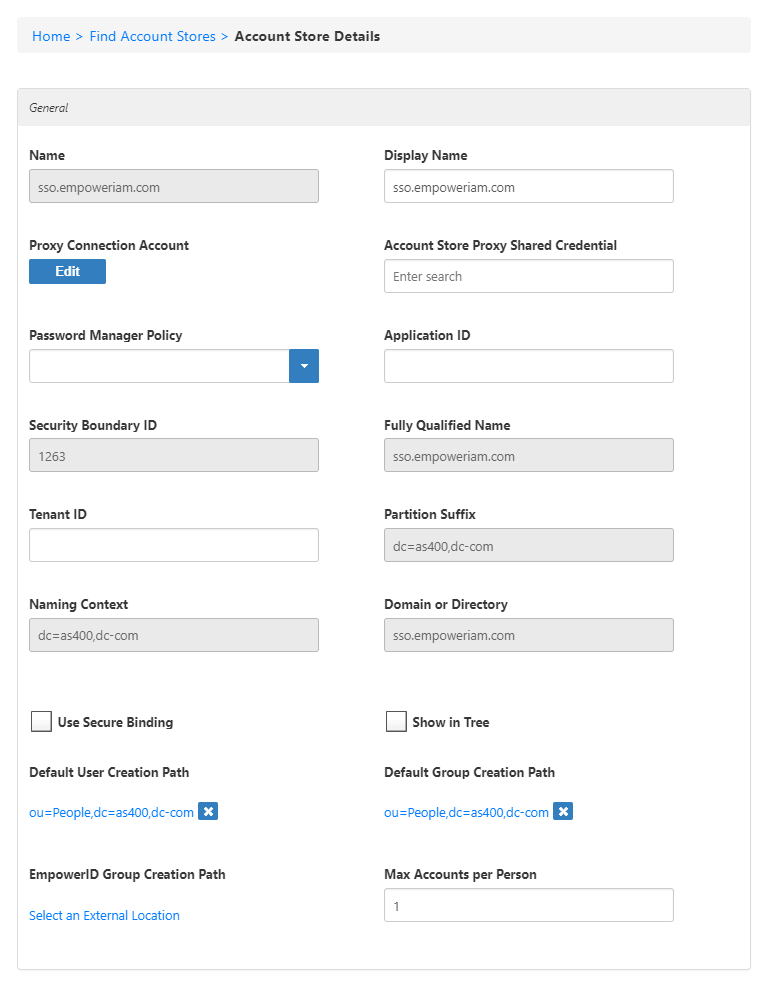
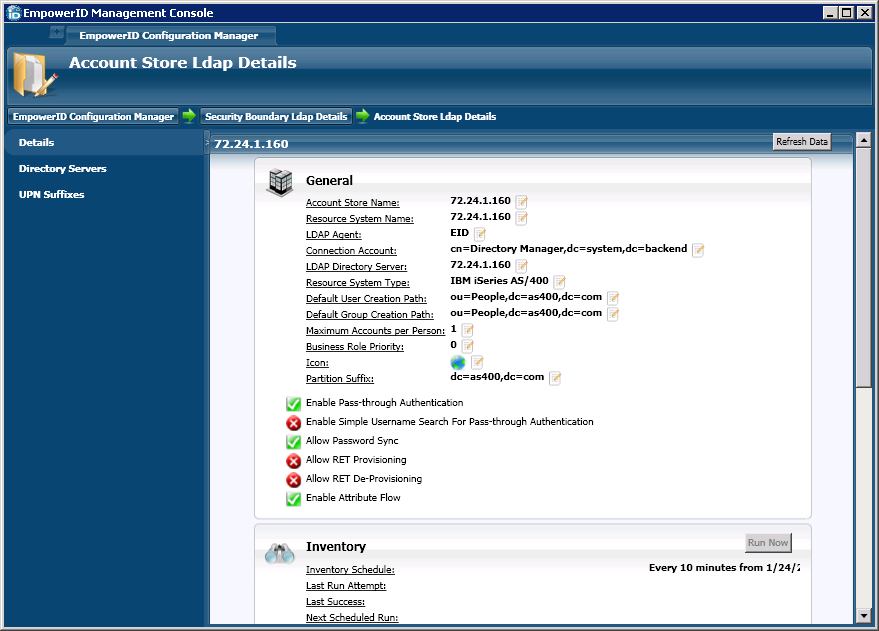
| title | General Pane |
|---|
Use this pane to set general information for the Account Store.
- Account Store Name - This is the name of the Account Store in question. This field is populated from the value supplied during the initial forest discovery process.
- Resource System Name - This is the name of the resource system that displays to users.
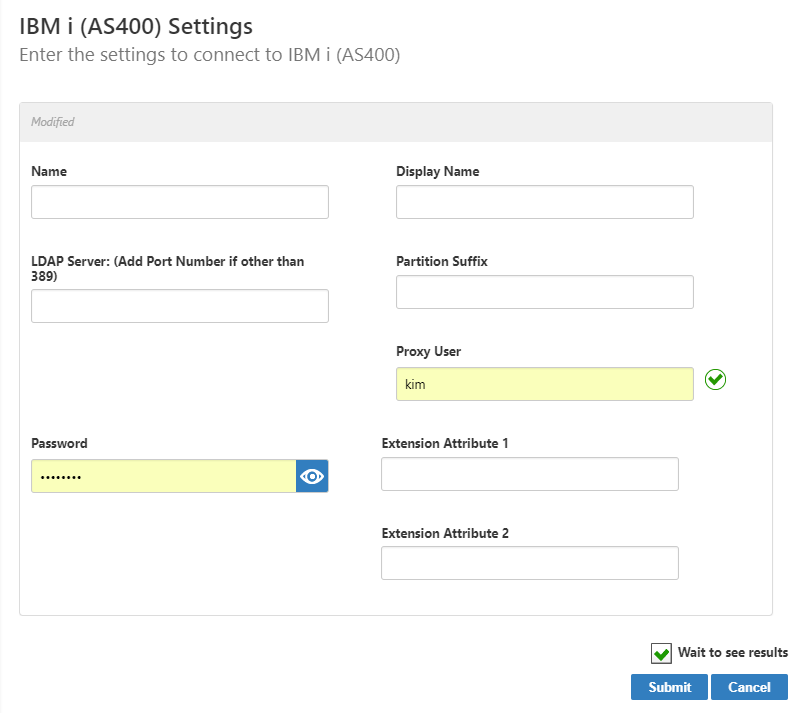
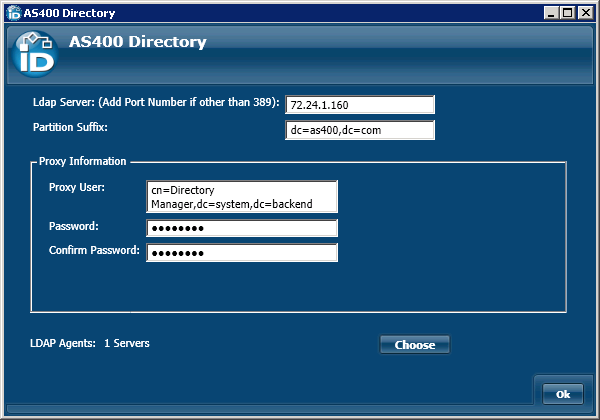
- LDAP Agent - This is the name of the server hosting the EmpowerID Agent. The EmpowerID Agent is the service that maintains all communication between any LDAP server (such as AS/400) and EmpowerID.
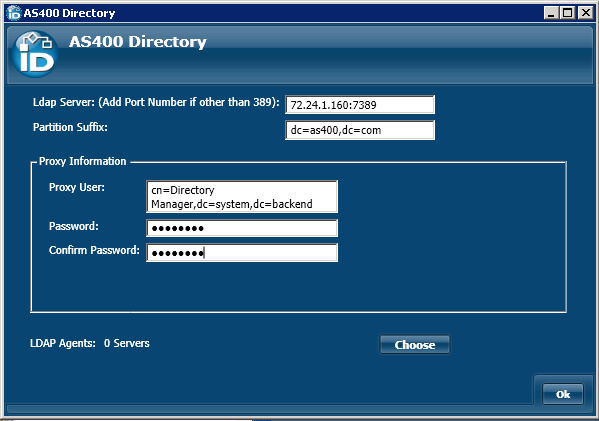
- Connection Account - This is the proxy account entered when scanning the forest. This account is used for inventorying, provisioning, making password resets, and enforcing permissions, so the information entered here must be an account with the appropriate administrative privileges.
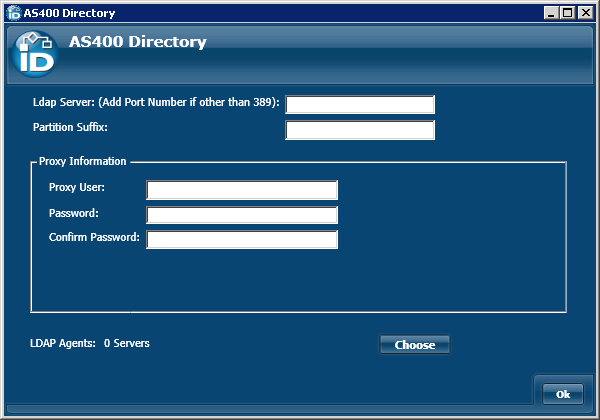
- LDAP Directory Server - This is the name of the server hosting the AS/400 directory and the port which EmpowerID monitors for changes. The values here were entered when you connected to the AS/400 directory.
- Resource System Type - This is the resource system type for the Account Store.
- Default User Creation Path - This is the creation location that is selected in a workflow process. If a change is needed here due to your environment, please contact Professional Services to make the change.
- Default Group Creation Path - This is the creation location that is selected in a workflow process. If a change is needed here due to your environment, please contact Professional Services to make the change.
- Maximum Accounts Per Person - Specifies the maximum number of user accounts from this domain that a person can have linked to them. This prevents the possibility of a runaway error caused by a wrongly configured Join rule. It is recommended that this value be set to 1 unless users will have more than 1 account and you wish them to be joined to the same person.
- Default User Creation Path - This is the creation location that is selected in a workflow process. If a change is needed here due to your environment, please contact Professional Services to make the change.
- Default Group Creation Path - This is the creation location that is selected in a workflow process. If a change is needed here due to your environment, please contact Professional Services to make the change.
- Maximum Accounts Per Person - Specifies the maximum number of user accounts from this domain that a person can have linked to them. This prevents the possibility of a runaway error caused by a wrongly configured Join rule. It is recommended that this value be set to 1 unless users will have more than 1 account and you wish them to be joined to the same person.
- Business Role Priority - This is an optional policy setting that can be used by provisioning workflows to determine which Account Store has priority when determining the roles and locations that should be assigned to a person. Account Stores with a higher value take precedence.
- Icon - This is the image icon that represents this account store in user interfaces.
- Partition Suffix - Allows the Account Store Partition Suffix to be specified.
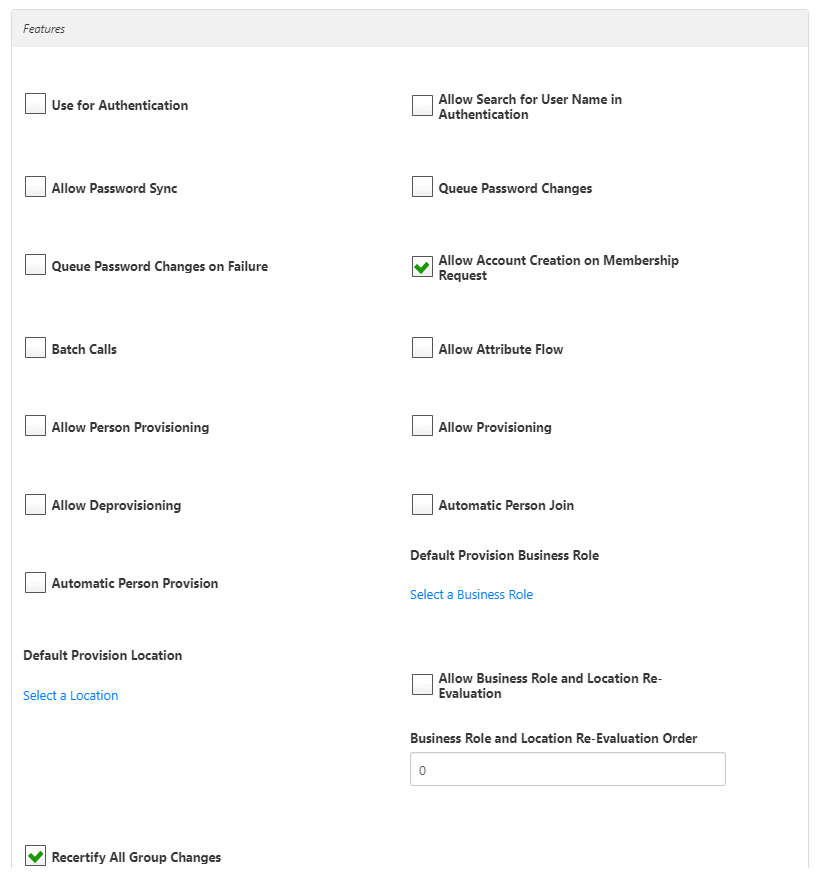
- Enable Pass-Through Authentication - This allows domain authentication to be used for logging in to EmpowerID. Unless Simple Search is enabled, the domain\username format needs to be used.
- Enable Simple Username Search for Pass-Through Authentication - Simple search works in conjunction with pass-through authentication to allow users to log in without specifying a domain name. When this is enabled, EmpowerID first checks to see if the user name entered exists within its metadirectory and if so attempts to authenticate as that user. If a matching logon name exists but the login fails, EmpowerID then searches through all Accounts Stores where simple username search is enabled to find the correct user name and password combination. Note: Simple search can cause long delays during the login process in environments with a large number of domains.
- Allow Password Sync - Enables or disables the synchronization of password changes to user accounts in the domain based on password changes for the owning person object or another account owned by the person. This setting does not prevent password changes by users running the reset user account password workflows.
- Allow RET Provisioning - If enabled, EmpowerID applies any Resource Entitlements policies to each person provisioned from an inventoried AWS account if those people are placed in a Business Role and Location that is targeted by a Resource Entitlement Policy.
- Allow RET De-Provisioning - Allows or disallows the Resource Entitlement Inbox process to auto de-provision accounts for this domain for users who still have RET policy-assigned user accounts, but no longer receive a policy that grants them a user account in the domain. De-provisioning only occurs if the de-provision action on the Resource Entitlement policy is set to De-Provision.
- Allow Create Account On Membership Request — Select to allow users without accounts to request group membership and automatically have an account created.
- Enable Attribute Flow - Allows or disallows attribute changes to flow between EmpowerID and the account store.
| Wiki Markup |
|---|
\\ |
...
| title | Inventory Pane |
|---|
Use this pane to enable or disable and set the inventory schedule for the domain. A description of the pane follows below.
...