Adding Recertification Policies to Audits
In EmpowerID, an audit is a user-defined, logically named object for identifying or grouping recertification tasks and running the Recertification policies that generate those tasks. After creating an audit, you add Recertification policies to it to define what you want to audit. Then when the audit runs, it compiles those Recertification policies, creating the appropriate recertification tasks.
Prerequisites
Before you can add a specific Recertification policy to an audit, both the audit and the policy must exist in EmpowerID. If they do not, please see Creating Audit Recertification Policies and Creating and Configuring Audits for more information.
To add recertification policies to audits
- Log in to the EmpowerID Web application as an auditor or other person with the ability to configure audits.
- In the Navigation Sidebar, expand Compliance Management and click Audit Configuration.
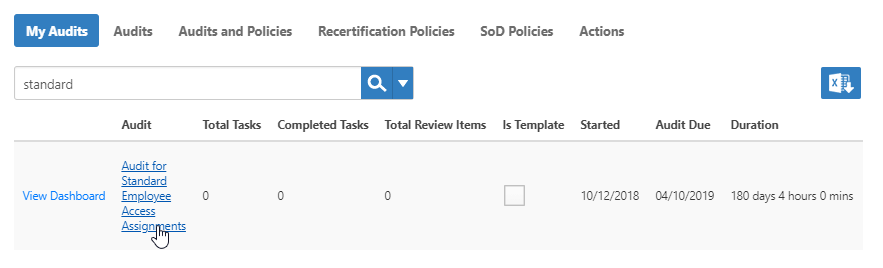
- Click the Audits tab and search for the audit to which you want to add a Recertification policy.
- Click the Audit link.
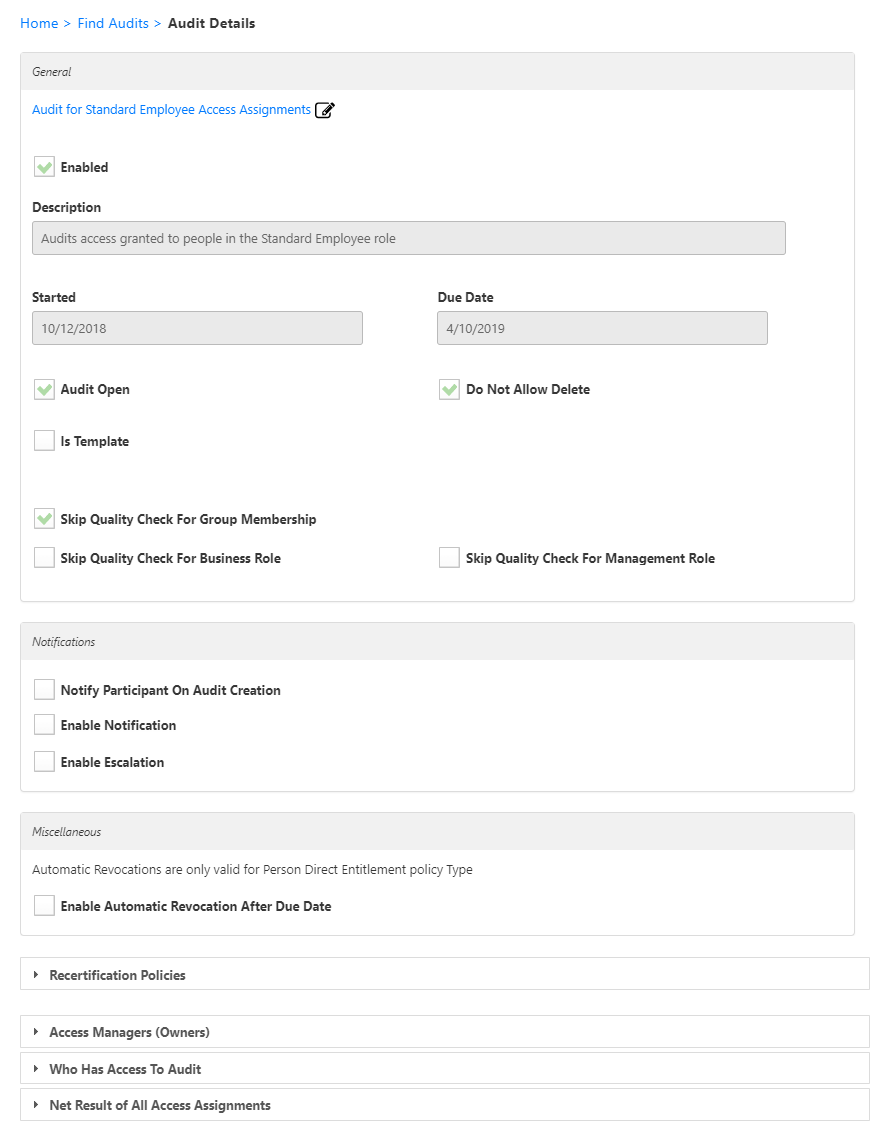
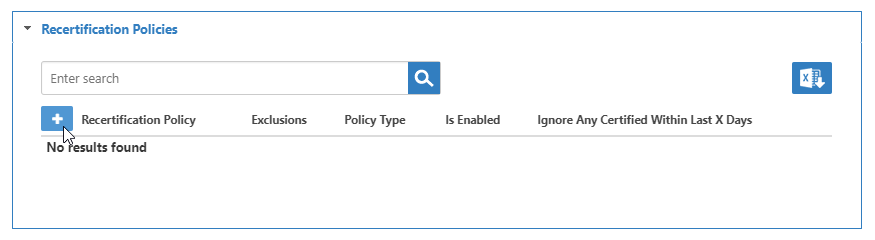
This opens the View One page for the Audit. View One pages allow you to view information about an object in EmpowerID and manage it as needed. - From the audit's View One page, expand the Recertification Policies accordion and click the Add New Recertification Policy (+) button in the Policy grid.
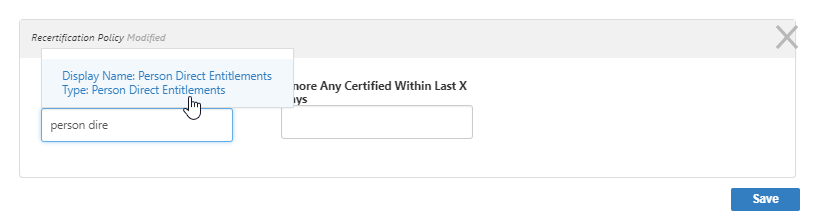
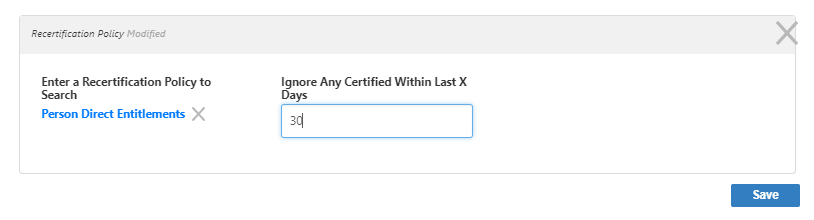
- In the Recertification Policy dialog that appears, type the name of the policy you want to add to the audit, and then click the tile for that policy.
Optionally, type a number in the Ignore Any Certified Within Last X Days field.
This is useful in situations where a previous audit closed before all recertification tasks it generated were completed. This way, managers only receive recertification tasks for any direct reports who were not certified in the last audit.
This setting does not completely exclude previously audited direct reports; it only excludes those access assignments that were re-certified within the specified day range. Thus, if a direct report gains access to a new resource, such as becoming the member of a new group, the audit generates a recertification task for that new membership.
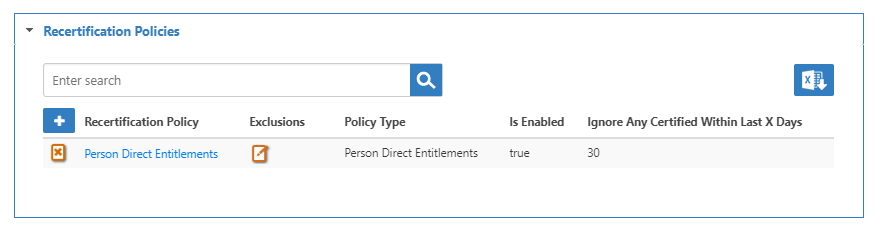
- Click Save to add the Recertification policy to the audit. The policy is added to the Recertification Policies grid.
To add exclusions to the Policy
Optionally, you can keep the audit from creating recertification tasks for certain access assignments that would normally be generated by the recertification policy.
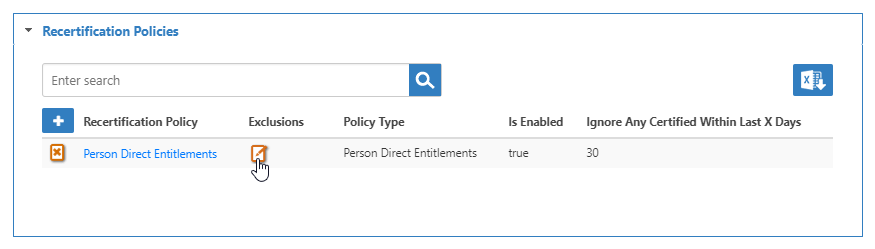
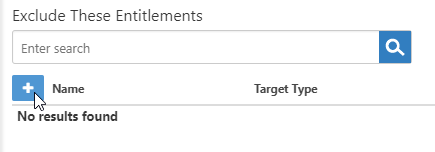
- On the Recertification Policy grid, click the Exclusions button for the policy.
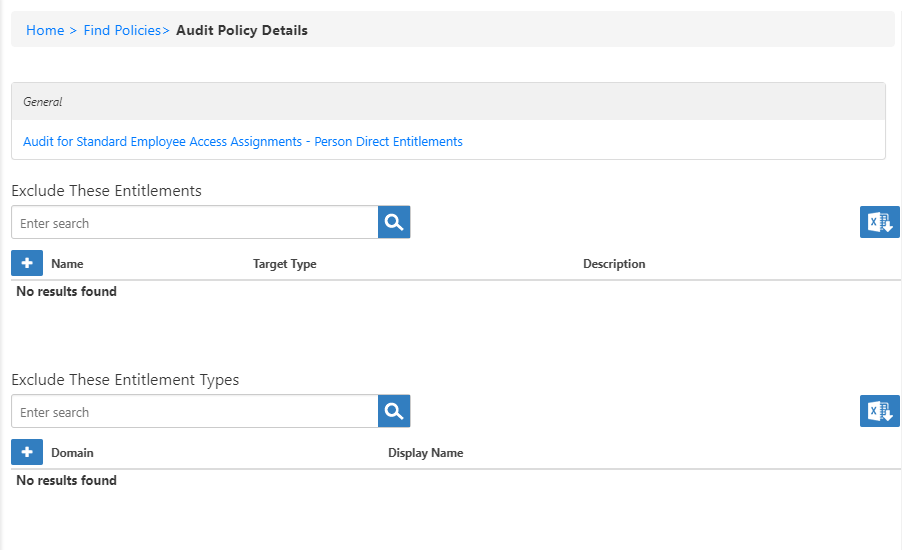
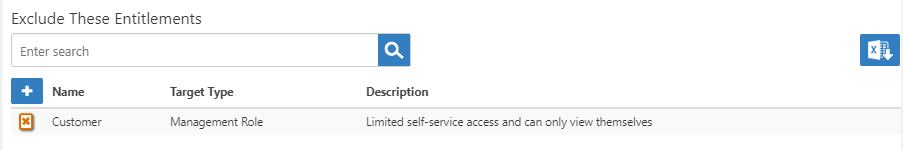
This opens a view with two grids: Exclude These Entitlements and Exclude These Entitlement Types. These grids allow you to exclude entitlements granted to specific actors, such as individual people or groups, as well as entitlement types, such as roles or groups that have no bearing for the audit. - To exclude a specific entitlement, in the Exclude These Entitlements grid, click the Add button.
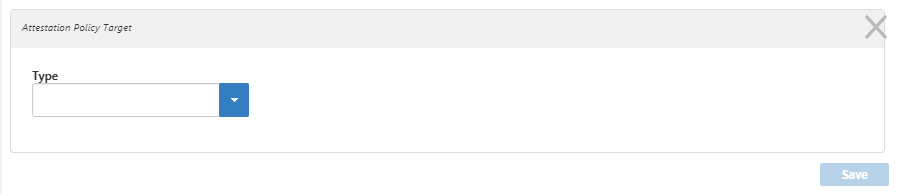
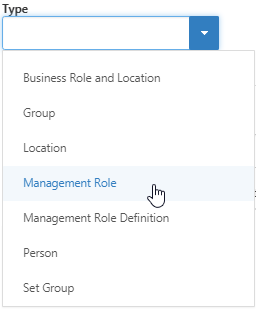
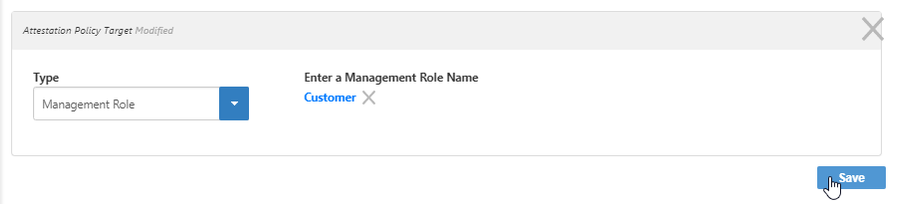
This opens the Attestation Policy Target dialog, where you can select the type of resource, such as Business Role and Location, and a specific object of that type, such as Sales Rep in Boston. - Select a target type from the Type drop-down, for example, Management Role.
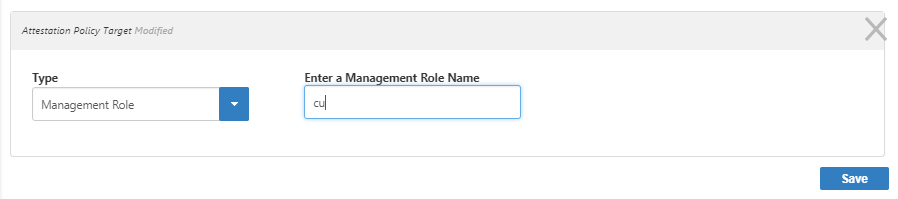
A box (or if you choose Business Role and Location, a pair of tree selectors) appears to the right. - Click in the box and press Enter for a list of available options, or type the name of the specific actor to exclude, in this case "customer," select the tile for the actor, and click Save.
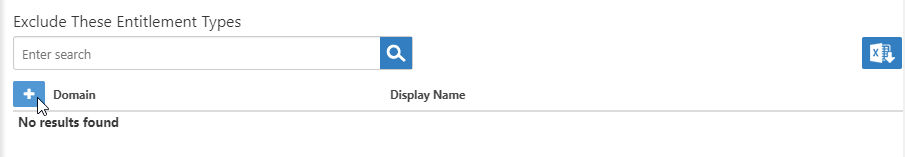
The Customer actor type is added to the grid of entitlements to exclude from this audit. - To exclude a type of entitlement, in the Exclude These Entitlement Types grid, click the Add button.
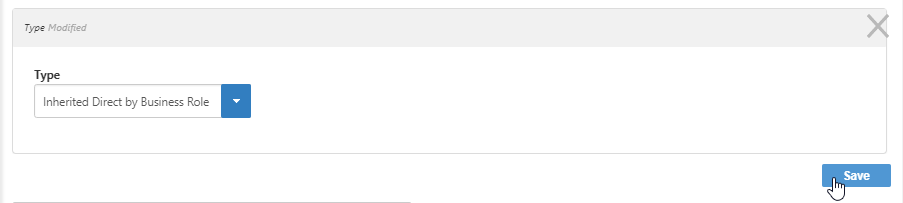
- Select a Type from the drop-down list. The following types are available:
- Business Role excludes business roles from the type of entitlements audited.
- Group Membership excludes group membership from the type of entitlements audited.
- Inherited Direct by Business Role excludes any access inherited directly from the person's business role from the type of entitlements audited.
- Inherited Direct by Management Role excludes any access inherited directly from the person's management role from the type of entitlements audited.
- Inherited Direct by Primary Business Role excludes any access inherited directly from the person's primary business role from the type of entitlements audited.
- Inherited Location based by Business Role excludes any location inherited from the person's business role from the type of entitlements audited.
- Inherited Location by Primary Business Role excludes any location inherited from the person's primary business role from the type of entitlements audited.
- Inherited Management Role by Primary Business Role excludes any management role inherited directly from the person's primary business role from the type of entitlements audited.
- Inherited Role Group Membership excludes any group membership inherited from the person's role from the type of entitlements audited.
- Management Role excludes management roles from the type of entitlements audited.
- Primary Business Role excludes primary business roles from the type of entitlements audited.
- Resource Role excludes resource roles from the type of entitlements audited.
- Role Group Membership excludes role group membership from the type of entitlements audited.
- Click Save.
The type is added to the grid of excluded entitlement types.
Once you have finished adding your Recertification policies to the audit, the next step is to generate the recertification tasks associated with the policies. You do this by compiling the audit. This is demonstrated in the Compiling Audits topic.