/
Port Communication Requirements
You are viewing an earlier version of the admin guide. For the latest version, please visit EmpowerID Admin Guide v7.211.0.0.
Port Communication Requirements
Active Directory
For EmpowerID to communicate with Active Directory environments, the following ports must be open:
- 135/TCP RPC
- 137/UDP NetBIOS
- 138/UDP NetBIOS
- 139/TCP NetBIOS
- 389/TCP/UDP LDAP
- 636/TCP LDAP SSL
- 3268/TCP LDAP GC
- 3269/TCP LDAP GC SSL
- 53/TCP/UDP DNS
- 88/TCP/UDP Kerberos
- 445/TCP SMB
- 123/UDP NTP
Internal EmpowerID Communications
The EmpowerID Management Console Windows desktop client requires the following ports be open:
- HTTPS/TLS: port 443 TCP
EmpowerID server to server communications require the following ports be open:
- HTTPS/TLS: port 443 TCP
EmpowerID server to SQL Database communications require the following ports be open:
- Microsoft SQL Server: port 1433 TCP
The EmpowerID WAM/Reverse Proxy does not require any communication with the Microsoft SQL database. The Reverse Proxy retrieves all of its configuration data by calling the EmpowerID REST API on any front-end servers.
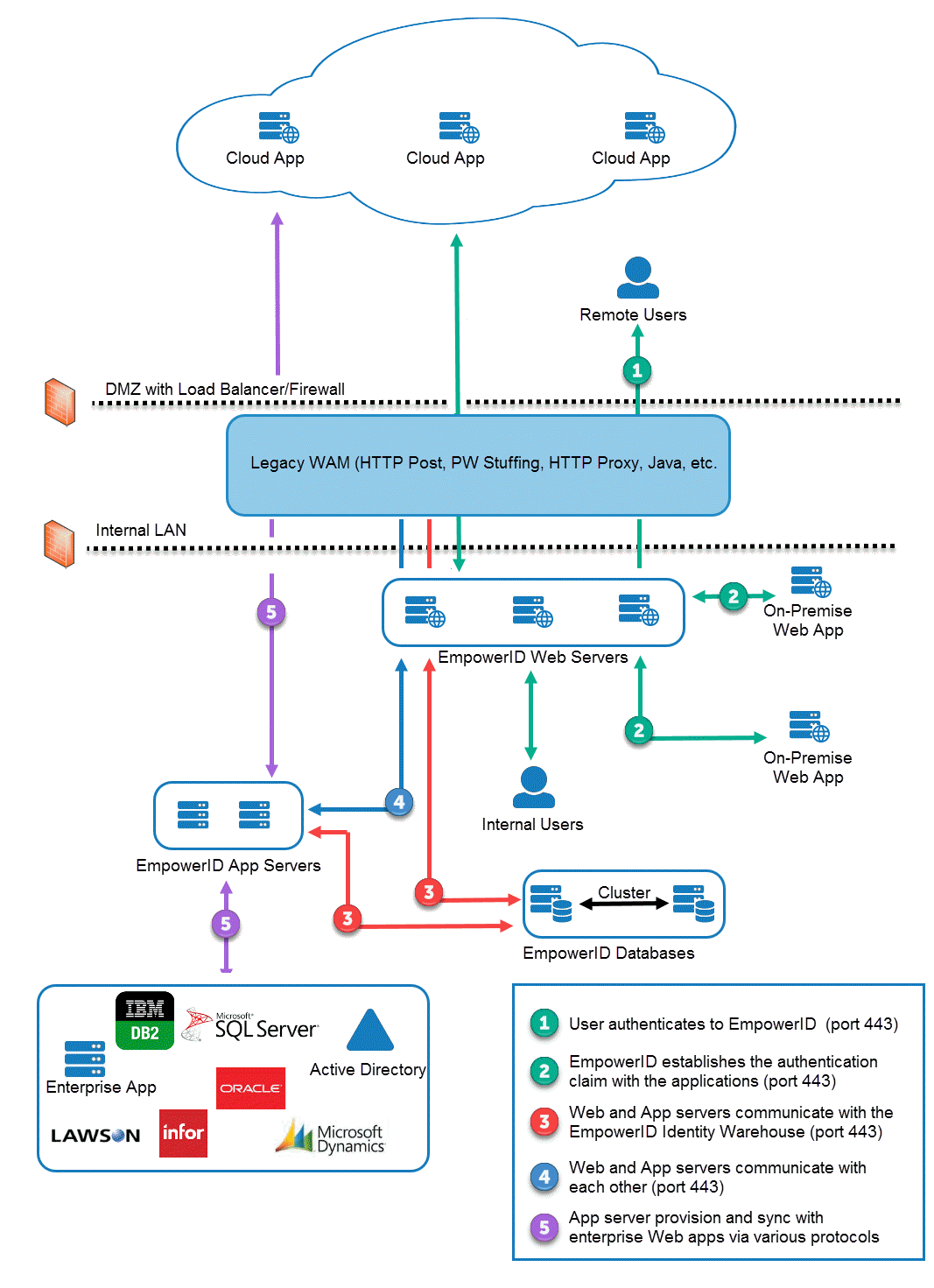
The below two images depict the EmpowerID Communications and Connectivity architecture. The first shows the architecture without EmpowerID WAM/Reverse Proxy, while the second shows the architecture with EmpowerID WAM/Reverse Proxy.
Figure 1: EmpowerID Communications and Connectivity Architecture
Figure 2: EmpowerID Communications and Connectivity architecture with WAM/Reverse Proxy module
In addition to the above, for password resets you may need to open TDP/UDP 135, as well as all RPC dynamic ports. For more information, see the following Microsoft topics:
Related content
Service Account Requirements
Service Account Requirements
Read with this
Port Communication Requirements
Port Communication Requirements
More like this
Hardware Requirements and Sizing
Hardware Requirements and Sizing
Read with this
Port Communication Requirements
Port Communication Requirements
More like this
Port Communication Requirements
Port Communication Requirements
More like this
Port Communication Requirements
Port Communication Requirements
More like this