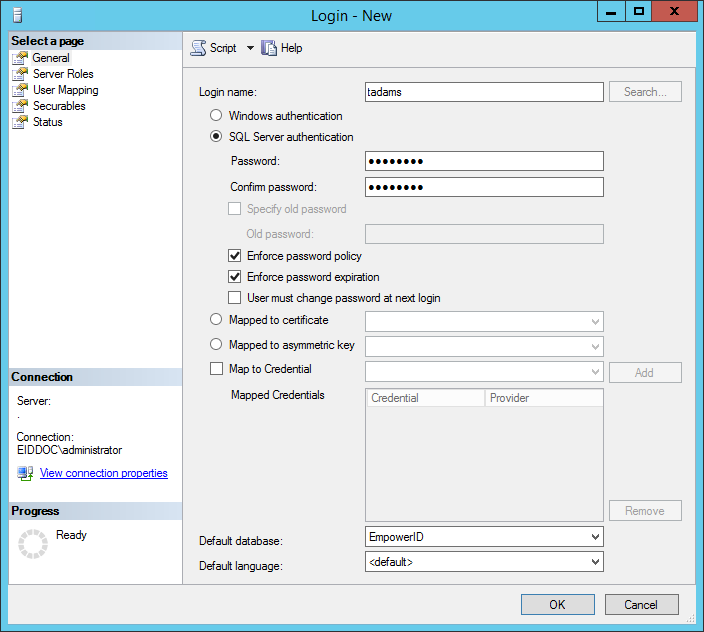
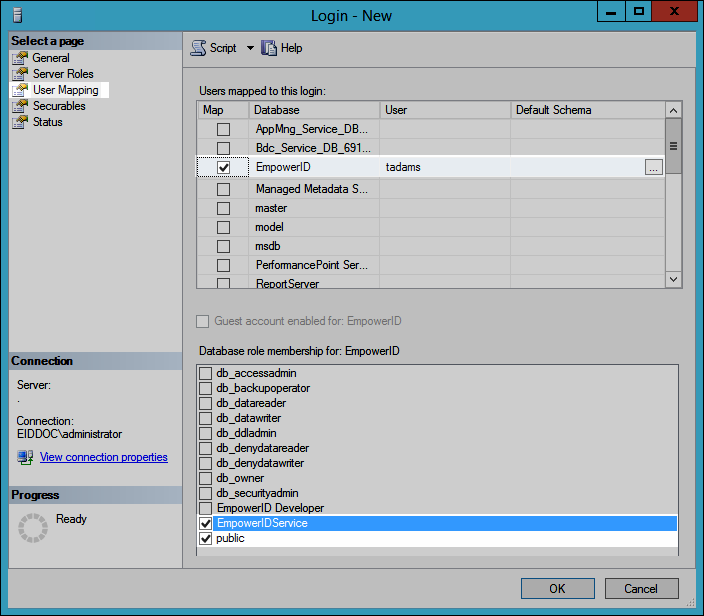
/
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
, multiple selections available,
Related content
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
More like this
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
More like this
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
More like this
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
More like this
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
More like this
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
Installing and Configuring the EmpowerID Virtual Directory Server on Linux
More like this